Connection to Google cloud environments
Create and manage connections and resources describes the wizards that create a connection. The following information covers details specific to Google cloud environments.
Note:
Before creating a connection to Google cloud environments, you need to first finish setting up your Google cloud account as a resource location. See Google Cloud virtualization environments.
Add a connection
In Studio, follow the guidance in Create and manage connections and resources. The following description guides you through setting up a hosting connection:
- From Studio, select Hosting in the left pane.
- Select Add Connection and Resources in the action bar.
-
On the Connection page, select Create a new Connection and Citrix provisioning™ tools, and then select Next.
- Zone name. Select a zone (equivalent to a resource location) where you want your host resources to reside. Zones are created automatically when you create a resource location and add a Cloud Connector to it. For more information, see Zones.
- Connection type. Select Google Cloud Platform from the menu.
-
Service account key. Import the key contained in your Google credential file (.json). You can either paste the key from the credential file or browse to the credential file. To paste the key:
- Locate your credential file
- Open the file with Notepad (or any text editor)
- Copy the content.
- Return to the Connection page, select Add key, paste the content, and then select Done.
- Service account ID. The field automatically populates with the information from the service account key.
- Connection name. Type a name for the connection.
-
Route traffic through Citrix Cloud Connectors. To route the API requests through an available Citrix Cloud Connector™, select this checkbox. When Cloud Connectors have no direct internet access, you can select Use the proxy configured on Citrix Cloud Connectors to ensure GCP connectivity works properly through Citrix Cloud Connectors. You can also select Enable Google Cloud Build to use private pools checkbox for an additional layer of security.
Alternatively, you can enable this feature using PowerShell. For more information, see Create a secure environment for GCP-managed traffic.
Note:
This option is available only when there are active Citrix Cloud™ Connectors in your deployment. Currently, this feature is not supported for Connector Appliances.
- Create virtual machines using. Select a method to create virtual machines.
-
On the Region page, select a project name from the menu, select a region containing the resources you want to use, and then select Next.
-
On the Network page, type a name for the resources, select a virtual network from the menu, select a subset, and then select Next. The resource name helps identify the region and network combination. Virtual networks with the (Shared) suffix appended to their name represent shared VPCs. If you configure a subnet-level IAM role for a shared VPC, only specific subnets of the shared VPC appear on the subnet list.
Note:
- The resource name can contain 1–64 characters, and cannot contain only blank spaces or the characters
\ / ; : # . * ? = < > | [ ] { } " ' ( ) ' ).
- The resource name can contain 1–64 characters, and cannot contain only blank spaces or the characters
- On the Summary page, confirm the information and then select Finish to exit the Add Connection and Resources window.
After you create the connection and resources, the connection and resources you created are listed. To configure the connection, select the connection and then select the applicable option in the action bar.
Similarly, you can delete, rename, or test the resources created under the connection. To do so, select the resource under the connection and then select the applicable option in the action bar.
Create a secure environment for GCP managed traffic
You can allow only private Google access to your Google Cloud projects. This implementation enhances security to handle sensitive data. To do this:
- Install Cloud Connectors in the VPC where you want to enforce VPC service controls. See VPC Service Controls for more information.
- Add
ProxyHypervisorTrafficThroughConnectorinCustomPropertiesin case of Citrix Cloud deployment. If you are using a private worker pool, addUsePrivateWorkerPoolinCustomProperties. For information on the private worker pool, see Private pools overview.
Note:
Currently, this feature is not supported for Connector Appliance.
Requirements to create a secure environment for GCP managed traffic
The requirements to create a secure environment for GCP managed traffic are:
- Ensure that the hosting connection is in maintenance mode when updating the custom properties.
- To use private worker pools, the following changes are required:
- For Citrix Cloud Service Account, add the following IAM roles:
- Cloud Build Service Account
- Compute Instance Admin
- Service Account User
- Service Account Token Creator
- Cloud Build WorkerPool Owner
- Create the Citrix Cloud Service Account in the same project that you use for creating a hosting connection.
