-
-
-
-
Reference Architecture for On-Premises Deployments
-
Configuring certificate-based authentication with EWS for Secure Mail push notifications
-
Integrate XenMobile Mobile Device Management with Cisco Identity Services Engine
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Reference Architecture for On-Premises Deployments
The figures in this article illustrate the reference architectures for the XenMobile deployment on-premises. The deployment scenarios include MDM-only, MAM-only, and MDM+MAM as the core architectures, and those that include components, such as the SNMP Manager, Citrix Gateway connector™ for Exchange ActiveSync, Endpoint Management connector for Exchange ActiveSync, and Virtual Apps and Desktops. The figures show the minimal components required for XenMobile.
Use this chart as a general guide for your deployment decisions.
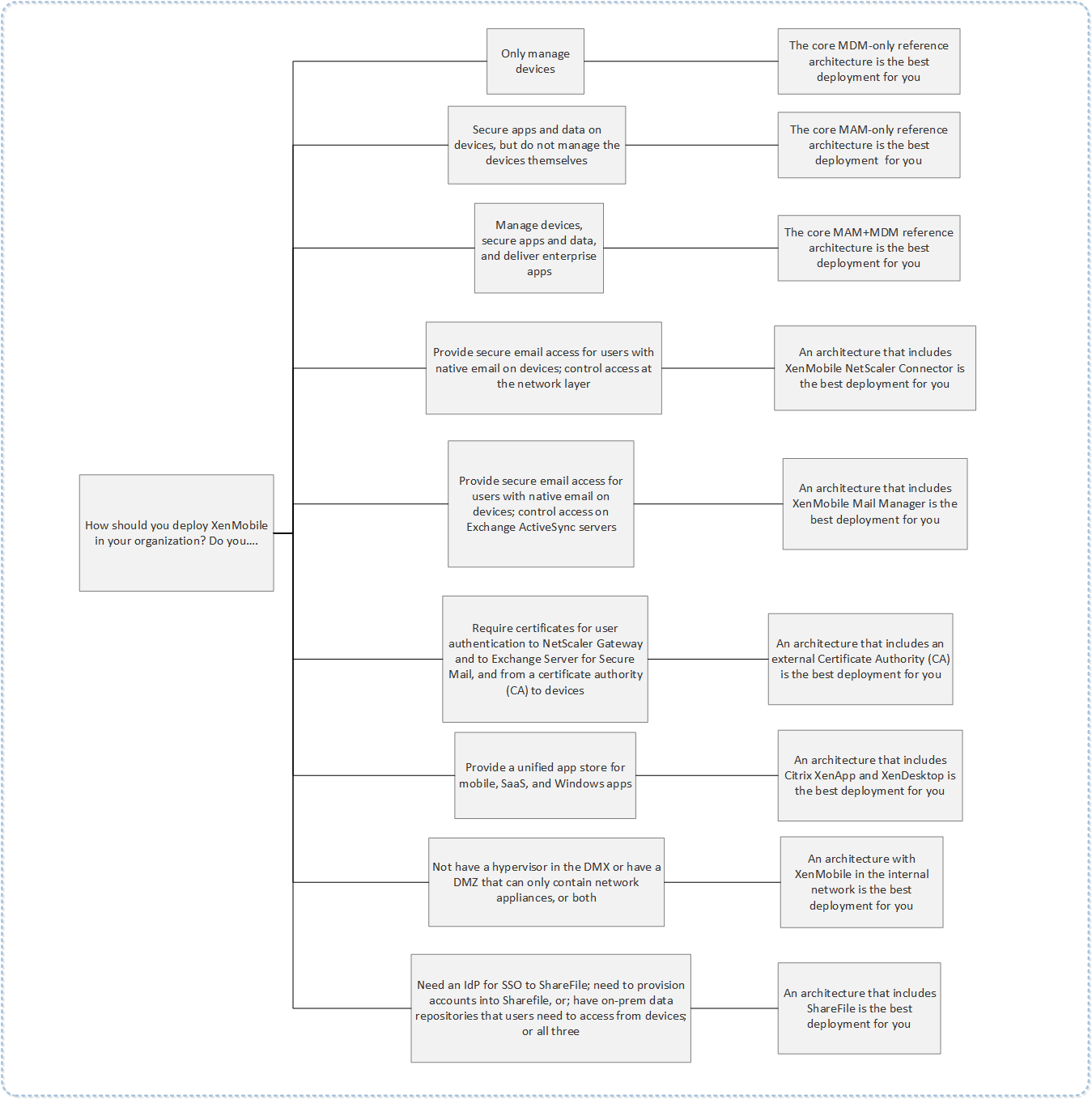
In the figures, the numbers on the connectors represent ports that you must open to allow connections between the components. For a complete list of ports, see Port requirements in the XenMobile documentation.
