What’s new in XenMobile Server 10.11
XenMobile Server 10.11 (PDF Download)
Apple Volume Purchase Program migration to Apple Business Manager (ABM) and Apple School Manager (ASM)
Companies and institutions using the Apple Volume Purchase Program (VPP) must migrate to Apps and Books in the Apple Business Manager or Apple School Manager before December 1, 2019.
Before migrating VPP accounts in XenMobile, see this Apple support article.
If your organization or school only uses the Volume Purchase Program (VPP), you can enroll in ABM/ASM and then invite existing VPP Purchasers to your new ABM/ASM account. For ASM, navigate to https://school.apple.com. For ABM, navigate to https://business.apple.com.
To update your Volume Purchase (formerly VPP) account on XenMobile®:
-
In the XenMobile console, click the gear icon in the upper-right corner. The Settings page appears.
-
Click Volume Purchase. The Volume Purchase configuration page appears.
-
Make sure that your ABM or ASM account has the same app config as your previous VPP account.
-
In the ABM or ASM portal, download an updated token.
-
In the XenMobile console, do the following:
-
Edit the existing Volume Purchase account with the updated token info for that location.
-
Edit your ABM or ASM credentials. Don’t change the suffix.
-
Click Save twice.
-
Additional support for iOS 13
Important:
To prepare for device upgrades to iOS 12+: The Citrix VPN connection type in the VPN device policy for iOS doesn’t support iOS 12+. Delete your VPN device policy and create a VPN device policy with the Citrix SSO connection type.
The Citrix VPN connection continues to operate in previously deployed devices after you delete the VPN device policy. Your new VPN device policy configuration takes effect in XenMobile Server 10.11, during user enrollment.
XenMobile Server supports devices upgraded to iOS 13. The upgrade impacts your users as follows:
-
During enrollment, a few new iOS Setup Assistant Option screens appear. Apple added a new iOS Setup Assistant Option screens to iOS 13. The new options aren’t included in the Settings > Apple Device Enrollment Program (DEP) page in this version. As a result, you can’t configure XenMobile Server to skip those screens. Those pages appear to users on iOS 13 devices.
-
Some Restrictions device policy settings that were available on supervised or unsupervised devices for previous versions of iOS are available only on supervised devices for iOS 13+. The current XenMobile Server console tool tips don’t yet indicate that these settings are for supervised devices for iOS 13+ only.
- Allow hardware controls:
- FaceTime
- Installing apps
- Allow apps:
- iTunes Store
- Safari
- Safari > Autofill
- Network - Allow iCloud actions:
- iCloud documents & data
- Supervised only settings - Allow:
- Game Center > Add friends
- Game Center > Multiplayer gaming
- Media content - Allow:
- Explicit music, podcasts, and iTunes U material
- Allow hardware controls:
These restrictions apply as follows:
- If an iOS 12 (or lower) device is already enrolled in XenMobile Server and then upgrades to iOS 13, the preceding restrictions apply to unsupervised and supervised devices.
- If an unsupervised iOS 13+ device enrolls in XenMobile Server, the preceding restrictions apply only to supervised devices.
- If a supervised iOS 13+ device enrolls in XenMobile Server, the preceding restrictions apply only to supervised devices.
Requirements for trusted certificates in iOS 13 and macOS 15
Apple has new requirements for TLS server certificates. Verify that all certificates follow the new Apple requirements. See the Apple publication, https://support.apple.com/en-us/HT210176. For help with managing certificates, see Uploading certificates in XenMobile.
Upgrade from GCM to FCM
From April 10, 2018, Google deprecated Google Cloud Messaging (GCM). Google removed the GCM server and client APIs on May 29, 2019.
Important requirements:
- Upgrade to the latest version of XenMobile Server.
- Upgrade to the latest version of Secure Hub.
Google recommends upgrading to Firebase Cloud Messaging (FCM) right away to begin taking advantage of the new features available in FCM. For information from Google, see https://developers.google.com/cloud-messaging/faq and https://firebase.googleblog.com/2018/04/time-to-upgrade-from-gcm-to-fcm.html.
