Preconfigured custom risk indicators and policies
Citrix Analytics for Security provides a list of preconfigured custom risk indicators and a policy to help you monitor the security of your Citrix infrastructure. The conditions of these preconfigured custom risk indicators and the policy are already defined according to specific security risk scenarios such as compromised users, insider threats, and data exfiltration. You can also modify these preconfigured conditions or add your own conditions according to your security requirements and use the custom risk indicators to mitigate the risks.
Currently, the preconfigured custom risk indicators are available for the following scenarios:
-
Geofencing
-
First time access
Preconfigured custom risk indicators for the geofencing scenario
Use the following pre-configured custom risk indicators to detect user events from outside the geofenced areas.
-
CVAD-Session started outside of geofence
-
GW-Geofence crossing
The preconfigured custom risk indicators are triggered whenever users access the Citrix® products from outside their usual country of operation or the geofence. By default, the geofence is set to “United States”. You can set your required country as a geofence.
Note
The CVAD-Session started outside of geofence risk indicator is linked to the Geofence Settings of the Access Assurance Location feature. So, you cannot directly modify the geofenced countries in the condition of the risk indicator. To update the geofenced countries in the risk indicator, select the countries in the Geofence Settings of the Access Assurance Location dashboard. For more information, see the Access assurance location dashboard.
To view the preconfigured custom risk indicators, select Security > Custom Risk Indicators.
By default, the preconfigured custom risk indicators are disabled. Use the STATUS button to enable them.
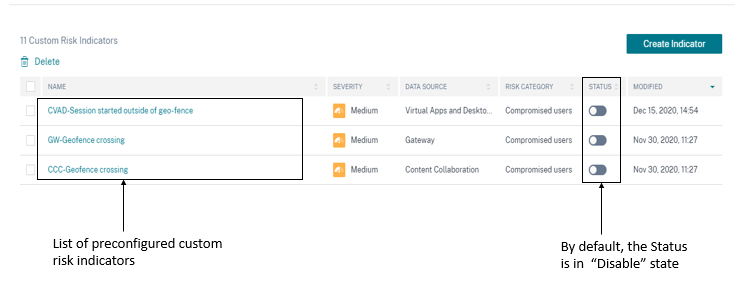
The following table describes the various preconfigured custom risk indicators for geofencing.
| Custom risk indicator name | Scenario | Custom indicator conditions | Data source | Risk category |
|---|---|---|---|---|
| CVAD-Session started outside of geofence | User has started a virtual session outside their country of operation | Event-Type = Session.logon Country != “United States” | Citrix Workspace app | Compromised users |
| GW-Geofence crossing | User has successful authentication from outside their country of operation | Event-Type = “VPN_AI” AND Country != “United States” | Citrix Gateway (on-premises) | Compromised users |
Preconfigured policy for the geofencing scenario
Citrix provides a preconfigured policy that applies the Request End User Response action to a user account whenever the user starts a virtual session from outside their country of operation. The user receives an email and based on the user’s response, an appropriate action is taken such as adding the user to the watchlist or notifying the administrator for further action. For more information, see Request end user response.
To view the preconfigured policy, select Security > Policies.
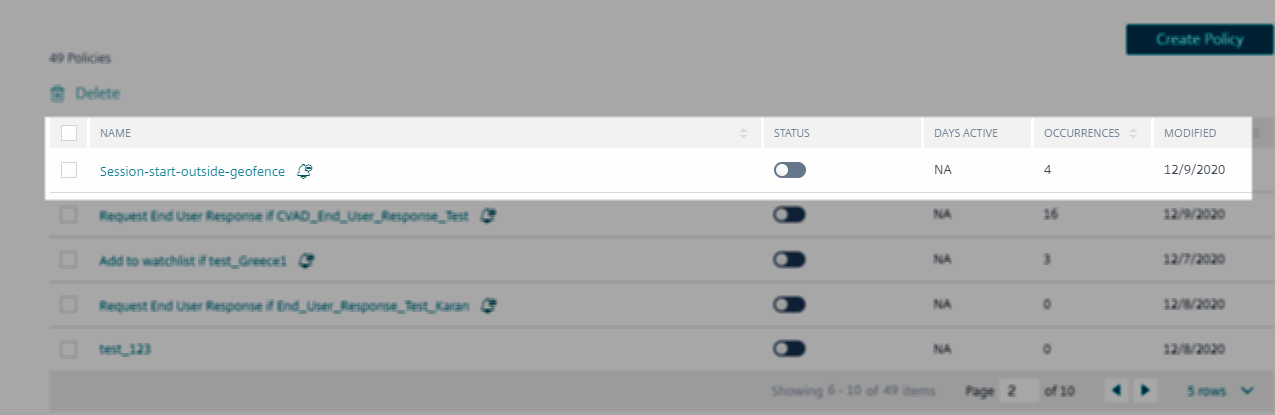
The following table describes the preconfigured policy for geofencing.