Core MDM-Only Reference Architecture
Deploy this architecture if you plan to use only the MDM features of XenMobile. For example, you need to manage a corporate-issued device through MDM to deploy device policies, apps and to retrieve asset inventories and be able to carry out actions on devices, such as a device wipe.
Core MAM-Only Reference Architecture
Deploy this architecture if you plan to use only the MAM features of XenMobile without having devices enroll for MDM. For example, you want to secure apps and data on BYO mobile devices; you want to deliver enterprise mobile apps and can lock apps and wipe their data. The devices cannot be MDM enrolled.
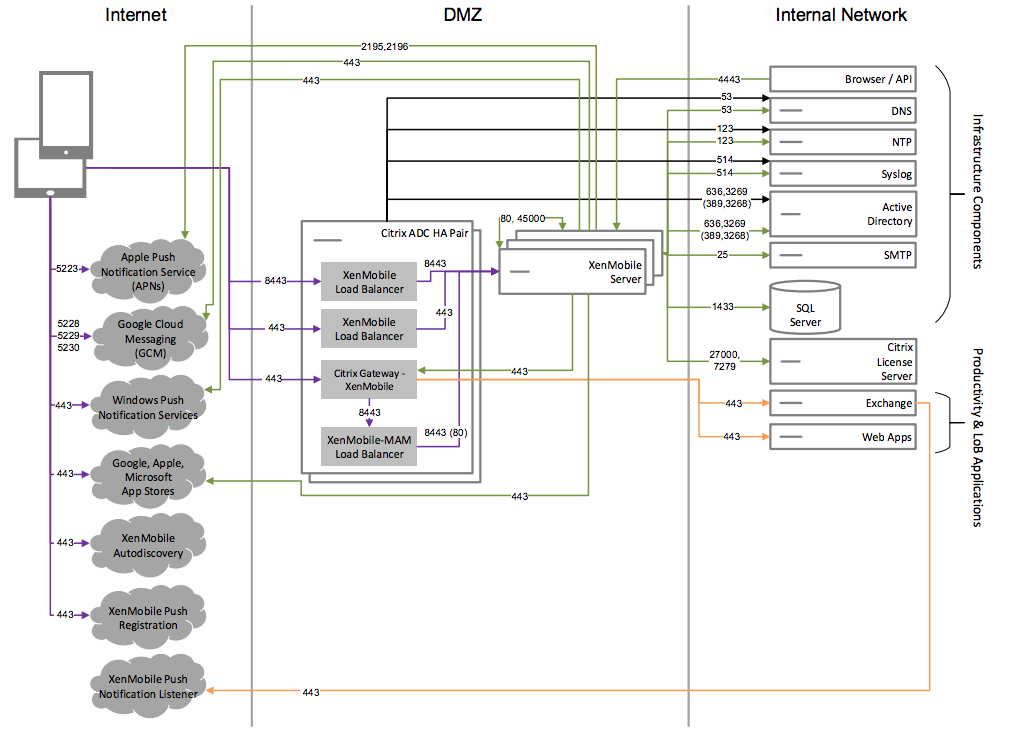
