Always On before Windows Logon
The Secure Private Access Always On connectivity ensures that a managed device is always connected to an enterprise network before (machine tunnel only) and after Windows Logon. The Always On feature establishes a machine-level VPN tunnel before a user logs in to a Windows system. After the user logs on, the machine-level VPN tunnel is replaced by a user-level VPN tunnel. The application access is based on policies assigned to the machine for the machine-level tunnel and to the user for the user-level tunnel.
The Secure Private Access Always On before Windows Logon (machine-tunnel) feature is supported on the following machines:
- Active Directory domain joined Windows machines
- Microsoft Entra ID hybrid domain joined Windows machines
The Always On before Windows Logon is authenticated by using the computer device certificate-based authentication with Active Directory.
The device certificate is issued by an Active Directory Enterprise Certificate Authority (CA). The device certificate is unique for each domain joined Windows machine.
Note:
- The one-tier to multi-tier Microsoft Enterprise Certification Authority is supported.
-
The Secure Private Access Always On after Windows Logon (user tunnel) is achieved by one of the following auto logon authentication methods for Active Directory:
- Single sign-on (SSO) to Citrix Secure Access™ client using the Active Directory credentials provided during Window Logon. SSO does not work if a second factor is configured.
- Kerberos-based SSO with Citrix Gateway / Adaptive Authentication configuration. For details, see Connect an on-premises Citrix Gateway as an identity provider to Citrix Cloud and Provision Adaptive Authentication and Provisioning Adaptive Authentication.
-
The Secure Private Access Always On after Windows Logon (user tunnel) is achieved by the following autologon authentication method for Microsoft Entra ID hybrid joined machines, SSO with Primary Refresh Token (PRT) of Microsoft Entra ID authentication.
Disable ADFS by navigating to Workspace Configuration\Customize\Preferences-Federated Identity Provider Sessions and disable the toggle.
How does Always On work?
The following diagram illustrates the workflow of the Always On before Windows Logon feature.
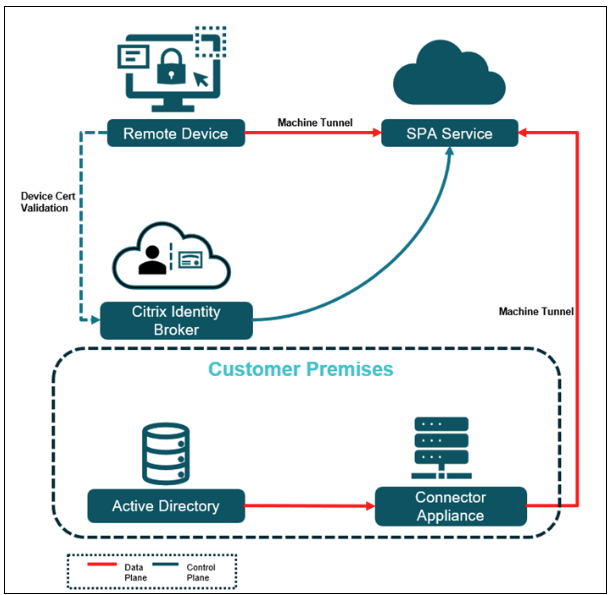
- The Citrix Identity Broker verifies the device certificate to authenticate the device immediately after bootup. The following are the device certificate verification steps:
- The client presents the device certificate based on CA certificates uploaded to the Secure Private Access admin console.
- The Citrix identity provider does device certificate-based authentication.
- The Citrix identity provider verifies the following details:
- Device certificate signature
- CRL-based device certificate revocation check
- Validate device certificate against Active Directory Computer object
- On successful verification of the device certificate, a secure machine tunnel is established between the device and the resources in the corporate premises based on the access policy.
- On allowing access to Active Directory, Windows Logon authenticates user credentials with Active Directory and supports password expiry and password change.
- After Windows Logon, the machine-level tunnel is automatically replaced by the user tunnel with autologon. On user tunnel failure/disconnect, the connection falls back to the machine tunnel.
- The autologin feature is supported for the Active Directory and hybrid Microsoft Entra ID environment.