| Policy name | Scenario | Policy condition | Applied action |
|---|---|---|---|
| Session start outside of geofence | Ability for an administrator to validate the user’s legitimacy through the ‘Request End-user Response’ action when the user starts the virtual session outside their country of operation | Use with preconfigured custom risk indicator- “CVAD-Session started outside of geofence” | Request End-User Response |
| Based on the following user’s response, the corresponding action is applied | |||
| If the user does not recognize the activity: Add to watchlist | |||
| If the user recognizes the activity: No action required | |||
| If the user does not respond within 60 minutes of receiving the email: Add the user to the watchlist |
Note
The Request End User Response action is supported only in the United States region. So, if your organization is onboarded to the European Union region in Citrix Cloud™, the preconfigured policy does not get applied to your account. To use the preconfigured policy, modify the policy and select another action of your choice.
Create your own policy with preconfigured custom risk indicators for geofencing
You can also create your own policies with these preconfigured custom risk indicators and apply actions such as locking users or logging off users whenever the indicators are triggered. For information on how to create policies, see Configure policies and actions.
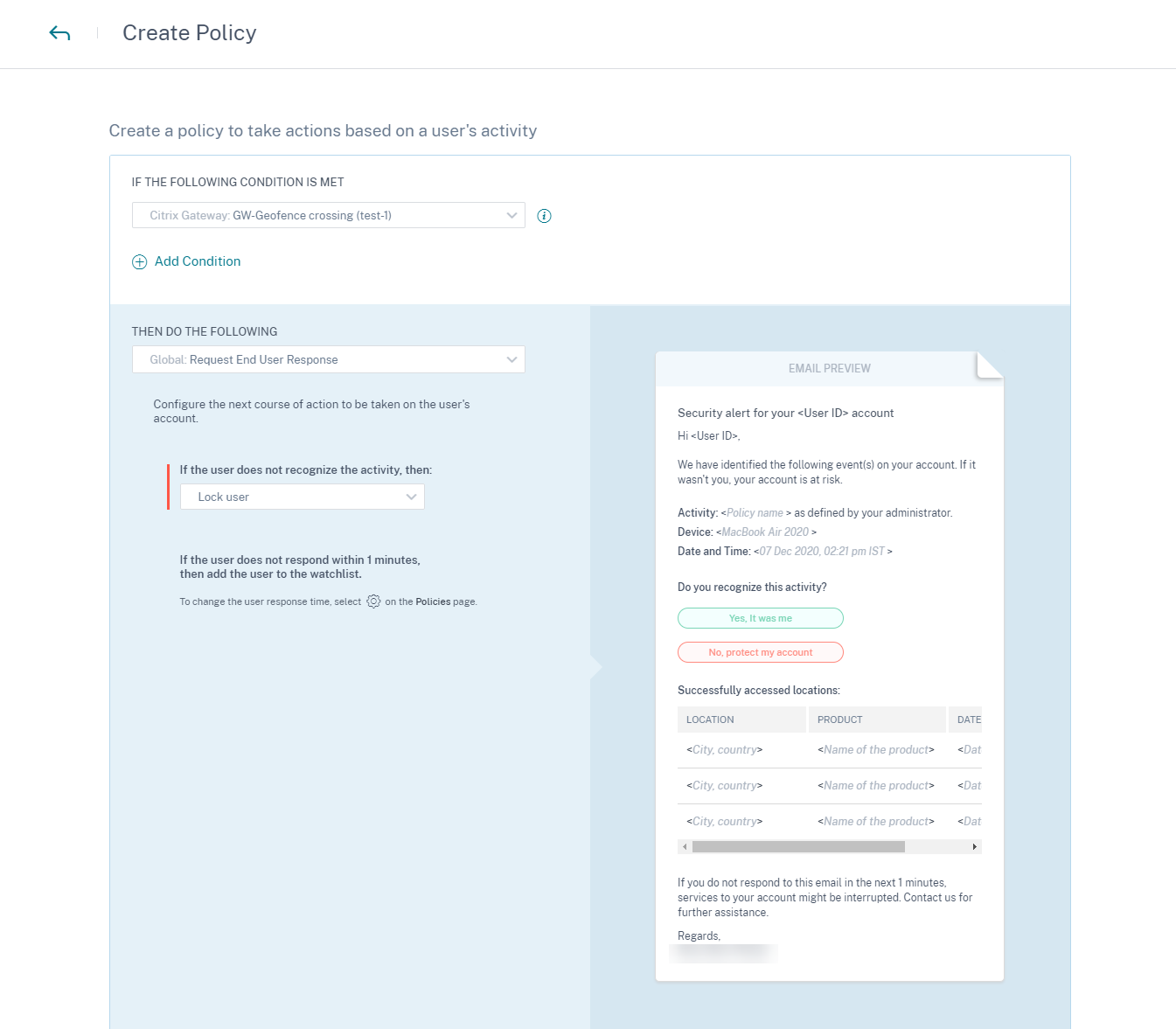
The following example shows a policy that locks users who try to access Citrix services from outside the United States. The user access is locked if the user does not recognize their access activity.