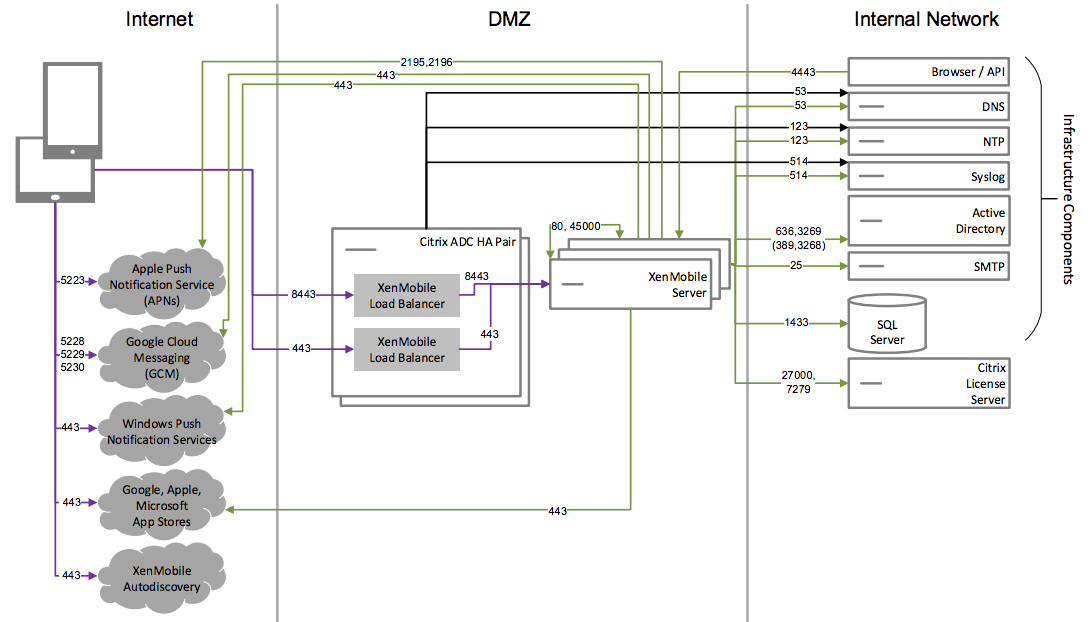
Core MAM+MDM Reference Architecture
Deploy this architecture if you plan to use the MDM+MAM features of XenMobile. For example, you want to manage a corporate-issued device via MDM; you want to deploy device policies and apps, retrieve an asset inventory and can wipe devices. You also want to deliver enterprise mobile apps and can lock apps and wipe the data on devices.
Reference Architecture with SNMP
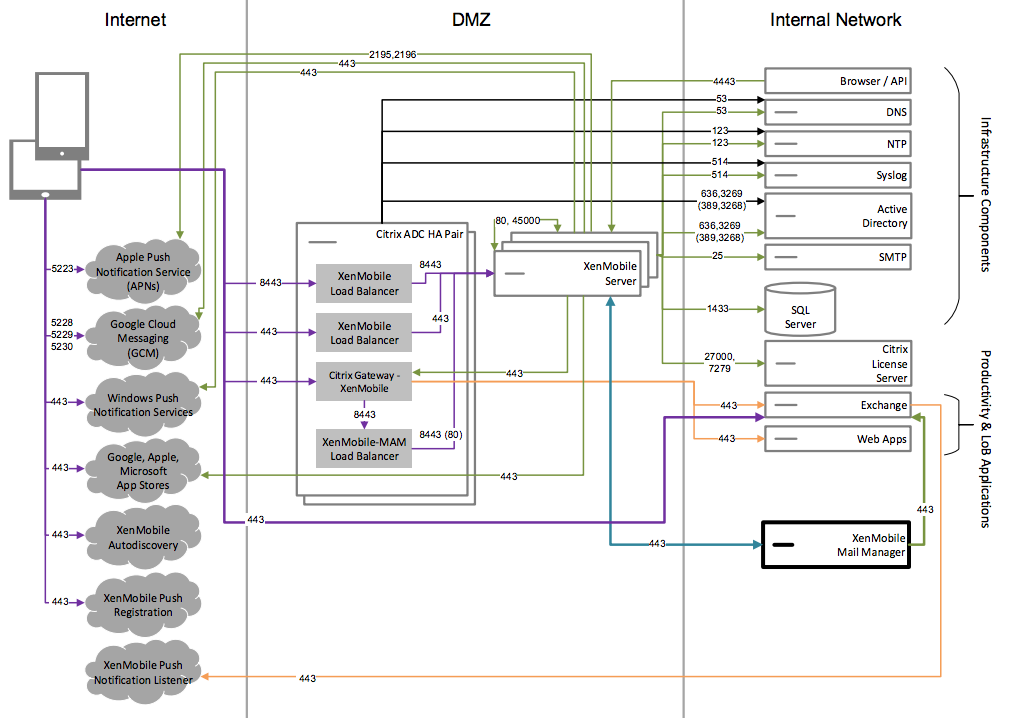
Deploy this architecture if you plan to enable SNMP monitoring with XenMobile. For example, you want to allow monitoring systems to query and obtain information on your XenMobile nodes. For more information, see SNMP monitoring.