Active Directory and Microsoft Entra ID Hybrid AD configuration
The Windows machines must be Active Directory or Microsoft Entra ID Hybrid joined as a prerequisite for Always On. The Active Directory Enterprise Certificate Authority is required to issue the device certificate for Always On machine authentication. The certificate revocation is verified based on the CDP extension with LDAP URL configuration in the certificate authority.
Device certificate enrollment configuration
The following steps are involved in device certificate enrollment:
- The Active Directory Enterprise Certificate Authority issues a Device Certificate for machine authentication.
-
The certificate authority must have the LDAP URL published for the CRL distribution point (CDP) extension.
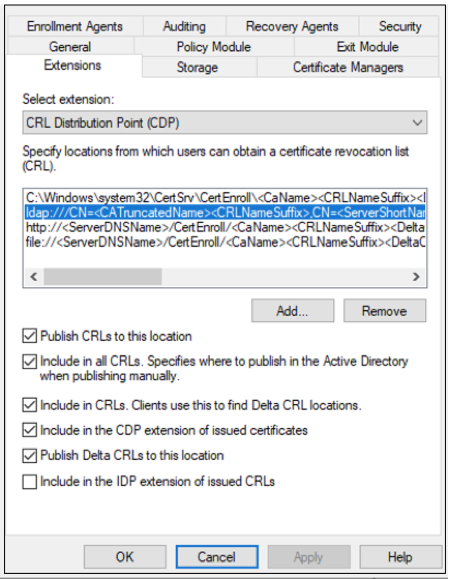
-
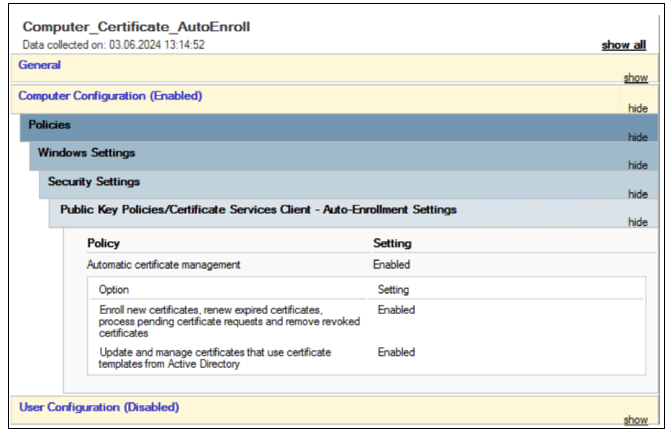
A certificate template in this certificate authority must be created to enroll the device certificate with the following details.
- Open the certification template snap-in and duplicate either the Computer or Workstation Authentication (preferred) template.
- Provide a new name for the certificate.
-
Switch to the Subject Name tab, change the Subject name format setting to Common name, and check User Principal Name (UPN) to be included in the alternate subject name.
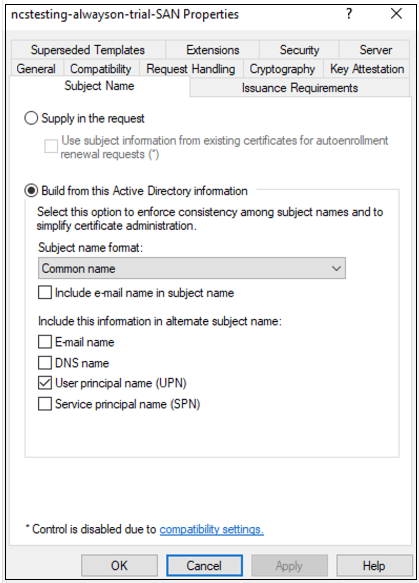
-
Switch to the Security tab and add a security group (containing only computer accounts) to which you want to autoenroll the new certificate template. Select the added group and select Allow for Autoenroll.
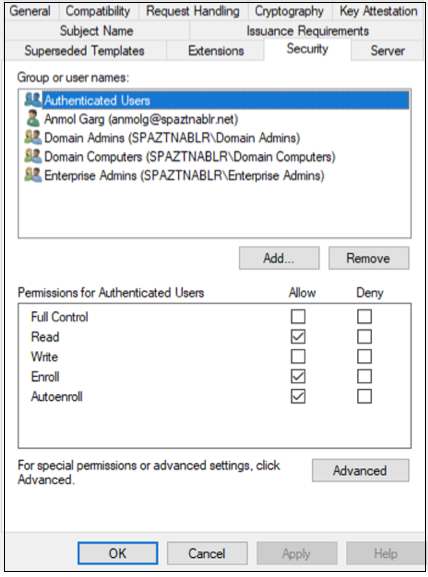
Note:
In the preceding image, Authenticated Users (all computer objects) are permitted to enroll/autoenroll the new certificate template.
