-
-
-
-
SSO and Proxy Considerations for MDX Apps
-
Configuring certificate-based authentication with EWS for Secure Mail push notifications
-
Integrate XenMobile Mobile Device Management with Cisco Identity Services Engine
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
SSO and Proxy Considerations for MDX Apps
XenMobile integration with Citrix ADC enables you to provide users with single sign-on (SSO) to all back end HTTP/HTTPS resources. Depending on your SSO authentication requirements, you can configure user connections for an MDX app to use either of these options:
- Secure Browse, which is a type of clientless VPN
- Full VPN Tunnel
If Citrix ADC isn’t the best way to provide SSO in your environment, you can set up an MDX app with policy-based local password caching. This article explores the various SSO and proxy options with a focus on the Secure Web. The concepts apply to other MDX apps.
The following flow chart summarizes the decision flow for SSO and user connections.
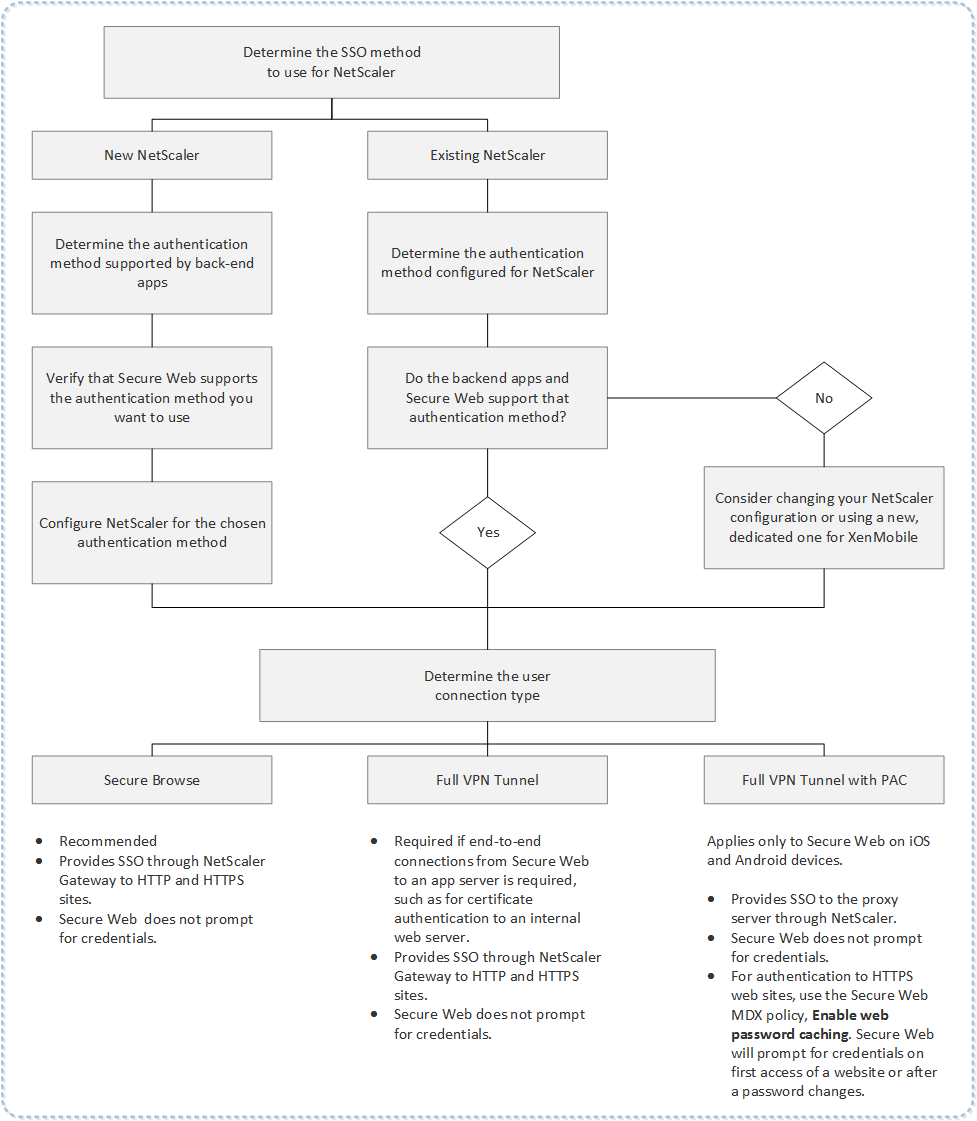
Citrix ADC Authentication Methods
This section provides general information about the authentication methods supported by Citrix ADC.
SAML authentication
When you configure Citrix ADC for Security Assertion Markup Language (SAML), users can connect to web apps that support the SAML protocol for single sign-on. Citrix Gateway supports the identity provider (IdP) single sign-on for SAML web apps.
Required configuration:
- Configure SAML SSO in the Citrix ADC Traffic profile.
- Configure the SAML IdP for the requested service.
NTLM authentication
If SSO to web apps is enabled in the session profile, Citrix ADC performs NTLM authentication automatically.
Required configuration:
- Enable SSO in the Citrix ADC Session or Traffic profile.
Kerberos impersonation
XenMobile® supports Kerberos for Secure Web only. When you configure Citrix ADC for Kerberos SSO, Citrix ADC uses impersonation when a user password is available to Citrix ADC. Impersonation means that Citrix ADC uses user credentials to get the ticket required to gain access to services, such as Secure Web.
Required configuration:
- Configure the Citrix ADC “Worx” Session policy to allow it to identify the Kerberos Realm from your connection.