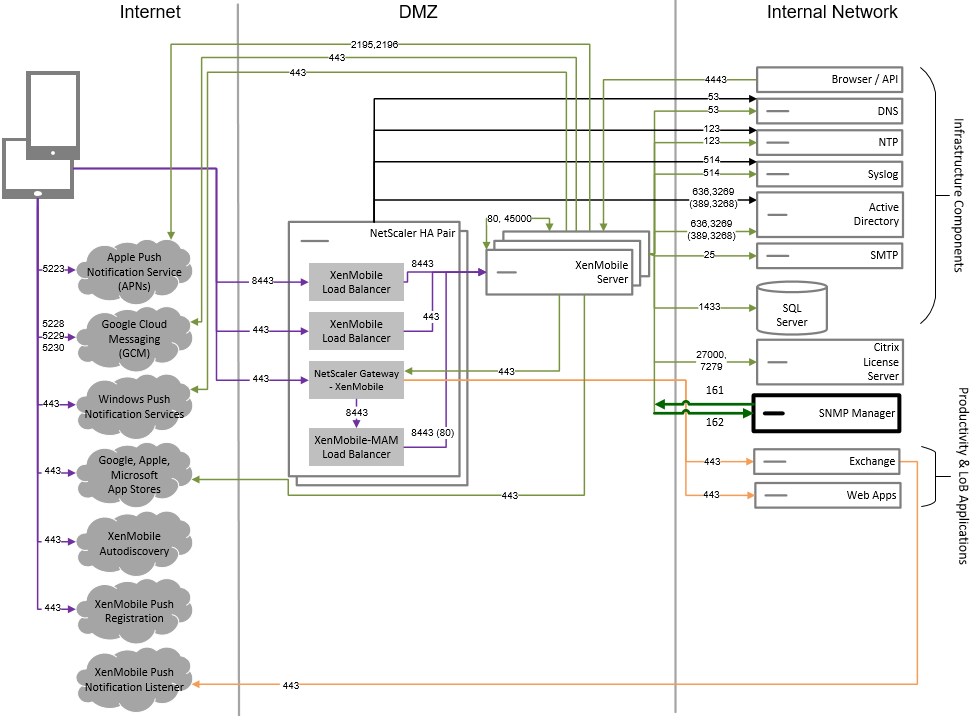
Reference Architecture with Citrix Gateway connector for Exchange ActiveSync
Deploy this architecture if you plan to use Citrix Gateway connector for Exchange ActiveSync with XenMobile. For example, you need to provide secure email access to users who use native mobile email apps. These users will continue accessing email through a native app or you can transition them over time to Citrix Secure Mail. Access control needs to occur at the network layer before traffic hits the Exchange Active Sync servers. Even though the diagram shows the connector for Exchange ActiveSync deployed in an MDM and MAM architecture, you can also deploy the connector for Exchange ActiveSync in the same manner as part of an MDM-only architecture.