-
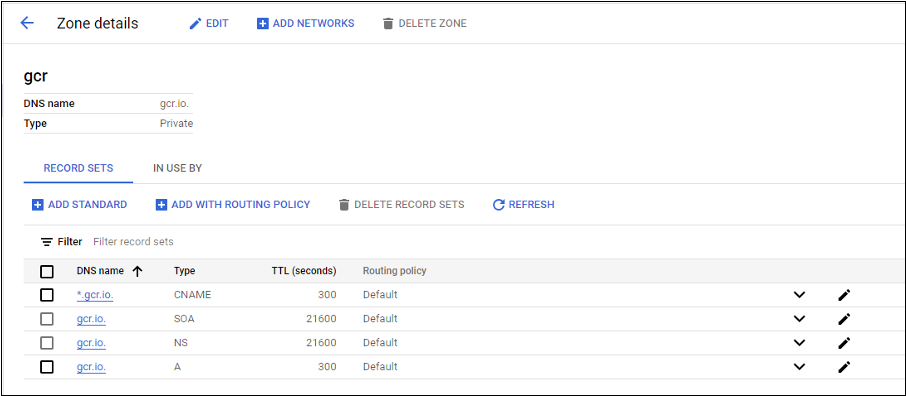
Set up DNS zones for
private.googleapis.comandgcr.ioas described in DNS configuration.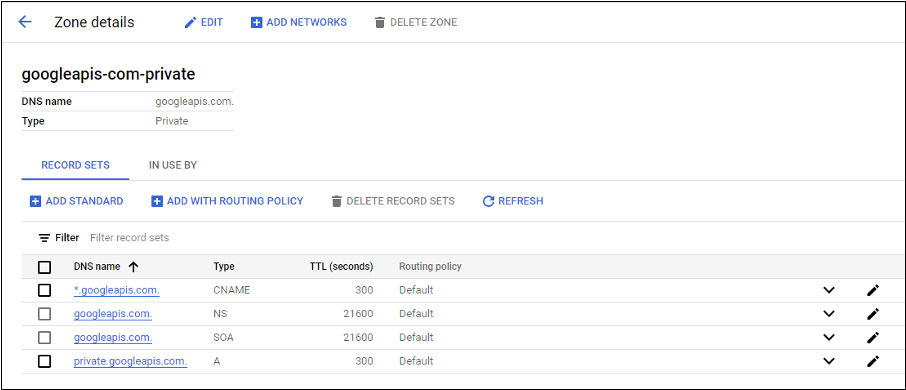
-
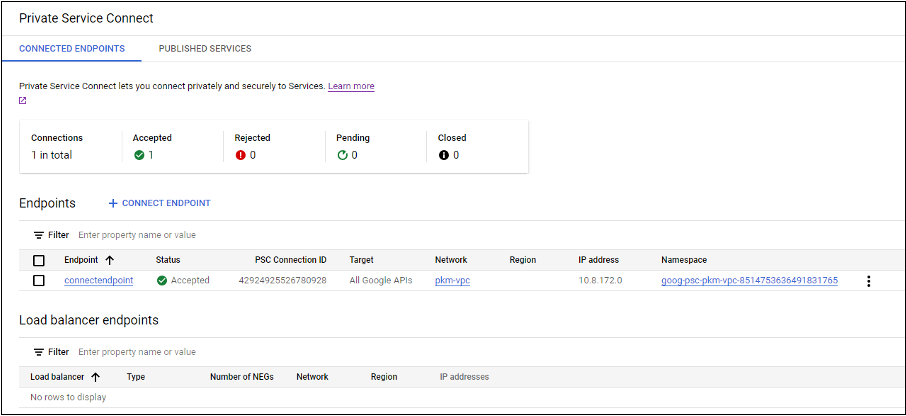
Set up private Network Address Translation (NAT) or use private service connect. For more information, see Access Google APIs through endpoints.