- Configure a Kerberos Constrained Delegation (KCD) account on Citrix ADC. Configure that account with no password and bind it to a traffic policy on your XenMobile gateway.
- For those and other configuration details, see the Citrix blog: WorxWeb and Kerberos Impersonation SSO.
Kerberos Constrained Delegation
XenMobile supports Kerberos for Secure Web only. When you configure Citrix ADC for Kerberos SSO, Citrix ADC uses constrained delegation when a user password is not available to Citrix ADC.
With constrained delegation, Citrix ADC uses a specified administrator account to get tickets on behalf of users and services.
Required configuration:
- Configure a KCD account in the Active Directory with the required permissions and a KCD account on Citrix ADC.
- Enable SSO in the Citrix ADC Traffic profile.
- Configure the back-end website for Kerberos authentication.
Form Fill Authentication
When you configure Citrix ADC for Form-based single sign-on, users can log on one time to access all protected apps in your network. This authentication method applies to apps that use Secure Browse or Full VPN modes.
Required configuration:
- Configure Form-based SSO in the Citrix ADC Traffic profile.
Digest HTTP authentication
If you enable SSO to web apps in the session profile, Citrix ADC performs digest HTTP authentication automatically. This authentication method applies to apps that use Secure Browse or Full VPN modes.
Required configuration:
- Enable SSO in the Citrix ADC Session or Traffic profile.
Basic HTTP authentication
If you enable SSO to web apps in the session profile, Citrix ADC performs basic HTTP authentication automatically. This authentication method applies to apps that use Secure Browse or Full VPN modes.
Required configuration:
- Enable SSO in the Citrix ADC Session or Traffic profile.
Secure Browse, Full VPN Tunnel, or Full VPN Tunnel with PAC
The following sections describe the user connection types for Secure Web. For more information, see this Secure Web article in the Citrix documentation, Configuring user connections.
Full VPN Tunnel
Connections that tunnel to the internal network can use a full VPN tunnel. Use the Secure Web Preferred VPN mode policy to configure a full VPN tunnel. Citrix recommends Full VPN tunnel for connections that use client certificates or end-to-end SSL to a resource in the internal network. A full VPN tunnel handles any protocol over TCP. You can use a full VPN tunnel with Windows, Mac, iOS, and Android devices.
In Full VPN Tunnel mode, the Citrix ADC does not have visibility inside an HTTPS session.
Secure Browse
Connections that tunnel to the internal network can use a variation of a clientless VPN, referred to as Secure Browse. Secure Browse is the default configuration specified for the Secure Web Preferred VPN mode policy. Citrix recommends Secure Browse for connections that require single sign-on (SSO).
In Secure Browse mode, Citrix ADC breaks the HTTPS session into two parts:
- From the client to Citrix ADC
- From Citrix ADC to the back-end resource server.
In this manner, Citrix ADC has full visibility into all transactions between the client and server, enabling it to provide SSO.
You can also configure proxy servers for Secure Web when used in secure browse mode. For details, see the blog XenMobile WorxWeb Traffic Through Proxy Server in Secure Browse Mode.
Full VPN Tunnel with PAC
You can use a Proxy Automatic Configuration (PAC) file with a full VPN tunnel deployment for Secure Web on iOS and Android devices. XenMobile supports proxy authentication provided by Citrix ADC. A PAC file contains rules that define how web browsers select a proxy to access a given URL. PAC file rules can specify handling for both internal and external sites. Secure Web parses PAC file rules and sends the proxy server information to Citrix Gateway. Citrix Gateway is unaware of the PAC file or proxy server.
For authentication to HTTPS websites: The Secure Web MDX policy Enable web password caching enables Secure Web to authenticate and provide SSO to the proxy server through MDX.
Citrix ADC Split Tunneling
When planning your SSO and proxy configuration, you must also decide whether to use Citrix ADC split tunneling. Citrix recommends that you use Citrix ADC split tunneling only if needed. This section provides a high-level look at how split tunneling works: Citrix ADC determines the traffic path based on its routing table. When Citrix ADC split tunneling is on, Secure Hub distinguishes internal (protected) network traffic from Internet traffic. Secure Hub makes that determination based on the DNS suffix and Intranet applications. Secure Hub then tunnels only the internal network traffic through the VPN tunnel. When Citrix ADC split tunneling is off, all traffic goes through the VPN tunnel.
- If you prefer to monitor all the traffic because of security considerations, disable Citrix ADC split tunneling. As a result, all traffic goes through the VPN tunnel.
- If you use Full VPN Tunnel with PAC, you must disable Citrix Gateway split tunneling. If split tunneling is on and you configure a PAC file, the PAC file rules override the Citrix ADC split tunneling rules. A proxy server configured in a traffic policy does not override the Citrix ADC split tunneling rules.
By default, the Network access policy is set to Tunneled to the internal network for Secure Web. With that configuration, MDX apps use Citrix ADC split tunnel settings. The Network access policy default differs for some other mobile productivity apps.
Citrix Gateway also has a micro VPN reverse split tunnel mode. This configuration supports an exclusion list of IP addresses that aren’t tunneled to the Citrix ADC. Instead, those addresses are sent by using the device internet connection. For more information about reverse split tunneling, see the Citrix Gateway documentation.
XenMobile includes a Reverse split tunnel exclusion list. To prevent certain websites from tunneling through the Citrix Gateway: Add a comma-separated list of fully qualified domain names (FQDN) or DNS suffixes that connect by using the LAN instead. This list applies only to Secure Browse mode with Citrix Gateway configured for reverse split tunneling.
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.