Support for server-to-client connections - Preview
In a traditional client-server setup, the remote users can access resources in customer resource locations using the HTTP, TCP, and UDP connections. However, there are scenarios where the server or the back-end system needs to initiate a connection with the remote client devices (example laptops, smart phone, tablet) for tasks such as push configurations, remote assistance, application access, or app installation while safeguarding user privacy and security. Secure Private Access supports server-to-client connections wherein the servers in the customer’s resource location can establish a TCP/UDP connection with the remote client.
- To enable server-to-client connection, Secure Private Access introduces the server-to-client app. This app can be configured with the client details (port, protocol) and the back-end server’s IP CIDR range.
- After the server-to-client app type is created, then appropriate access policies must be configured for these applications to enable server-to-client connections.
How server-to-client connection works
The following diagram displays a sample server-to-client connection architecture.
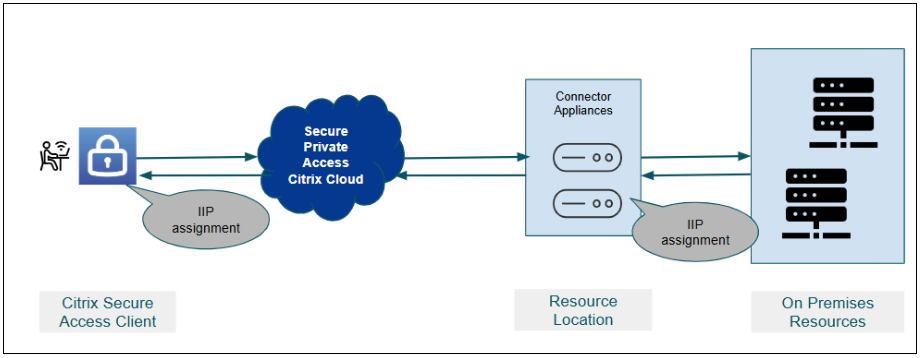
The following steps illustrate the server-to-client connection workflow:
- When a user logs in to the Citrix Secure Access™ client, the user is assigned an Internal IP address from the designated client internal IP address pool. This assignment is based on the configured resource location, IP CIDR, and user context in the IP address pool configuration.
- This assigned IP address is then associated with a specific Connector Appliance within the configured resource location and IP pool. This Connector Appliance owns and manages connections related to this IP address for back-end customer resource location.
- The back-end server initiates a TCP/UDP connection to the remote client using the assigned client internal IP address using the port of the client application specified in the server-to-client application configuration.
- The connector communicates with Secure Private Access to establish a connection with the client.
- The Secure Private Access verifies if the back-end server is configured in the server-to-client application, then evaluates the relevant access policy to determine whether to allow or block access to the client machine.
- If the policy allows access, then Secure Private Access connects with the remote client machine. If the client machine is domain-joined, then the FQDN of that machine is registered with the IIP address. The machine can be accessed either by FQDN or the internal IP address.
- When a user logs out, the assigned internal IP address is released both from the Connector Appliance and the active session. If the same user logs in again within 15 days, the user gets the same IP address, else it is released for other user’s usage.
Create a server-to-client app
Prerequisites
- The client internal IP address pool is created. The IP address pool is essential for assigning a unique IP address to a user and the associated device. For details, see Client internal IP address pools.
- The customer’s admin must allocate a free Intranet IP CIDR subnet for the resource location network. This IP CIDR must not conflict with other resource IP addresses.
- The customer’s admin must determine which group/context users are allocated the Intranet IP address from which resource location. It is recommended to maintain a user-to-IP address ratio of 1:3. That is if the number of users logging in is 1000, it is recommended to allocate 3000 IP addresses in the Client IP Pool.
- The free IIP subnet and the connector’s primary IP address must belong to the same network and subnet.
- Interconnections must be maintained between resource locations to allow servers in other locations (not configured in the IP pool) to connect to the client.
-
Ensure that you use the Citrix Secure Access clients versions that support server-to-client apps.
- Windows 24.11.1.17 and later
- macOS 25.01.1 and later
- Linux 25.2.2 and later
Perform the following steps to configure server to client TCP/UDP apps
- Log in to Citrix Cloud and select Secure Private Access.
-
Click Applications > App Configuration and then click Add an app.
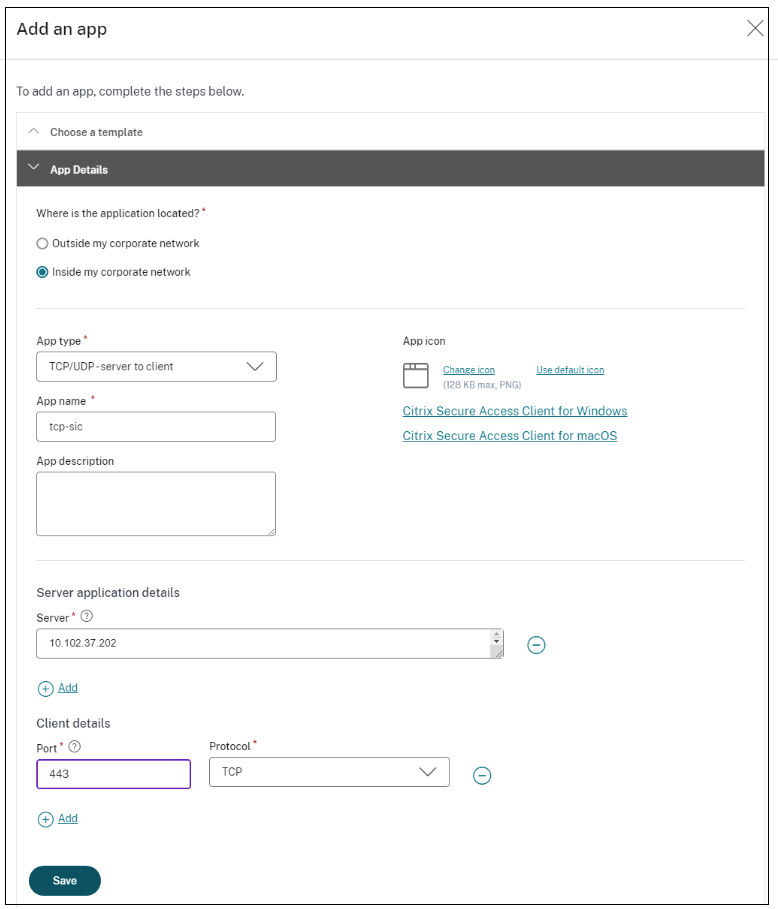
- Select the location Inside my corporate network.
-
Enter the following details:
- App type – Select TCP/UDP - server to client.
- App name – Name of the application.
- App description – Description of the app you are adding. This field is optional.
- Server - IP address range of the back-end server that can establish a connection with the client machine. This ensures that only the servers with IP addresses within this range can access the client’s ports.
- Port – The client machine’s port number to which the back-end server can initiate a connection.
- Protocol – TCP or UDP.
- Click Add to add more servers and ports.
- Click Save. The app is added to the App Configuration page.
You can edit or delete an app from the Applications page after you have configured the application. To do so, click the ellipsis button in line with the app and select the actions accordingly.
After you create the server-to-client app, create access policies as per the requirement.
Note:
All the existing access policies are supported for server-to-client applications. The server-to-client access is allowed to users whose context is evaluated to “Allow” for the configured access policy.