To continue support for push notifications to your Android devices: If you use GCM with XenMobile Server, migrate to FCM. Then, update XenMobile Server with the new FCM key available from the Firebase Cloud Messaging Console.
The following steps reflect the enrollment workflow when you use trusted certificates.
Upgrade steps:
- Follow the information from Google to upgrade from GCM to FCM.
- In the Firebase Cloud Messaging Console, copy your new FCM key. You’ll need it for the next step.
- In the XenMobile Server console, go to Settings > Firebase Cloud Messaging and configure your settings.
Devices switch over to FCM the next time they check in with XenMobile Server and do a policy refresh. To force Secure Hub to refresh policies: In the Secure Hub, go to Preferences > Device Information and tap Refresh Policy. For more information about configuring FCM, see Firebase Cloud Messaging.
Before you upgrade to XenMobile 10.11 (on-premises)
Some systems requirements changed. For information, see System requirements and compatibility and XenMobile compatibility.
-
Update your Citrix License Server to 11.15 or later before updating to the latest version of XenMobile Server 10.11.
The latest version of XenMobile requires Citrix License Server 11.15 (minimum version).
Note:
If you want to use your own license for the Preview, know that the Customer Success Services date (previously, Subscription Advantage date) in XenMobile 10.11 is April 9, 2019. The Customer Success Services date on your Citrix license must be later than this date.
You can view the date next to the license in the License Server. If you connect the latest version of XenMobile to an older License Server environment, the connectivity check fails and you can’t configure the License Server.
To renew the date on your license, download the latest license file from the Citrix Portal and upload the file to the Licensing Server. For more information, see Customer Success Services.
-
For a clustered environment: iOS policy and app deployments to devices running iOS 11 and later have the following requirements. If Citrix Gateway is configured for SSL persistence, you must open port 80 on all XenMobile Server nodes.
-
If the virtual machine running the XenMobile Server to be upgraded has less than 4 GB of RAM, increase the RAM to at least 4 GB. Keep in mind that the recommended minimum RAM is 8 GB for production environments.
-
Recommendation: Before you install a XenMobile update, use the functionality in your VM to take a snapshot of your system. Also, back up your system configuration database. If you experience issues during an upgrade, complete backups enable you to recover.
To upgrade
You can directly upgrade to XenMobile 10.11 from XenMobile 10.10.x or 10.9.x. To do the upgrade, download the latest binary available: Go to https://www.citrix.com/downloads. Navigate to Citrix Endpoint Management (and Citrix XenMobile Server) > XenMobile Server (on-premises) > Product Software > XenMobile Server 10. On the tile for the XenMobile Server software for your hypervisor, click Download File.
To upload the upgrade, use the Release Management page in the XenMobile console. For more information, see To upgrade using the Release Management page.
After you upgrade
After you upgrade to XenMobile 10.11 (on-premises):
If functionality involving outgoing connections stop working, and you haven’t changed your connections configuration, check the XenMobile Server log for errors such as the following: “Unable to connect to the VPP Server: Host name ‘192.0.2.0’ does not match the certificate subject provided by the peer”.
The certificate validation error indicates that you need to disable host name verification on XenMobile Server. By default, host name verification is enabled on outgoing connections except for the Microsoft PKI server. If host name verification breaks your deployment, change the server property disable.hostname.verification to true. The default value of this property is false.
New and updated device policy settings for Android Enterprise devices
Samsung Knox and Android Enterprise policy unification. For Android Enterprise devices running Samsung Knox 3.0 or later and Android 8.0 or later: Knox and Android Enterprise are combined into a unified device and Profile Management solution. Configure Knox settings on the Android Enterprise page of the following device policies:
- OS Update device policy. Includes settings for Samsung Enterprise FOTA updates.
- Passcode device policy.
- Samsung MDM license key device policy. Configures the Knox license key.
- Restrictions device policy settings.