- (Optional) Create a group policy object (GPO) that allows for auto certificate enrollment and bind it to an organization unit (OU) or at the domain level.
Secure Private Access configuration
Configure Always On before Windows Logon (machine tunnel)
-
In the Secure Private Access admin console, navigate to Settings > Certificate Store.
Note:
We recommend that you use the Machine Based Authentication option found under Settings > Certificate Store instead of Settings > Machine Based Authentication. The option Settings > Machine Based Authentication is scheduled for removal in the upcoming service release.
-
In the Certificates page, click the Machine Authentication tab.
The Enforce machine level tunnel before users log on toggle switch is enabled by default for the Always On before Windows Logon feature.
- Upload a CA certificate: Click Add certificate, select the certificate, and click Open.
- In Name, enter a name for the certificate.
-
In Certificate file, browse to your local drive and upload the certificate file.
- Certificates for both root CA and intermediate CA are supported. The certificates to be uploaded must be in the PEM format and include the whole chain. The certificate must be generated starting from the intermediate certificate all the way to the root CA.
-
If the certificate is in a CER format, run the following command on a Linux or Mac terminal to convert the certificate into PEM format. After converting the certificate into PEM format, upload the certificate in the Secure Private Access user interface.
openssl x509 -in /Users/t_abhishes2/Downloads/cert12.crt out/Users/t_abhishes2/Downloads/cer_pem12_ao.pem
-
Click Save.
The certificate is added to the list of available certificates in the Machine authentication tab.
- Create a TCP/UDP application to access Active Directory as a TCP/UDP server. For example, Active Directory domain, IP address, and Ports. This is for Windows user logon with AD credentials. For details on creating a TCP/UDP app, see Admin Configuration – Citrix Secure Access client-based access to TCP/UDP apps.
- Create additional applications if needed to be accessed before Windows Logon and before user-level tunnel migration.
-
Create an access policy and provide access for the domain joined machine or its AD group.
- In the Secure Private Access admin console, click Access Policies, and then click Create Policy.
- Enter the policy name and description of the policy.
- In Applications, select the app or set of apps for which this policy must be enforced.
-
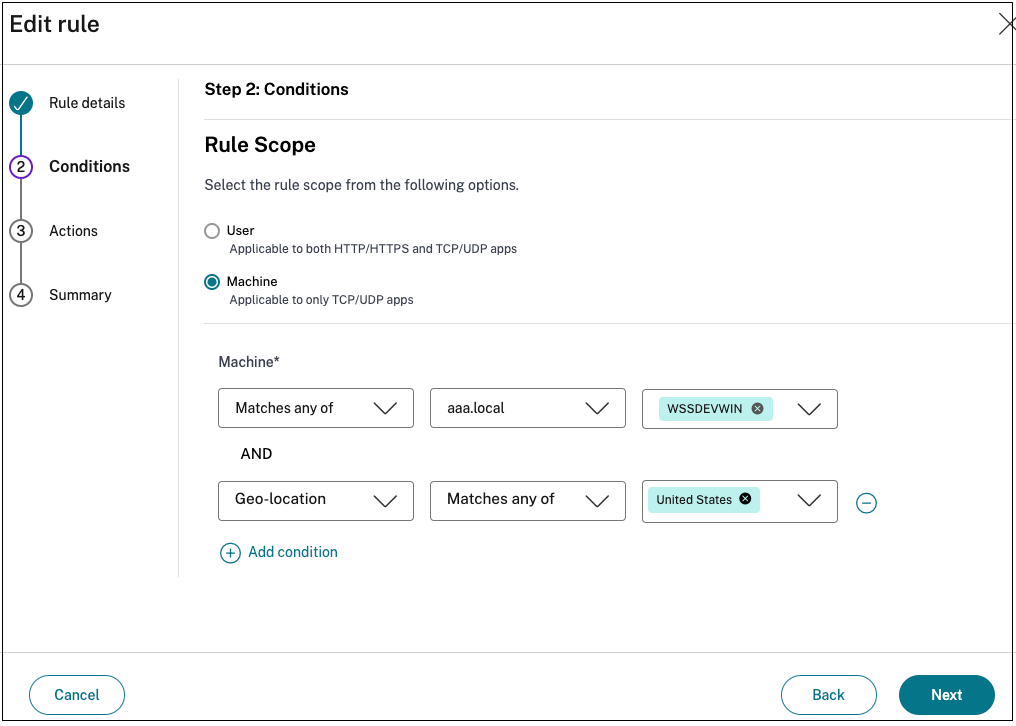
Click Create Rule to create rules for the policy.