-
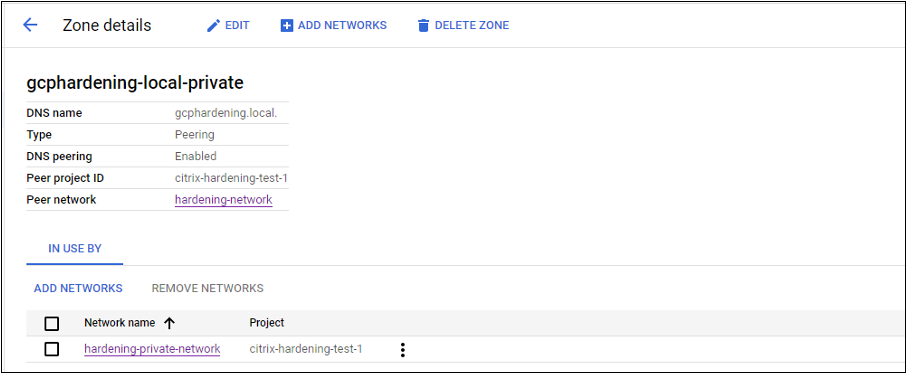
If using a peered VPC, create a Cloud DNS zone peering to the peered VPC. For more information, see Create a peering zone.
-
In VPC service controls, set up Egress rules so that the APIs and VMs can talk to the internet. Ingress rules are optional. For example:
Egress Rule 1 From: Identities:ANY_IDENTITY To: Projects = All projects Service = Service name: All services <!--NeedCopy-->
- For Citrix Cloud Service Account, add the following IAM roles:
Enable the proxy
To enable the proxy, set the custom properties as follows on the host connection:
- Open a PowerShell window from the Delivery Controller host or use the Remote PowerShell SDK. For more information on Remote PowerShell SDK, see SDKs and APIs.
-
Run the following commands:
Add-PSSnapin citrix*cd XDHyp:\Connections\dir
- Copy the
CustomPropertiesfrom the connection to a notepad. -
Append the property setting as follows:
-
In case of cloud deployment (using public pools): Append property setting
<Property xsi:type="StringProperty" Name="ProxyHypervisorTrafficThroughConnector" Value="True"/>to theCustomPropertiesto enable the proxy. For example:<CustomProperties xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://schemas.citrix.com/2014/xd/machinecreation"> <Property xsi:type="StringProperty" Name="ProxyHypervisorTrafficThroughConnector" Value="True"/> </CustomProperties> <!--NeedCopy-->Allow ingress rule for Cloud Build Service Account in VPC service perimeter. For example:
Ingress Rule 1 From: Identities: <ProjectID>@cloudbuild.gserviceaccount.com Source > All sources allowed To: Projects = All projects Services = Service name: All services <!--NeedCopy-->For information on VPC service perimeter, see Service perimeter details and configuration.
-
In case of a private worker pool in a cloud deployment, append property setting
<Property xsi:type="StringProperty" Name="ProxyHypervisorTrafficThroughConnector" Value="True"/>and<Property xsi:type="StringProperty" Name="UsePrivateWorkerPool" Value="True"/>to theCustomPropertiesto enable the proxy. For example:<CustomProperties xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://schemas.citrix.com/2014/xd/machinecreation"> <Property xsi:type="StringProperty" Name="ProxyHypervisorTrafficThroughConnector" Value="True"/> <Property xsi:type="StringProperty" Name="UsePrivateWorkerPool" Value="True"/> </CustomProperties> <!--NeedCopy-->
-
- In the PowerShell window, assign a variable to the modified custom properties. For example:
$customProperty = '<CustomProperties…</CustomProperties>'. - Run
$gcpServiceAccount = "<ENTER YOUR SERVICE ACCOUNT EMAIL HERE>". - Run
$gcpPrivateKey = "<ENTER YOUR SERVICE ACCOUNT PRIVATE KEY HERE AFTER REMOVING ALL INSTANCES OF \n >". - Run
$securePassword = ConvertTo-SecureString $gcpPrivateKey -AsPlainText -Force. -
Run the following to update an existing host connection:
Set-Item -PassThru -Path @('XDHyp:\\Connections\\<ENTER YOUR CONNECTION NAME HERE>') -SecurePassword $securePassword -UserName $gcpServiceAccount -CustomProperties $customProperty <!--NeedCopy-->
Option to use system proxy on Citrix Cloud Connectors for redirected GCP API traffic
To route all external traffic through a non-transparent proxy, configure the host connection with the custom property UseSystemProxyForHypervisorTrafficOnConnectors. This redirects GCP API internet traffic on Citrix Cloud Connectors through the system proxy.