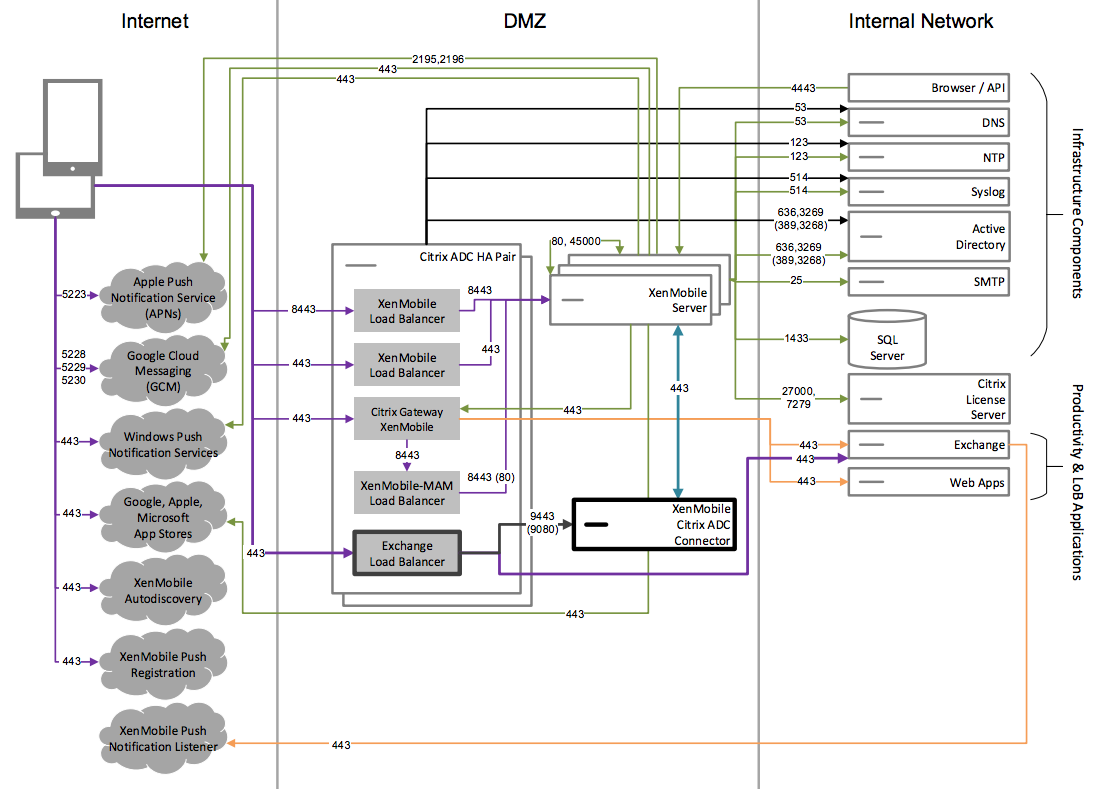
Reference Architecture with Endpoint Management connector for Exchange ActiveSync
Deploy this architecture if you plan to use Endpoint Management connector for Exchange ActiveSync with XenMobile. For example, you want to provide secure email access to users who use native mobile email apps. These users will continue accessing email via a native app or you can transition users over time to Secure Mail. You can achieve access control on the Exchange ActiveSync servers. Although the diagram shows the Endpoint Management connector for Exchange ActiveSync deployed in an MDM and MAM architecture, you can also deploy the Endpoint Management connector for Exchange ActiveSync in the same manner as part of an MDM-only architecture.