- Enter the rule name and a brief description of the rule, and then click Next.
-
In the Rule scope, select Machine.
Note:
When you select a machine, the access privileges are limited as the machine-level tunnel is based on single-factor authentication.
- Select the matching condition, and the domain, and search for the machine/groups to which the policy must be applied. Add more conditions if needed. When finished, click Next.
- Matches any of – Only the machines/groups that match any of the names listed in the field and belonging to the selected domain are allowed access.
-
Does not match any – All machines/groups except those listed in the field and belonging to the selected domain are allowed access.
-
Select one of the following actions to be applied based on the condition evaluation.
- Allow access
- Deny access
-
Click Next, and then click Finish.
-
(Optional) Create additional rules for the geo-location and network location, and so on. For details, see Configure an access policy.
The policy is listed on the Access Policies page. A priority order is assigned to the policy, by default. The priority with a lower value has the highest preference. The policy with the lowest priority number is evaluated first. If the policy does not match the conditions defined, the next policy is evaluated. If the conditions match, the other policies are skipped.
Connector Appliance Configuration
Connector Appliance performs device certificate validation, certificate revocation check (CRL), and device object verification for Always On Device certificate authentication. Connector Appliance must be domain joined to the Active Directory domain for Device certificate authentication to be supported.
Client configuration
- The Windows machine that needs Always On support must be domain joined to Active Directory or Entra ID hybrid.
- The Windows machine must enroll a device certificate from the Enterprise Certificate Authority for Secure Private Access Always On.
-
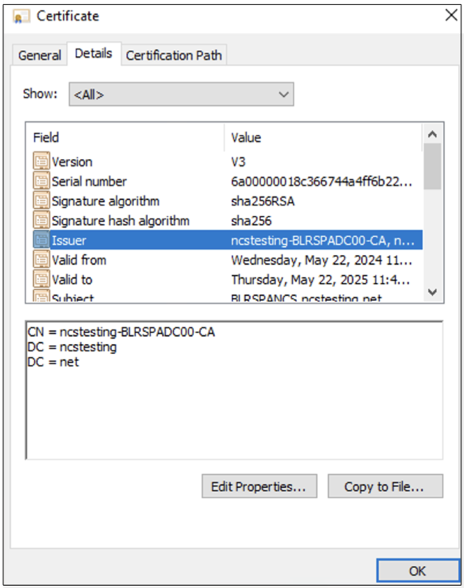
The device certificate attributes must include the following details.
-
The issuer name in the device certificate must match the common name of the CA certificate uploaded to the Secure Private Access admin console.
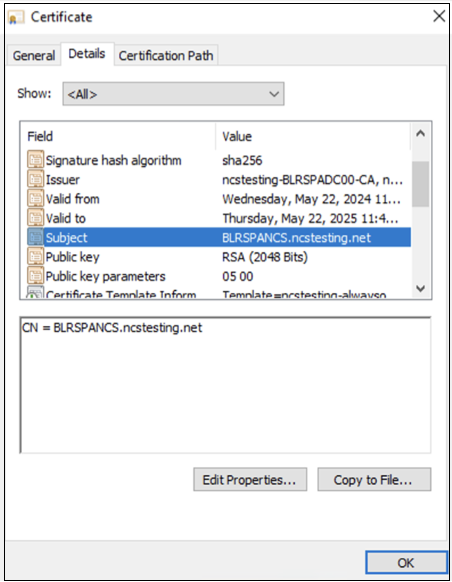
-
Subject must contain the common name of the computer.