Do the same steps as outlined in Enable the proxy to configure the host connection with the custom property. However, make sure to append property setting <Property xsi:type="StringProperty" Name="UseSystemProxyForHypervisorTrafficOnConnectors" Value="True" /> to the CustomProperties to enable the proxy.
<Property xsi:type="StringProperty" Name="UseSystemProxyForHypervisorTrafficOnConnectors" Value="True" />
<!--NeedCopy-->
Example:
<CustomProperties xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://schemas.citrix.com/2014/xd/machinecreation">
<Property xsi:type="StringProperty" Name="ProxyHypervisorTrafficThroughConnector" Value="True"/>
<Property xsi:type="StringProperty" Name="UsePrivateWorkerPool" Value="True"/>
<Property xsi:type="StringProperty" Name="UseSystemProxyForHypervisorTrafficOnConnectors" Value="True" />
</CustomProperties>
<!--NeedCopy-->
Note:
After you set this property, the proxy configured in the
netsh winhttpsettings on the Citrix Cloud Connectors is used for outbound traffic to the cloud service provider.
Specify CMEK global and regional key
Note:
Support for CMEK in GCP is currently under Preview.
There are two types of customer-managed encryption keys (CMEK) in GCP:
- Regional: Encryption keys that can only be used by resources in the same region.
- Global: Encryption keys that can be used by resources from multiple regions.
You can browse and use global or regional customer-managed encryption keys (CMEK) from all projects that are accessible to the service account. You can then use the key to create a CMEK enabled MCS machine catalog and update an existing CMEK enabled MCS machine catalog using Set-ProvScheme command. For information creating a CMEK enabled catalog using PowerShell, see Create a catalog with CMEK using custom properties.
For this feature, you need additional permissions for the following two service accounts:
- The service account of the current project with which the hosting connection is created.
- The Compute Engine Service Agent of the current project (that has the email:
service-PROJECT_NUMBER@compute-system.iam.gserviceaccount.com). For more information, see Compute Engine Service Agent.
In Service accounts, you must assign the following roles in the project that has crypto keys that you want to use (for example, shared project):
- Cloud KMS Viewer
- Cloud KMS CryptoKey Encrypter/Decrypter
If you do not assign to the roles, then make sure that you have the following permissions:
- resourcemanager.projects.get
- cloudkms.keyRings.list
- cloudkms.keyRings.get
- cloudkms.cryptoKeys.get
- cloudkms.cryptoKeys.list
- cloudkms.cryptoKeyVersions.useToDecrypt
- cloudkms.cryptoKeyVersions.useToEncrypt
List the encryption keys
You can list the global and regional encryption keys within the same project and all other accessible projects using the PowerShell commands. To do this:
- Open a PowerShell window from the Delivery Controller™ host or remote PowerShell.
