-
-
-
Windows Information Protection device policy
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Windows Information Protection device policy
Windows Information Protection (WIP), previously known as enterprise data protection (EDP), is a Windows technology that protects against the potential leakage of enterprise data. Data leakage can occur through sharing of enterprise data to non-enterprise protected apps, between apps, or outside of the organization network. For more information, see Protect your enterprise data using Windows Information Protection (WIP).
You can create a device policy in XenMobile® to specify the apps that require Windows Information Protection at the enforcement level you set. The Windows Information Protection policy is for supervised Tablet and Desktop running Windows 10 or Windows 11.
XenMobile includes some common apps and you can add others. You specify for the policy an enforcement level that affects the user experience. For example, you can:
-
Block any inappropriate data sharing.
-
Warn about inappropriate data sharing and allow users to override the policy.
-
Run WIP silently while logging and permitting inappropriate data sharing.
To exclude apps from Windows Information Protection, define the apps in Microsoft AppLocker XML files and then import those files into XenMobile.
To add or configure this policy, go to Configure > Device Policies. For more information, see Device policies.
Windows 10 and Windows 11 settings
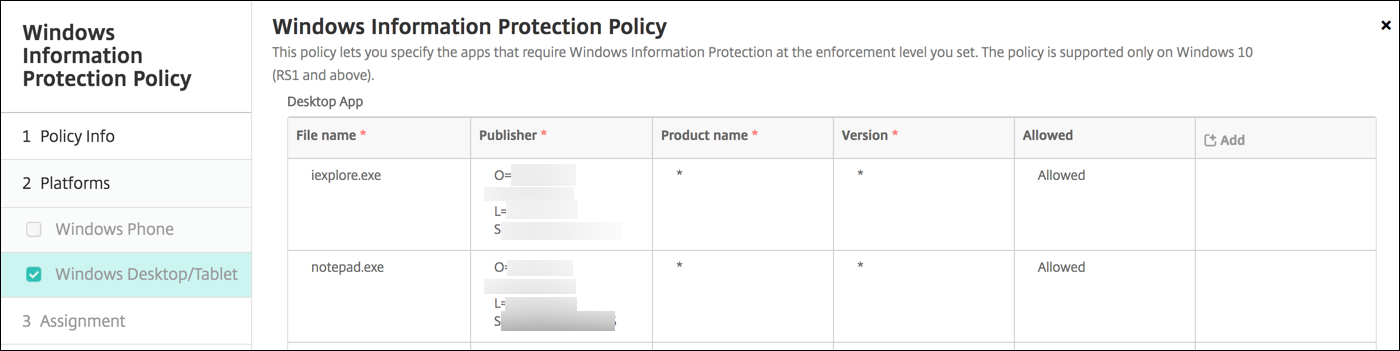
-
Desktop App (Windows 10 or Windows 11 Desktop), Store App (Windows 10 or Windows 11 Tablet): XenMobile includes some common apps, as shown in the preceding sample. You can edit or remove those apps as needed.
To add other apps: In the Desktop App or Store App table, click Add and provide the app information.
Allowed apps can read, create, and update enterprise data. Denied apps can’t access enterprise data. Exempt apps can read enterprise data but can’t create or modify the data.
-
AppLocker XML: Microsoft provides a list of Microsoft apps that have known compatibility issues with WIP. To exclude those apps from WIP, click Browse to upload the list. XenMobile combines the uploaded AppLocker XML and the configured desktop and store apps in the policy sent to the device. For more information, see Recommended block list for Windows Information Protection.
-
Enforcement level: Select an option to specify how you want Windows Information Protection to protect and manage data sharing. Defaults to Off.
-
0-Off: WIP is off and doesn’t protect or audit your data.
-
1-Silent: WIP runs silently, logs inappropriate data sharing, and doesn’t block anything. You can access logs through Reporting CSP.
-
2-Override: WIP warns users about potentially unsafe data sharing. Users can override warnings and share the data. This mode logs actions, including user overrides, to your audit log.
-
3-Block: WIP prevents users from completing potentially unsafe data sharing.
-
-
Protected domain names: The domains that your enterprise uses for its user identities. This list of managed identity domains, along with the primary domain, make up the identity of your managing enterprise. The first domain in the list is the primary corporate identity used in the Windows UI. Use “ ” to separate list items. For example: domain1.com | domain2.com -
Data recovery certificate: Click Browse and then select a recovery certificate to use for data recovery of encrypted files. This certificate is the same as the data recovery agent (DRA) certificate for the encrypting file system (EFS), only delivered through MDM instead of Group Policy. If a recovery certificate isn’t available, create it. For information, see “Create a data recovery certificate” in this section.