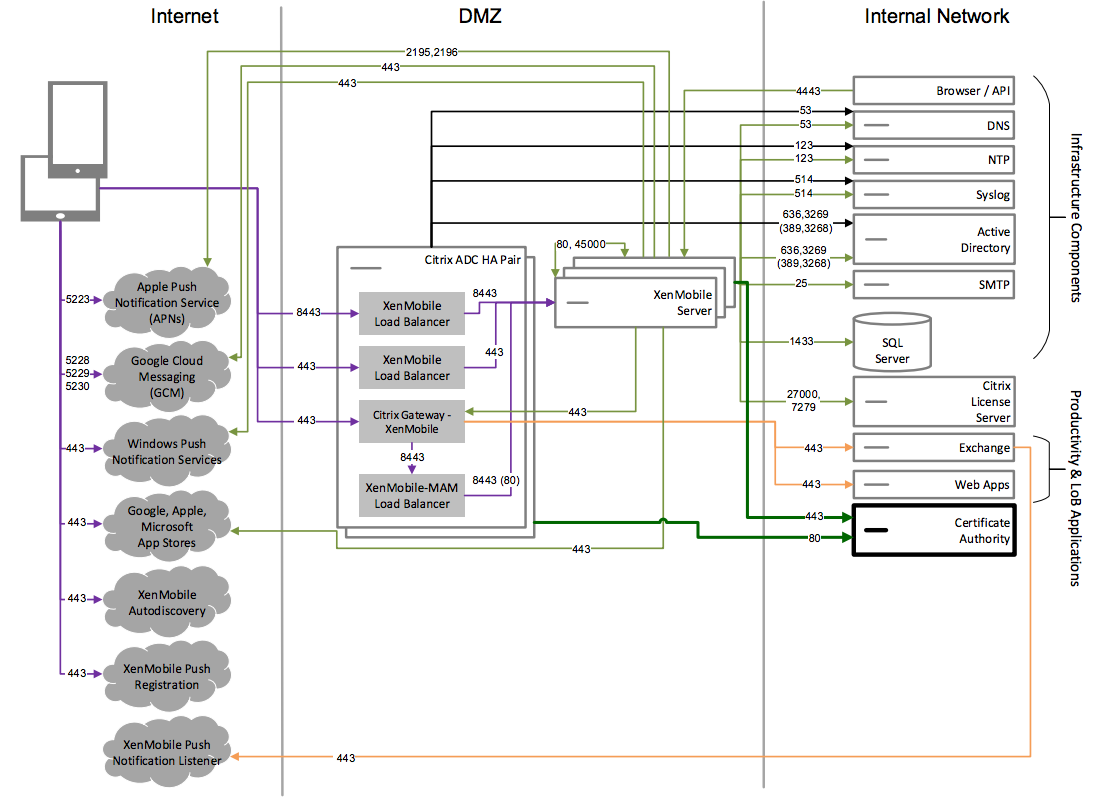
Reference Architecture with External Certificate Authority
A deployment that includes an external certificate authority is recommended to meet one or more of the following requirements:
- You require user certificates for user authentication to Citrix Gateway (for intranet access).
- You require Secure Mail users to authenticate to the Exchange Server by using a user certificate.
- You must push certificates issued by your corporate Certificate Authority to mobile devices for Wi-Fi access, for example.
Although the diagram shows an external certificate authority deployed in an MDM+MAM architecture, you can also deploy an external Certificate Authority in the same manner as part of an MDM-only or MAM-only architecture.
Reference Architecture with Virtual Apps and Desktops
Deploy this architecture if you plan to integrate Virtual Apps and Desktops with XenMobile. For example, you need to provide a unified app store to mobile users for all types of applications (mobile, SaaS and Windows). Although the diagram shows Virtual Desktops deployed in an MDM and MAM architecture, you can also deploy those desktops in the same manner as part of a MAM-only architecture.