- Run the command
asnp citrix*to load Citrix-specific PowerShell modules. -
Run the following command to list the encryption keys. Example:
-
To list contents of
encryptionKeysfolder:Get-ChildItem XDHyp:\HostingUnits\my-hostingunit\encryptionKeys.folder <!--NeedCopy--> -
To get global encryption keys within the same project:
Get-Item XDHyp:\HostingUnits\my-hostingunit\encryptionKeys.folder\myglobalkeyring.globalkeyring\myglobalkey.cryptokey <!--NeedCopy--> -
To get regional encryption keys within the same project:
Get-Item XDHyp:\HostingUnits\my-hostingunit\encryptionKeys.folder\regional-ring.keyring\shared-key.cryptokey <!--NeedCopy--> -
To get global encryption keys from another accessible project (for example: myanotherproject):
Get-Item XDHyp:\HostingUnits\my-hostingunit\encryptionKeys.folder\myanotherproject.project\shared-global-ring.globalkeyring\shared-key.cryptokey <!--NeedCopy--> -
To get regional encryption keys from another accessible project (for example: myanotherproject):
Get-Item XDHyp:\HostingUnits\my-hostingunit\encryptionKeys.folder\myanotherproject .project.project\shared-uscentral.keyring\shared-uscentral-key.cryptokey <!--NeedCopy-->
-
Note:
- The extension of the key ring inventory item for a global key ring is
.globalkeyring.- The id of global key rings has the word
globalin it.
Required GCP permissions
This section has the complete list of GCP permissions. Use the complete set of permissions as given in the section for the functionality to work correctly.
Note:
GCP is introducing changes to Cloud Build Services’s default behavior and use of service accounts after April 29, 2024. For more information, see Cloud Build Service Account Change. Your existing Google projects with Cloud Build API enabled before April 29, 2024 are not affected by this change. However, if you want to have existing Cloud Build Service behavior after April 29, you can create or apply the organization policy to disable the constraint enforcement before you enable the API. If you set the new organization policy, you can still follow the existing permissions in this section and the items that are marked Before Cloud Build Service Account Change. If not, then follow the existing permissions and items that are marked After Cloud Build Service Account Change.
Creating a host connection
-
Minimum permissions required for Citrix Cloud Service Account in Provisioning project:
compute.instanceTemplates.list compute.instances.list compute.networks.list compute.projects.get compute.regions.list compute.subnetworks.list compute.zones.list resourcemanager.projects.get <!--NeedCopy-->The following Google defined roles have the permissions as listed above:
- Compute Admin
- Cloud Datastore User
-
Additional permissions required for Shared VPC for Citrix Cloud Service Account in Shared VPC project:
compute.networks.list compute.subnetworks.list resourcemanager.projects.get <!--NeedCopy-->The following Google defined roles have the permissions as listed above:
- Compute Network User
-
In Service accounts, you must assign the following roles in the project that has crypto keys that you want to use (for example, shared project):
- Cloud KMS Viewer
- Cloud KMS CryptoKey Encrypter/Decrypter
If you do not assign to the roles, then make sure that you have the following permissions:
- resourcemanager.projects.get
- cloudkms.keyRings.list
- cloudkms.keyRings.get
- cloudkms.cryptoKeys.get
- cloudkms.cryptoKeys.list
- cloudkms.cryptoKeyVersions.useToDecrypt
- cloudkms.cryptoKeyVersions.useToEncrypt
Power management of VMs
Minimum permissions required for Citrix Cloud Service Account in Provisioning project in case of power managed only catalogs:
compute.instanceTemplates.list
compute.instances.list
compute.instances.get
compute.instances.reset
compute.instances.resume
compute.instances.start
compute.instances.stop
compute.instances.suspend
compute.networks.list
compute.projects.get
compute.regions.list
compute.subnetworks.list
compute.zones.list
resourcemanager.projects.get
compute.zoneOperations.get
<!--NeedCopy-->
The following Google defined roles have the permissions as listed above:
- Compute Admin
- Cloud Datastore User
Creating, updating, or deleting VMs
-
Minimum permissions required for Citrix Cloud Service Account in Provisioning project:
cloudbuild.builds.create cloudbuild.builds.get cloudbuild.builds.list compute.acceleratorTypes.list compute.diskTypes.get compute.diskTypes.list compute.disks.create compute.disks.createSnapshot compute.disks.delete compute.disks.get compute.disks.list compute.disks.setLabels compute.disks.use compute.disks.useReadOnly compute.firewalls.create compute.firewalls.delete compute.firewalls.list compute.globalOperations.get compute.images.create compute.images.delete compute.images.get compute.images.list compute.images.setLabels compute.images.useReadOnly compute.instanceTemplates.create compute.instanceTemplates.delete compute.instanceTemplates.get compute.instanceTemplates.list compute.instanceTemplates.useReadOnly compute.instances.attachDisk compute.instances.create compute.instances.delete compute.instances.detachDisk compute.instances.get compute.instances.getSerialPortOutput compute.instances.list compute.instances.reset compute.instances.resume compute.instances.setDeletionProtection compute.instances.setLabels compute.instances.setMetadata compute.instances.setServiceAccount compute.instances.setTags compute.instances.start compute.instances.stop compute.instances.suspend compute.machineTypes.get compute.machineTypes.list compute.networks.list compute.networks.updatePolicy compute.nodeGroups.list compute.nodeTemplates.get compute.projects.get compute.regions.list compute.snapshots.create compute.snapshots.delete compute.snapshots.list compute.snapshots.get compute.snapshots.setLabels compute.snapshots.useReadOnly compute.subnetworks.get compute.subnetworks.list compute.subnetworks.use compute.zoneOperations.get compute.zoneOperations.list compute.zones.get compute.zones.list iam.serviceAccounts.actAs resourcemanager.projects.get storage.buckets.create storage.buckets.delete storage.buckets.get storage.buckets.list storage.buckets.update storage.objects.create storage.objects.delete storage.objects.get storage.objects.list compute.networks.get compute.resourcePolicies.use <!--NeedCopy-->The following Google defined roles have the permissions as listed above:
- Compute Admin
- Storage Admin
- Cloud Build Editor
- Service Account User
- Cloud Datastore User
-
Additional permissions required for Shared VPC for Citrix Cloud Service Account in Shared VPC project to create a hosting unit using VPC and subnetwork from Shared VPC project:
compute.firewalls.list compute.networks.list compute.projects.get compute.regions.list compute.subnetworks.get compute.subnetworks.list compute.subnetworks.use compute.zones.list resourcemanager.projects.get <!--NeedCopy-->The following Google defined roles have the permissions as listed above:
- Compute Network User
- Cloud Datastore User
-
(Before Cloud Build Service Account Change): Minimum permissions required for Cloud Build Service Account in Provisioning project required by Google Cloud Build service when downloading preparation instruction disk to MCS:
-
(After Cloud Build Service Account Change): Minimum permissions required for Cloud Compute Service Account in Provisioning project required by Google Cloud Compute service when downloading preparation instruction disk to MCS:
compute.disks.create compute.disks.delete compute.disks.get compute.disks.list compute.disks.setLabels compute.disks.use compute.disks.useReadOnly compute.images.get compute.images.list compute.images.useReadOnly compute.instances.create compute.instances.delete compute.instances.get compute.instances.getSerialPortOutput compute.instances.list compute.instances.setLabels compute.instances.setMetadata compute.instances.setServiceAccount compute.machineTypes.list compute.networks.get compute.networks.list compute.projects.get compute.subnetworks.list compute.subnetworks.use compute.subnetworks.useExternalIp compute.zoneOperations.get compute.zones.list iam.serviceAccounts.actAs logging.logEntries.create pubsub.topics.publish resourcemanager.projects.get source.repos.get source.repos.list storage.buckets.create storage.buckets.get storage.buckets.list storage.objects.create storage.objects.delete storage.objects.get storage.objects.list <!--NeedCopy-->The following Google defined roles have the permissions as listed above:
- Cloud Build Service Account (After Cloud Build Service Account Change, it is Cloud Compute Service Account)
- Compute Instance Admin
- Service Account User
-
