-
-
macOS
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
macOS
To manage macOS devices in XenMobile, you set up an Apple Push Notification service (APNs) certificate from Apple. For information, see APNs certificates.
XenMobile® enrolls macOS devices into MDM. XenMobile supports the following enrollment authentication types for macOS devices in MDM.
- Domain
- Domain plus one-time password
- Invitation URL plus one-time password
Requirements for trusted certificates in macOS 15:
Apple has new requirements for TLS server certificates. Verify that all certificates follow the new Apple requirements. See the Apple publication, https://support.apple.com/en-us/HT210176. For help with managing certificates, see Uploading certificates in XenMobile.
A general workflow for starting macOS device management is as follows:
-
Set up device and app security actions. See Security actions.
For supported operating systems, see Supported device operating systems.
Apple host names that must remain open
Some Apple host names must remain open to make sure proper operation of iOS, macOS, and Apple App Store. Blocking those host names can affect the installation, update, and proper operation of the following: iOS, iOS apps, MDM operation, and device and app enrollment. For more information, see https://support.apple.com/en-us/HT201999.
Supported enrollment methods
The following table lists the enrollment methods that XenMobile supports for macOS devices:
| Method | Supported |
|---|---|
| Apple Deployment Program | Yes |
| Apple School Manager | Yes |
| Apple Configurator | No |
| Manual enrollment | Yes |
| Enrollment invitations | Yes |
Apple has device enrollment programs for business and education accounts. For business accounts, you enroll in the Apple Deployment Program to use the Apple Deployment Program for device enrollment and management in XenMobile. That program is for iOS and macOS devices. See Deploy devices through Apple Deployment Program.
For education accounts, you create an Apple School Manager account. Apple School Manager unifies the Deployment Program and volume purchase. Apple School Manager is a type of Education Apple Deployment Program. See Integrate with Apple Education features.
You can use the Apple Deployment Program to bulkly enroll iOS and macOS devices. You can purchase those devices directly from Apple, a participating Apple Authorized Reseller, or a carrier.
Configure macOS device policies
Use these policies to configure how XenMobile interacts with devices running macOS. This table lists all device policies available for macOS devices.
Enroll macOS devices
XenMobile provides two methods to enroll devices that are running macOS. Both methods enable macOS users to enroll over the air, directly from their devices.
-
Send users an enrollment invitation: This enrollment method enables you to set any of the following enrollment security modes for macOS devices:
- User name + password
- User name + PIN
- Two-factor authentication
When the user follows the instructions in the enrollment invitation, a sign-on screen with the user name filled in appears.
-
Send users an enrollment link: This enrollment method for macOS devices sends users an enrollment link, which they can open in Safari or Chrome browsers. A user then enrolls by providing their user name and password.
To prevent the use of an enrollment link for macOS devices, set the server property Enable macOS OTAE to false. As a result, macOS users can enroll only by using an enrollment invitation.
Send macOS users an enrollment invitation
-
Add an invitation for macOS user enrollment. See Create an enrollment invitation.
-
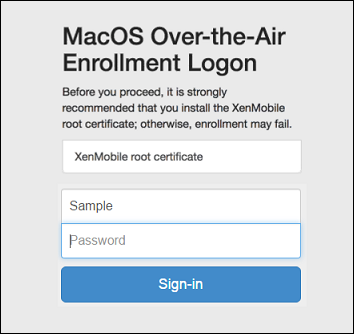
After users receive the invitation and click the link, the following screen appears in the Safari browser. XenMobile fills in the user name. If you chose Two Factor for the enrollment security mode, another field appears.
-
Users install certificates as necessary. Whether users see the prompt to install certificates depends on whether you configured the following for macOS: A publicly trusted SSL certificate and a publicly trusted digital signing certificate. For information about certificates, see Certificates and authentication.
-
Users provide the requested credentials.
The Mac device policies install. You can now start managing macOS devices with XenMobile just as you manage mobile devices.
Send macOS users an installation link
-
Send the enrollment link
https://serverFQDN:8443/instanceName/macos/otae, which users can open in Safari or Chrome browsers.- serverFQDN is the fully qualified domain name (FQDN) of the server running XenMobile.
- Port 8443 is the default secure port. If you configured a different port, use that port instead of 8443.
- The instanceName, often shown as
zdm, is the name specified during server installation.
For more information about sending installation links, see Send an enrollment invitation.
-
Users install certificates as necessary. If you configured a publicly trusted SSL certificate and digital signing certificate for iOS and macOS, users see the prompt to install the certificates. For information about certificates, see Certificates and authentication.
-
Users sign on to their Macs.
The Mac device policies install. You can now start managing macOS devices with XenMobile just as you manage mobile devices.
Security actions
macOS supports the following security actions. For a description of each security action, see Security actions.
| Revoke | Lock | Selective Wipe |
| Full Wipe | Certificate renewal |
Lock macOS devices
You can remotely lock a lost macOS device. XenMobile locks the device. It then generates a PIN code and sets it in the device. To access the device, the user types the PIN code. Use Cancel Lock to remove the lock from the XenMobile console.
You can use the Passcode device policy to configure more settings associated with the PIN code. For more information, see macOS settings.
-
Click Manage > Devices. The Devices page appears.
-
Select the macOS device that you want to lock.
