This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
BitLocker device policy
Windows 10 and Windows 11 include a disk encryption feature called BitLocker, which provides extra file and system protections against unauthorized access of a lost or stolen Windows device. For more protection, you can use BitLocker with Trusted Platform Module (TPM) chips, version 1.2 or later. A TPM chip handles cryptographic operations and generates, stores, and limits the use of cryptographic keys.
Starting with Windows 10, build 1703, MDM policies can control BitLocker. You use the BitLocker device policy in XenMobile® to configure the settings available in the BitLocker wizard on Windows 10 and Windows 11 devices. For example, on a device with BitLocker enabled, BitLocker can prompt users for how they want to unlock their drive at startup, how to back up their recovery key, and how to unlock a fixed drive. BitLocker device policy settings also configure whether to:
- Enable BitLocker on devices without a TPM chip.
- Show recovery options in the BitLocker interface.
- Deny write access to a fixed or removable drive when BitLocker isn’t enabled.
Note:
After BitLocker encryption starts on a device, you can’t change the BitLocker settings on the device later by deploying an updated BitLocker device policy.
To add or configure this policy, go to Configure > Device Policies. For more information, see Device policies.
Requirements
-
The BitLocker device policy requires Windows 10 or Windows 11 Enterprise edition.
-
Before deploying the BitLocker device policy, prepare your environment for BitLocker use. For detailed information from Microsoft, including BitLocker system requirements, and setup, see BitLocker and the articles under that node.
Windows Desktop and Tablet settings
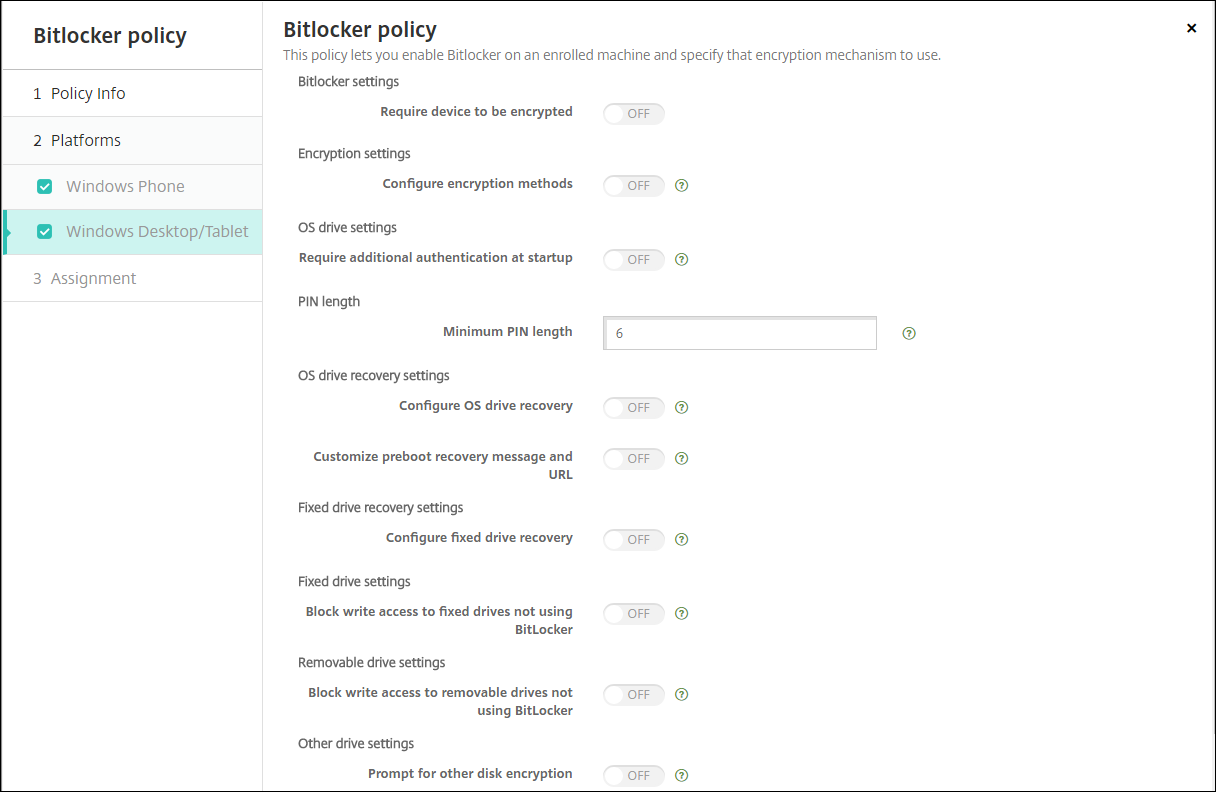
-
Require device to be encrypted: Determines whether to prompt users to enable BitLocker encryption on the Windows Desktop or Tablet. If On, device shows a message after enrollment completes, indicating that the enterprise requires device encryption. If Off, the user isn’t prompted and BitLocker uses the policy settings. Defaults to Off.