Minimum permissions required for Cloud Compute Service Account in Provisioning project required by Google Cloud Build service when downloading preparation instruction disk to MCS:
resourcemanager.projects.get storage.objects.create storage.objects.get storage.objects.list <!--NeedCopy-->The following Google defined roles have the permissions as listed above:
- Compute Network User
- Storage Account User
- Cloud Datastore User
- (Before Cloud Build Service Account Change): Additional permissions required for Shared VPC for Cloud Build Service Account in Provisioning project required by Google Cloud Build service when downloading preparation instruction disk to MCS:
-
(After Cloud Build Service Account Change): Additional permissions required for Shared VPC for Cloud Compute Service Account in Provisioning project required by Google Cloud Compute service when downloading preparation instruction disk to MCS:
compute.firewalls.list compute.networks.list compute.subnetworks.list compute.subnetworks.use resourcemanager.projects.get <!--NeedCopy-->The following Google defined roles have the permissions as listed above:
- Compute Network User
- Storage Account User
- Cloud Datastore User
-
Additional permissions required for Cloud Key Management Service (KMS) for Citrix Cloud Service Account in Provisioning project:
cloudkms.cryptoKeys.get cloudkms.cryptoKeys.list cloudkms.keyRings.get cloudkms.keyRings.list <!--NeedCopy-->The following Google defined roles have the permissions as listed above:
- Compute KMS Viewer
General permissions
Following are the permissions for Citrix Cloud Service Account in Provisioning project for all features supported in MCS. These permissions provide the best compatibility going forward:
resourcemanager.projects.get
cloudbuild.builds.create
cloudbuild.builds.get
cloudbuild.builds.list
compute.acceleratorTypes.list
compute.diskTypes.get
compute.diskTypes.list
compute.disks.create
compute.disks.createSnapshot
compute.disks.delete
compute.disks.get
compute.disks.setLabels
compute.disks.use
compute.disks.useReadOnly
compute.firewalls.create
compute.firewalls.delete
compute.firewalls.list
compute.globalOperations.get
compute.images.create
compute.images.delete
compute.images.get
compute.images.list
compute.images.setLabels
compute.images.useReadOnly
compute.instanceTemplates.create
compute.instanceTemplates.delete
compute.instanceTemplates.get
compute.instanceTemplates.list
compute.instanceTemplates.useReadOnly
compute.instances.attachDisk
compute.instances.create
compute.instances.delete
compute.instances.detachDisk
compute.instances.get
compute.instances.getSerialPortOutput
compute.instances.list
compute.instances.reset
compute.instances.resume
compute.instances.setDeletionProtection
compute.instances.setLabels
compute.instances.setMetadata
compute.instances.setTags
compute.instances.start
compute.instances.stop
compute.instances.suspend
compute.instances.update
compute.instances.updateAccessConfig
compute.instances.updateDisplayDevice
compute.instances.updateSecurity
compute.instances.updateShieldedInstanceConfig
compute.instances.updateShieldedVmConfig
compute.machineTypes.get
compute.machineTypes.list
compute.networks.list
compute.networks.updatePolicy
compute.nodeGroups.list
compute.nodeTemplates.get
compute.projects.get
compute.regions.list
compute.snapshots.create
compute.snapshots.delete
compute.snapshots.list
compute.snapshots.get
compute.snapshots.setLabels
compute.snapshots.useReadOnly
compute.subnetworks.get
compute.subnetworks.list
compute.subnetworks.use
compute.subnetworks.useExternalIp
compute.zoneOperations.get
compute.zoneOperations.list
compute.zones.get
compute.zones.list
resourcemanager.projects.get
storage.buckets.create
storage.buckets.delete
storage.buckets.get
storage.buckets.list
storage.buckets.update
storage.objects.create
storage.objects.delete
storage.objects.get
storage.objects.list
cloudkms.cryptoKeys.get
cloudkms.cryptoKeys.list
cloudkms.keyRings.get
cloudkms.keyRings.list
compute.disks.list
compute.instances.setServiceAccount
compute.networks.get
compute.networks.use
compute.networks.useExternalIp
iam.serviceAccounts.actAs
compute.resourcePolicies.use
cloudkms.cryptoKeyVersions.useToDecrypt
cloudkms.cryptoKeyVersions.useToEncrypt
<!--NeedCopy-->
Where to go next
- If you’re in the initial deployment process, see Create machine catalogs.
- For Google Cloud Platform (GCP) specific information, see Create a Google Cloud Platform catalog.