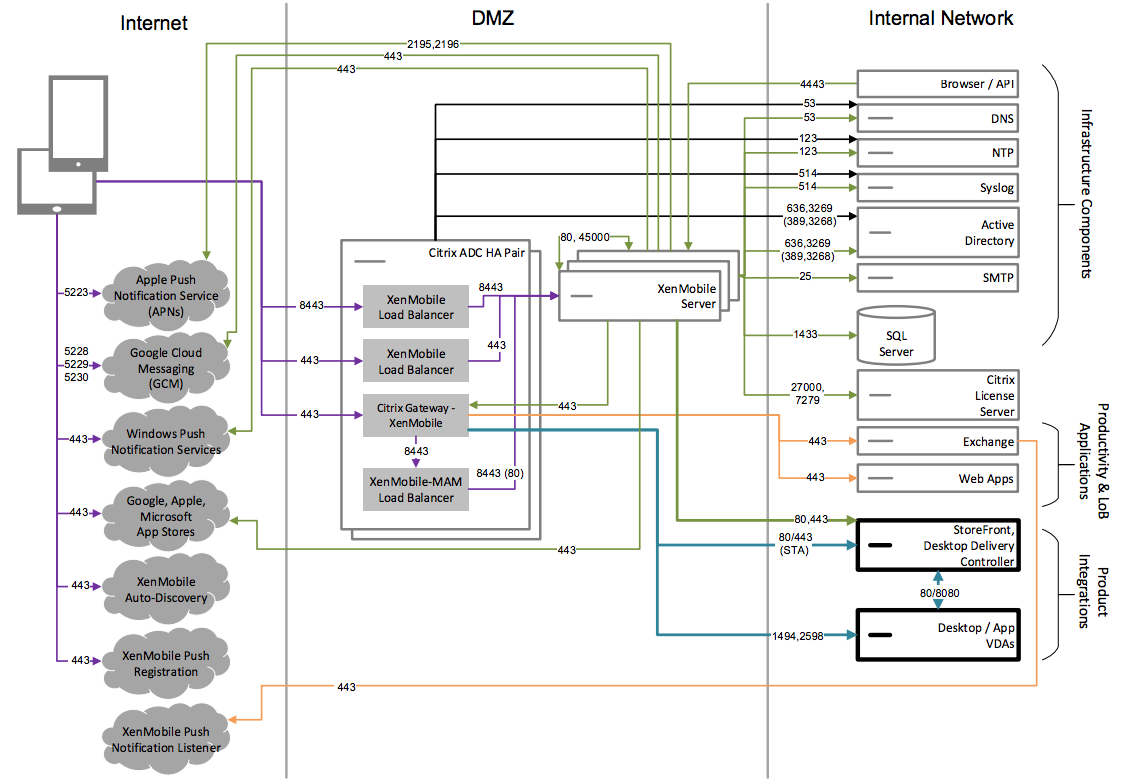
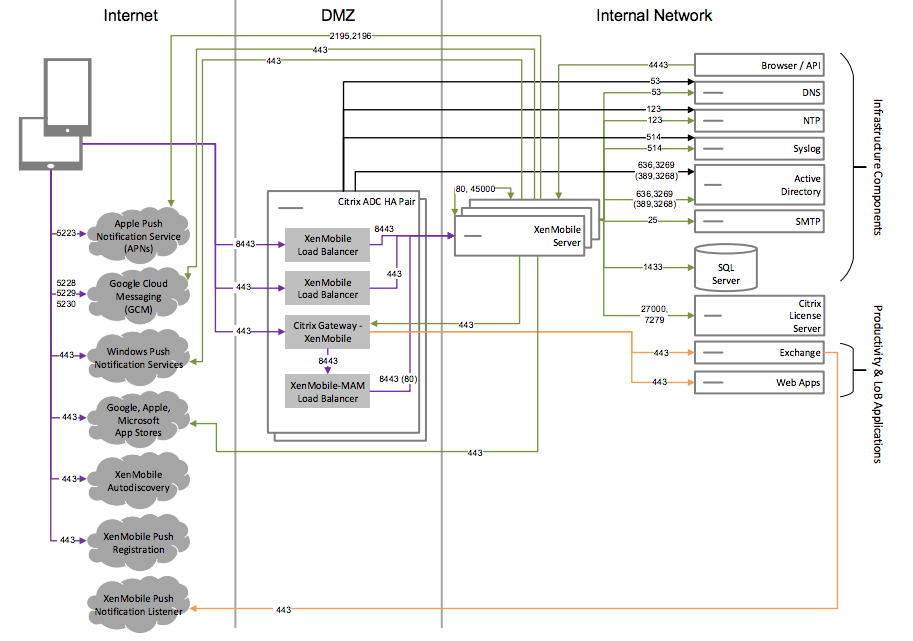
Reference Architecture with XenMobile in the Internal Network
You can deploy an architecture with XenMobile in the internal network to meet one or more of the following requirements:
- You do not have or are not allowed to have a hypervisor in the DMZ.