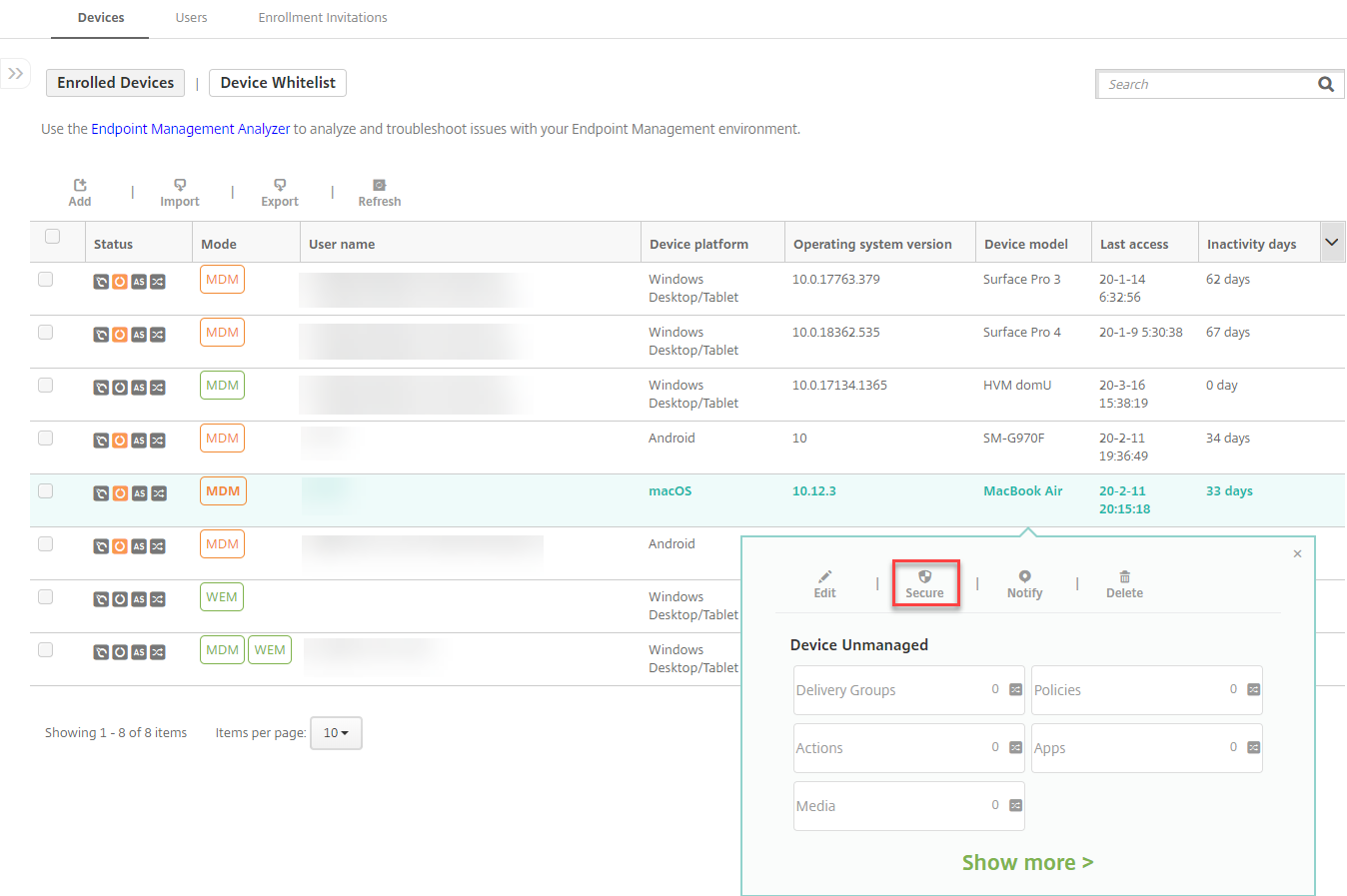
Select the checkbox next to a device to show the options menu above the device list. You can also click anywhere else on a listed item to show the options menu on the right side of the list.
-
In the options menu, click Secure. The Security Actions dialog box appears.
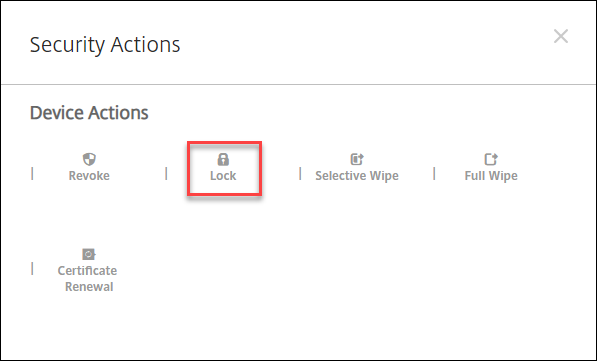
-
Click Lock. The Security Actions confirmation dialog box displays.
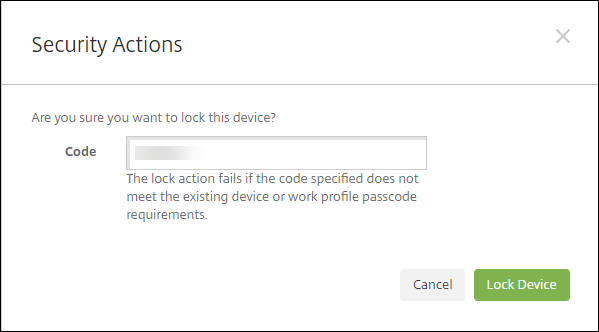
-
Click Lock Device.
Important:
You can also specify a passcode instead of using the code that XenMobile generates. The lock action fails if the code specified does not meet the code requirements of the device or existing work profile.
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.