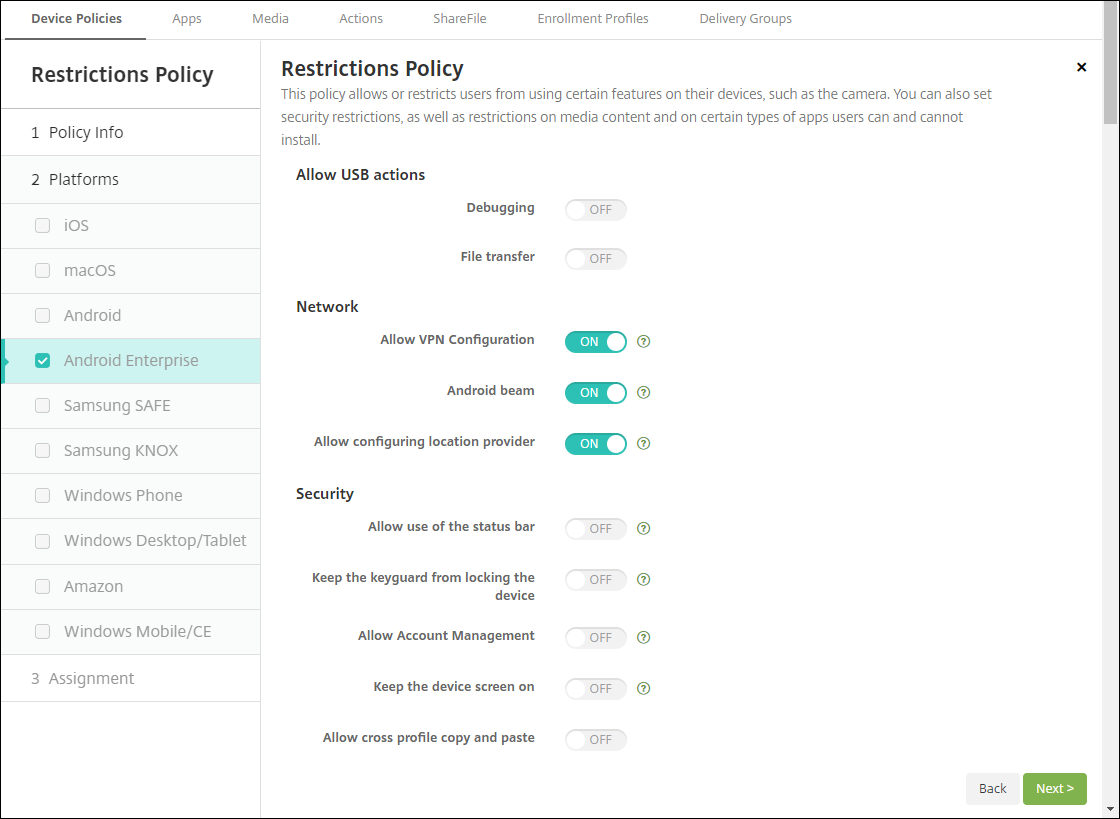
App inventory device policy for Android Enterprise. You can now collect an inventory of the Android Enterprise apps on managed devices. See App inventory device policy.
Access all Google Play apps in the managed Google Play store. The Access all apps in the managed Google Play store server property makes all apps from the public Google Play store accessible from the managed Google Play store. Setting this property to true allows the public Google Play store apps for all Android Enterprise users. Administrators can then use the Restrictions device policy to control access to these apps.
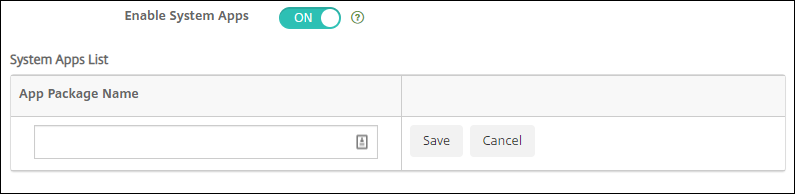
Enable system apps on Android Enterprise devices. To allow users to run pre-installed system apps in the Android Enterprise work profile mode or fully managed mode, configure the Restrictions device policy. That configuration grants the user access to default device apps, such as camera, gallery, and others. To restrict access to a particular app, set app permissions using the Android Enterprise app permissions device policy.
Support for Android Enterprise dedicated devices. XenMobile now supports the management of dedicated devices, previously called corporate owned single use (COSU) devices.