-
Network domain names: A list of domains that comprise the boundaries of the enterprise. WIP protects all traffic to the fully qualified domains in this list. This setting, with the IP range setting, detects whether a network endpoint is enterprise or personal on private networks. Use a comma to separate list items. For example: corp.example.com,region.example.com
-
IP range: A list of the enterprise IPv4 and IPv6 ranges that define the computers in the enterprise network. WIP considers these locations as safe destinations for enterprise data sharing. Use commas to separate list items. For example:
10.0.0.0-10.255.255.255,2001:4898::-2001:4898:7fff:ffff:ffff:ffff:ffff:ffff -
IP ranges list is authoritative: To prevent auto-detection of IP ranges by Windows, change this setting to On. Defaults to Off.
-
Proxy servers: A list of the proxy servers that the enterprise can use for corporate resources. This setting is required if you use a proxy in your network. Without a proxy server, enterprise resources might be unavailable when a client is behind a proxy. For example, resources might be unavailable from certain Wi-Fi hotspots at hotels and restaurants. Use commas to separate list items. For example:
proxy.example.com:80;157.54.11.118:443 -
Internal proxy servers: A list of the proxy servers that your devices go through to reach your cloud resources. Using this server type indicates that the cloud resources you’re connecting to are enterprise resources. Don’t include in this list any of the servers in the Proxy servers setting, which are used for non-WIP-protected traffic. Use commas to separate list items. For example:
example.internalproxy1.com;10.147.80.50 -
Cloud resources: A list of cloud resources protected by WIP. For each cloud resource, you can also optionally specify a proxy server in the Proxy servers list to route traffic for this cloud resource. All traffic routed through the Proxy servers is treated as enterprise traffic. Use commas to separate list items. For example:
domain1.com:InternalProxy.domain1.com,domain2.com:InternalProxy.domain2.com -
Revoke WIP certificate on unenroll: Specifies whether to revoke local encryption keys from a user device when it’s unenrolled from Windows Information Protection. After the encryption keys are revoked, a user can’t access encrypted corporate data. If Off, the keys aren’t revoked and the user continues to have access to protected files after unenrollment. Defaults to On.
- Show overlay icons: Specifies whether to include the Windows Information Protection icon overlay on corporate files in Explorer and enterprise only app tiles in the Start menu. Defaults to Off.
-
Create a data recovery certificate
A data recover certificate is required to enable the Windows Information Protection policy.
-
On the machine where the XenMobile console is running, open a command prompt and navigate to a folder (other than Windows\System32) where you want to create a certificate.
-
Run this command:
cipher /r:ESFDRA -
When prompted, enter a password to protect the private key file.
The cipher command creates a .cer and a .pfx file.
-
In the XenMobile console, go to Settings > Certificates and import the .cer file, which applies to Windows 10 and Windows 11 tablets.
User experience
When Windows Information Protection is in effect, apps and files include an icon:
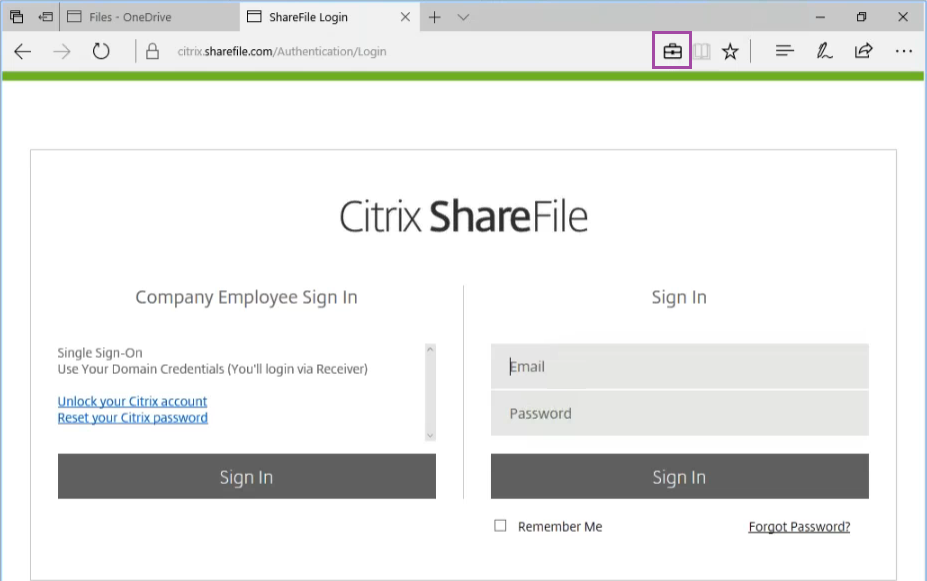
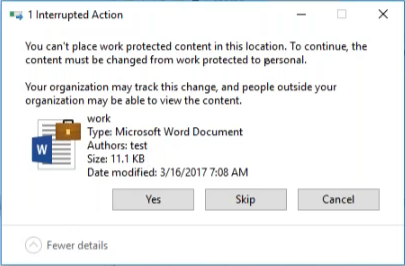
If a user copies or saves a protected file to a non-protected location, the following notification appears, depending on the enforcement level configured.
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.