-
Configure encryption methods: Determines the encryption methods to use for specific drive types. If Off, the BitLocker wizard prompts the user for the encryption method to use for a drive type. The encryption method for all drives defaults to XTS-AES 128 bit. The encryption method for removable drives defaults to AES-CBC 128-bit. If On, BitLocker uses the encryption method specified in the policy. If On, these extra settings appear: Operating system drive, Fixed drive, and Removable drive. Choose the default encryption method for each drive type. Defaults to Off.
-
Require additional authentication at startup: Specifies the additional authentication required during device startup. Also specifies whether to allow BitLocker on devices that don’t have a TPM chip. If Off, devices without TPM can’t use BitLocker encryption. For information about TPM, see the Microsoft article, Trusted Platform Module Technology Overview. If On, the following extra settings appear. Defaults to Off.
-
Block BitLocker on devices without TPM chip: On a device with no TPM chip, BitLocker requires users to create an unlock password or startup key. The startup key is stored in a USB drive, which the user must connect to the device before startup. The unlock password is a minimum of eight characters. Defaults to Off.
-
TPM startup: On a device with TPM, there are four unlock modes: TPM-only, TPM + PIN, TPM + Key, and TPM + PIN + Key. TPM startup is for the TPM-only mode, in which encryption keys are stored in the TPM chip. This mode doesn’t require a user to provide more unlock data. The user device automatically unlocks during restart, using the encryption key from the TPM chip. Defaults to Allow TPM.
-
TPM startup PIN: This setting is the TPM + PIN unlock mode. A PIN can have up to 20 digits. Use the Minimum PIN length setting to specify the minimum PIN length. A user configures a PIN during BitLocker setup and provides the PIN during device startup.
-
TPM startup key: This setting is the TPM + Key unlock mode. The startup key is stored in a USB or other removable drive, which the user must connect to the device before startup.
-
TPM startup key and PIN: This setting is the TPM + PIN + Key unlock mode.
If the unlock succeeds, the operating system starts loading. If the unlock fails, the device enters recovery mode.
-
-
Minimum PIN length: The minimum length of the TPM startup PIN. Defaults to 6.
-
Configure OS drive recovery: If the unlock step fails, BitLocker prompts the user for the configured recovery key. This setting configures the operating system drive recovery options available to users if they don’t have the unlock password or USB startup key. Default is Off.
-
Allow certificate based data recovery agent: Specifies whether to allow a certificate-based data recovery agent. Add a data recovery agent from Public Key Policies, which is in the Group Policy Management Console (GPMC) or in the Local Group Policy Editor. For more information about data recovery agents, see the Microsoft article, BitLocker Group Policy settings. Default is Off.
-
Create 48-bit recovery password for OS drive recovery: Specifies whether to allow or require users to use a recovery password. BitLocker generates the password and stores it in a file or Microsoft Cloud account. Default is Allow 48-digit password.
-
Create 256-bit recovery key: Specifies whether to allow or require users to use a recovery key. A recovery key is a BEK file, which is stored on a USB drive. Default is Allow 256-bit recovery key.
-
Hide OS drive recovery options: Specifies whether to show or hide recovery options in the BitLocker interface. If On, no recovery options appear in the BitLocker interface. In that case, register the device to Active Directory, save the recovery options to Active Directory, and set Save recovery info to AD DS to On. Default is Off.
-
Save recovery info to AD DS: Specifies whether to save the recovery options to Active Directory Domain Services. Default is Off.
-
Configure recovery info stored in AD DS: Specifies whether to store the BitLocker recovery password or the recovery password and the key package in Active Directory Domain Services. Storing the key package supports recovering data from a drive that is physically corrupted. Default is Backup recovery password.
-
Enable BitLocker after storing recovery info in AD DS: Specifies whether to prevent users from enabling BitLocker unless the device is domain-connected and the backup of BitLocker recovery information to the Active Directory succeeds. If On, a device must be domain-joined before starting BitLocker. Default is Off.
-
-
Customize preboot recovery message and URL: Specifies whether BitLocker shows a customized message and URL on the recovery screen. If On, the following extra settings appear: Use default recovery message and URL, Use empty recovery message and URL, Use custom recovery message, and Use custom recovery URL. If Off, the default recovery message and URL display. Default is Off.
-
Configure fixed drive recovery: Configures the recovery options to users for a BitLocker-encrypted fixed drive. BitLocker doesn’t display a message to users about fixed drive encryption. To unlock a drive during startup, a user provides a password or smart card. The startup’s unlock settings, which aren’t in this policy, appear in the BitLocker interface when a user enables BitLocker encryption on a fixed drive. For information about the related settings, see Configure OS drive recovery, earlier in this list. Default is Off.
-
Block write access to fixed drives not using BitLocker: If On, users can write to fixed drives only when those drives are encrypted with BitLocker. Default is Off.
-
Block write access to removable drives not using BitLocker: If On, users can write to removable drives only when those drives are encrypted with BitLocker. Configure this setting according to whether your organization allows write access on other organization removable drives. Default is Off.
-
Prompt for other disk encryption: Allows you to disable the warning prompt for other disk encryption on devices. Defaults to Off.
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.