Dedicated Android Enterprise devices are fully managed devices that are dedicated to fulfill a single use case. You restrict these devices to one app or small set of apps required to do the tasks needed for this use case. You also prevent users from enabling other apps or doing other actions on the device.
For information about provisioning Android Enterprise devices, see Provisioning dedicated Android Enterprise devices.
Renamed policy. To align with Google terminology, the Android Enterprise app restriction device policy is now called Managed configurations device policy. See Managed configurations device policy.
Lock and reset password for Android Enterprise
XenMobile now supports the Lock and Reset password security action for Android Enterprise devices. Those devices must be enrolled in work profile mode running Android 8.0 and greater.
- The passcode sent locks the work profile. The device isn’t locked.
- If no passcode is sent or the passcode sent doesn’t meet passcode requirements:
- And no passcode is already set on the work profile, the device is locked.
- And a passcode is already set on the work profile. The work profile is locked but the device isn’t locked.
For more information on the lock and reset password security actions, see Security actions.
New Restrictions device policy settings for iOS or macOS
- Unmanaged apps read managed contacts: Optional. Only available if Documents from managed apps in unmanaged apps is disabled. If this policy is enabled, unmanaged apps can read data from managed accounts’ contacts. Default is Off. Available from iOS 12.
- Managed apps write unmanaged contacts: Optional. If enabled, allow managed apps to write contacts to unmanaged accounts’ contacts. If Documents from managed apps in unmanaged apps is enabled, this restriction has no effect. Default is Off. Available from iOS 12.
- Password AutoFill: Optional. If disabled, users can’t use the AutoFill Passwords or Automatic Strong Passwords features. Default is On. Available from iOS 12 and macOS 10.14.
- Password proximity requests: Optional. If disabled, users’ devices don’t request passwords from nearby devices. Default is On. Available from iOS 12 and macOS 10.14.
- Password Sharing: Optional. If disabled, users can’t share their passwords using the AirDrop Passwords feature. Default is On. Available from iOS 12 and macOS 10.14.
- Force automatic date and time: Supervised. If enabled, users can’t disable the option General > Date & Time > Set Automatically. Default is Off. Available from iOS 12.
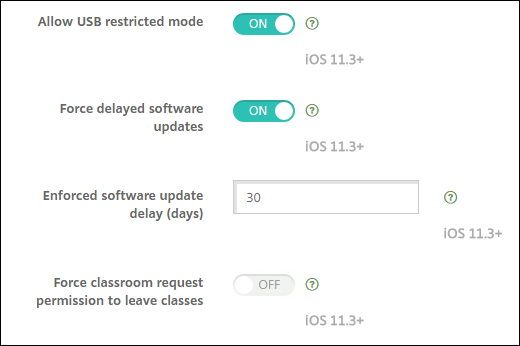
- Allow USB restricted mode: Only available for supervised devices. If set to Off, the device can always connect to USB accessories while locked. Default is On. Available from iOS 11.3.
- Force delayed software updates: Only available for supervised devices. If set to On, delays user visibility of Software Updates. With this restriction in place, the user will not see a software update until the specified number of days after the software update release date. Default is Off. Available from iOS 11.3 and macOS 10.13.4.
- Enforced software update delay (days): Only available for supervised devices. This restriction allows the admin to set how long to delay a software update on the device. The max is 90 days and the default value is 30. Available from iOS 11.3 and macOS 10.13.4.
- Force classroom request permission to leave classes: Only available for supervised devices. If set to On, a student enrolled in an unmanaged course with Classroom must request permission from the teacher when trying to leave the course. Default is Off. Available from iOS 11.3.
See Restrictions device policy.
Exchange device policy updates for iOS or macOS
More S/MIME Exchange signing and encryption settings as of iOS 12. The Exchange device policy now includes settings to configure S/MIME signing and encryption.
For S/MIME signing:
- Signing identity credential: Choose the signing credential to use.
- S/MIME Signing User Overridable: If set to On, users can turn S/MIME signing on and off in the settings of their devices. The default is Off.
- S/MIME Signing Certificate UUID User Overridable: If set to On, users can select, in the settings of their devices, the signing credential to use. The default is Off.
