Getting started
This document describes how to get started with Citrix Analytics for Security™ for the first time.
Step 1: Sign in to Citrix Cloud™
To use Citrix Analytics for Security, you must have a Citrix Cloud account. Go to https://citrix.cloud.com and sign in with your existing Citrix Cloud account.
If you do not have a Citrix Cloud account, you must first create a Citrix Cloud account or join an existing account created by someone else in your organization. For detailed processes and instructions on how to proceed, see Sign Up for Citrix Cloud.
Step 2: Get access to Security Analytics
You can access Citrix Analytics for Security in one of the following ways:
-
Request a Citrix Analytics for Security trial. After signing in to Citrix Cloud, do the following:
-
In the Available Services section, click Manage on the Analytics tile. You are redirected to the Analytics overview page.
-
On the Security tile, click Request Trial or directly get in touch with your Citrix Account or Citrix Partner.
-
-
Subscribe to Citrix Analytics for Security. To purchase a Citrix Analytics for Security subscription, visit https://www.citrix.com/en-in/products/citrix-analytics/form/inquiry/ and contact a Citrix Analytics expert who can help you.
Note
With effect from March 8, 2023, Citrix Analytics for Security will no longer be available for purchase as a standalone offering with ShareFile/Citrix Content Collaboration. We are announcing End of Sales (EOS) and End of Renewals (EOR) of Citrix Analytics Service stand-alone add-on for ShareFile/Citrix Content Collaboration. Customers’ existing entitlements for Citrix Analytics for Security remains valid until their subscription expires. However, trials, renewals, and new purchases will not be supported for Sharefile/Citrix Content Collaboration integrations. Citrix Analytics Service integrations for other Citrix products continue to be offered as standalone or bundle offerings with existing Citrix DaaS plans, Citrix Virtual Apps and Desktops deployments and Citrix Workspace deployments.
With effect from February 03, 2020, Citrix Analytics for Security is no longer included with the Workspace Premium and the Workspace Premium Plus subscriptions. Customers who have purchased the Workspace Premium or the Workspace Premium Plus subscription before February 03, 2020 can access Citrix Analytics for Security as a part of the Workspace subscription until their subscription expires. Citrix Analytics for Security is now offered as an add-on service with the Citrix Workspace packages- Workspace Standard, Workspace Premium, and Workspace Premium Plus. For more information, see Citrix Cloud services.
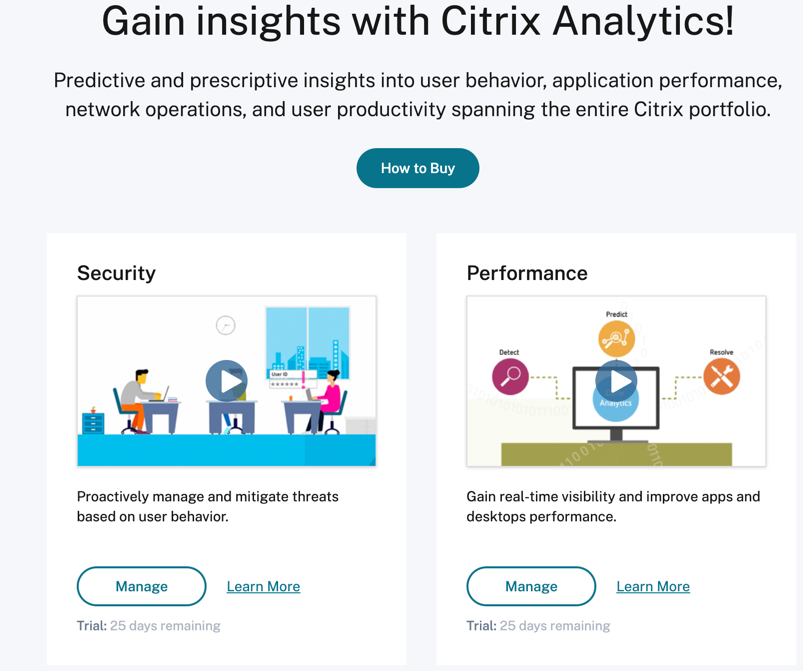
Step 3: Manage Security Analytics
After you have the necessary subscription or are authorized to access the trial, on the Analytics overview page, the Request Trial button for the Security offering changes to Manage. Click Manage to view the user dashboard.
Analytics supports both Citrix data sources and external data sources. It automatically discovers the Citrix data sources associated with your Citrix Cloud account. To receive data from external data sources, you need to integrate the external data sources with Analytics. To view your discovered data sources, click Settings > Data Sources > Security.
What’s next
-
Data processing is turned on for the following cloud services when their Citrix Analytics for Security entitlement is approved:
-
Citrix data sources
-
-
To verify the data processing status or know how to turn it on manually, see the following articles:
-
Citrix data sources:
-
External data sources:
-
-
Export processed data from Analytics to the following products:
-
Use the Users dashboard to view the discovered users and their security risk profiles. The Users dashboard is the launching point for user behavior analysis and threat prevention.
Note
If you are using Analytics for the first time, the user risk profiles take some time to appear on the dashboard. Analytics uses machine learning to determine the risky pattern or anomalies in the user events and identifies the user profiles as high risk, medium risk, and low risk based on the severity of the risks.
-
Use the self-service search feature to view and filter the user events (raw data) received from the data sources.