-
Subject Alternate Name (SAN) must contain the UPN of the computer.
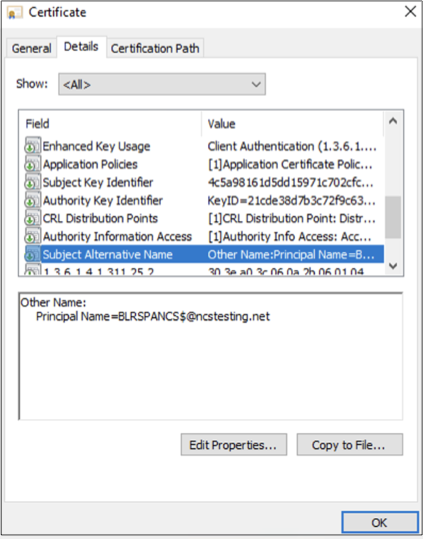
-
CRL distribution point must contain the appropriate LDAP URL.
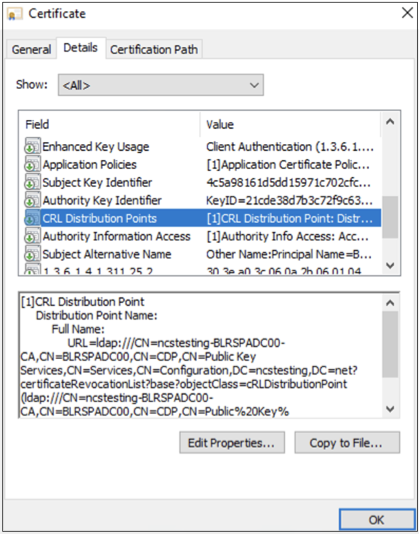
-
The certification path must be appropriate to the certificate authority chain.
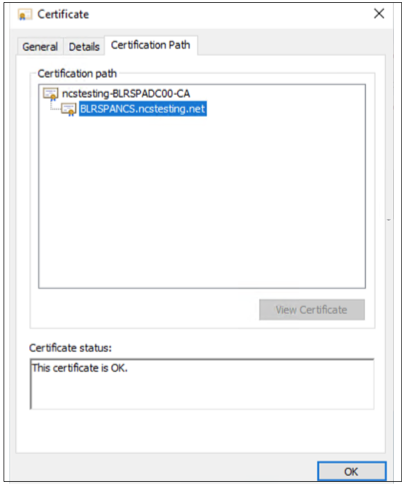
-
-
Install the Citrix Secure Access client for Always On.
-
The following registries must be created on the client to enable Always On before Windows Logon.
-
CloudAlwaysOnURL in HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client.
Registry Type - STRING
Registry Value -
<Customer Workspace FQDN>(For example, company.cloud.com) -
AlwaysOnService in HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client.
Registry Type - DWORD
Registry Value - 0x00000002
-
Configure Always On after Windows Logon (machine/user tunnel)
After successful Windows Logon, the machine tunnel continues until the user login is successful with the Citrix Secure Access client.
- If user auto login is successful, the machine tunnel is migrated to a user tunnel.
- If user auto login fails, the machine tunnel continues.
- If the user tunnel gets disconnected, the connection automatically falls back to the machine tunnel.
User Autologon after Windows Logon is supported for the following authentication methods in the Workspace authentication configuration.
- Workspace authentication with Active Directory (with no second factor) - AD credential SSO
- Workspace authentication with Citrix Gateway/Adaptive Auth configured with Kerberos SSO
- Workspace authentication with Azure Active Directory (SSO with Primary Refresh Token (PRT) of Microsoft Entra ID authentication).
Note:
Disable ADFS by navigating to Workspace Configuration\Customize\Preferences-Federated Identity Provider Sessions and disable the toggle.
Limitations
- Computer UPN host name must not exceed 15 characters.
- Windows Auto Logon (First Time User (FTU)) case is supported only if the machine is domain joined and the device certificate is present.
- The Always On before Windows Logon feature is supported only on Windows 10 or later versions.
- The Always On before Windows Logon feature is not supported for Windows Server Operating Systems.
- The Always On before Windows Logon feature is not supported with Cloud Connector. Even if you have not selected Connector Appliance as a preferred connector, the machine tunnel traffic goes via Connector Appliance.