- Your DMZ can only contain network appliances.
- Your security requirements require the use of SSL Offload.
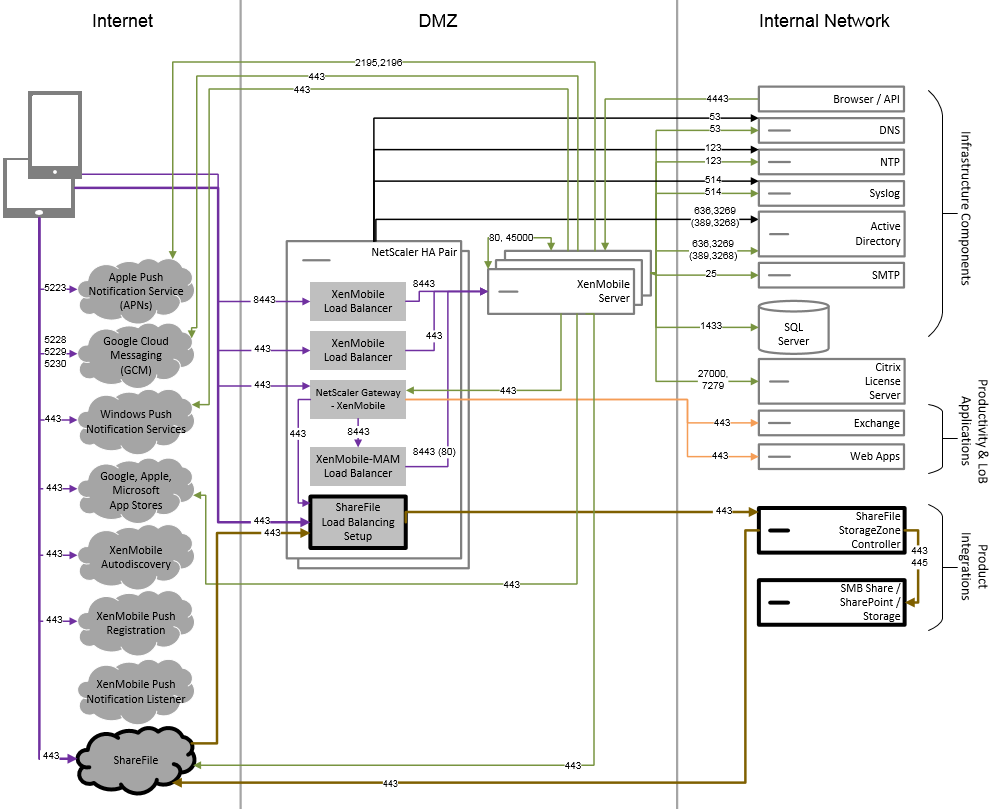
Reference Architecture with ShareFile
Deploy this architecture if you want to integrate Citrix Files or only storage zone connectors with XenMobile. Citrix Files integration enables you to meet one or more of the following requirements:
- You need an IdP to give users a single sign-on (SSO) to ShareFile.com.
- You need a way to provision accounts into ShareFile.com.
- You have on-premises data repositories that must be accessed from mobile devices.
An integration with only storage zone connectors gives users secure mobile access to existing on-premises storage repositories, such as SharePoint sites and network file shares. In this configuration, you don’t need to set up a ShareFile subdomain, provision users to Citrix Files, or host Citrix Files data.
Although the diagram shows Citrix Files deployed in a MDM+MAM architecture, you can also deploy Citrix Files in the same manner as part of a MAM-only architecture.
Share
Share
In this article
- Core MDM-Only Reference Architecture
- Core MAM-Only Reference Architecture
- Core MAM+MDM Reference Architecture
- Reference Architecture with SNMP
- Reference Architecture with Citrix Gateway connector for Exchange ActiveSync
- Reference Architecture with Endpoint Management connector for Exchange ActiveSync
- Reference Architecture with External Certificate Authority
- Reference Architecture with Virtual Apps and Desktops
- Reference Architecture with XenMobile in the Internal Network
- Reference Architecture with ShareFile
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.