For S/MIME encryption:
- Encryption identity credential: Choose the encryption credential to use.
- Enable per message S/MIME switch: When set to On, shows users an option to switch S/MIME encryption on or off for each message they compose. The default is Off.
- S/MIME Encrypt By Default User Overridable: If set to On, users can, in the settings of their devices, select whether S/MIME is on by default. The default is Off.
- S/MIME Encryption Certificate UUID User Overridable: If set to On, users can turn S/MIME encryption identity and encryption on and off in the settings of their devices. The default is Off.
Exchange OAuth settings as of iOS 12. You can now configure the connection with Exchange to use OAuth for authentication.
Exchange OAuth settings as of macOS 10.14. You can now configure the connection with Exchange to use OAuth for authentication. For authentication using OAuth, you can specify the sign-in URL for a setup that doesn’t use AutoDiscovery.
Mail device policy updates for iOS
More S/MIME Exchange signing and encryption settings as of iOS 12. The Mail device policy includes more settings to configure S/MIME signing and encryption.
For S/MIME signing:
-
Enable S/MIME Signing: Select whether this account supports S/MIME signing. The default is On. When set to On, the following fields appear.
- S/MIME Signing User Overridable: If set to On, users can turn S/MIME signing on and off in the settings of their devices. The default is Off. This option applies to iOS 12.0 and later.
- S/MIME Signing Certificate UUID User Overridable: If set to On, users can select, in the settings of their devices, the signing credential to use. The default is Off. This option applies to iOS 12.0 and later.
For S/MIME encryption:
-
Enable S/MIME Encryption: Select whether this account supports S/MIME encryption. The default is Off. When set to On, the following fields appear.
- Enable per message S/MIME switch: When set to On, shows users an option to switch S/MIME encryption on or off for each message they compose. The default is Off.
- S/MIME Encrypt By Default User Overridable: If set to On, users can, in the settings of their devices, select whether S/MIME is on by default. The default is Off. This option applies to iOS 12.0 and later.
- S/MIME Encryption Certificate UUID User Overridable: If set to On, users can turn S/MIME encryption identity and encryption on and off in the settings of their devices. The default is Off. This option applies to iOS 12.0 and later.
See Mail device policy.
Apps notifications device policy updates for iOS
The following Apps notifications settings are available from iOS 12.
- Show in CarPlay: If On, notifications display in Apple CarPlay. Default is On.
- Enable Critical Alert: If On, an app can mark a notification as a critical notification that ignores Do Not Disturb and ringer settings. Default is Off.
See Apps notifications device policy
Support for shared iPads used with Apple Education
The XenMobile integration with Apple Education features now supports shared iPads. Multiple students in a classroom can share an iPad for different subjects taught by one or several instructors.
Either you or instructors enroll shared iPads and then deploy device policies, apps, and media to the devices. After that, students provide their managed Apple ID credentials to sign in to a shared iPad. If you previously deployed an Education Configuration policy to students, they no longer sign-in as an “Other User” to share devices.
Prerequisites for shared iPads:
- Any iPad Pro, iPad 5th generation, iPad Air 2 or later, and iPad mini 4 or later
- At least 32 GB of storage
- Supervised
For more information, see Configure shared iPads.
Role-based access control (RBAC) permissions change
The RBAC permission Add/Delete Local Users is now split into two permissions: Add Local Users and Delete Local Users.
For more information, see Configure roles with RBAC.
In this article
- Apple Volume Purchase Program migration to Apple Business Manager (ABM) and Apple School Manager (ASM)
- Additional support for iOS 13
- Requirements for trusted certificates in iOS 13 and macOS 15
- Upgrade from GCM to FCM
- Before you upgrade to XenMobile 10.11 (on-premises)
- To upgrade
- After you upgrade
- New and updated device policy settings for Android Enterprise devices
- Lock and reset password for Android Enterprise
- New Restrictions device policy settings for iOS or macOS
- Exchange device policy updates for iOS or macOS
- Mail device policy updates for iOS
- Apps notifications device policy updates for iOS
- Support for shared iPads used with Apple Education
- Role-based access control (RBAC) permissions change