Condition: GW-Geofence crossing
Action: Request end user response
Next action: Lock the user if the user does not recognize the activity
Note
The Request End User Response action is supported only in the United States region. So, if your organization is onboarded to the European Union region, select another action of your choice instead of the Request End User Response action.
Preconfigured custom risk indicators for the first time access scenario
Use the following custom risk indicators to detect the user events for the first-time access scenarios:
-
CVAD-First time access from new device
-
Gateway-First time access from new IP
By default, these preconfigured custom risk indicators are in the enabled state. Use the STATUS button if you want to disable them.
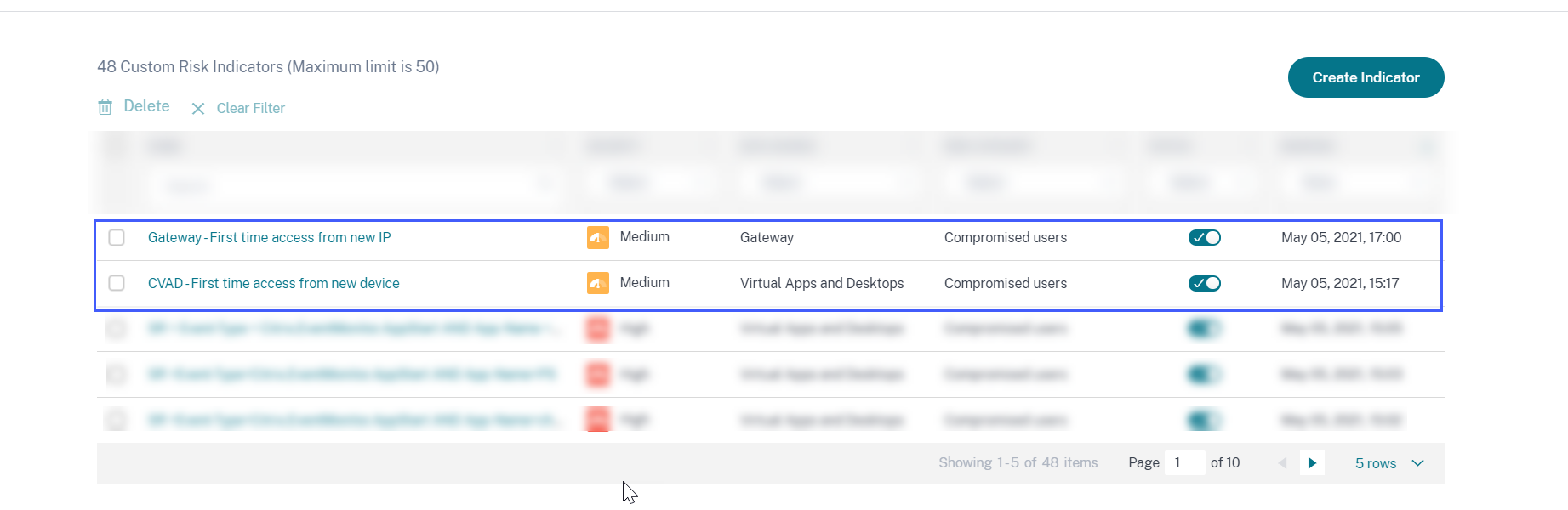
The following table describes the preconfigured custom risk indicators for first-time access.
| Custom indicator name | Scenario | Preconfigured conditions | Data source | Risk category |
|---|---|---|---|---|
| CVAD-First time access from new device | When a Citrix Workspace app user signs in from one of the following | The following conditions are enabled by default | Citrix Virtual Apps and Desktops on-premises and Citrix DaaS (formerly Citrix Virtual Apps and Desktops service) | Compromised users |
| A new device | The First time for a new Device-ID. | |||
| An existing device that has not been used for the last 90 days. | Event-Type = "Session.Logon" AND Client-Type IN ("XA.Receiver.Windows", "XA.Receiver.Mac", "XA.Receiver.Chrome", "XA.Receiver.Android", "XA.Receiver.Linux", "XA.Receiver.iOS") |
|||
| Gateway-First time access from new IP | When a Citrix Gateway user successfully signs from one of the following | The following conditions are enabled by default | Citrix Gateway | Compromised users |
| A new public IP address | The First time for a new Client-IP | |||
| An existing public IP address that has not been used for the last 90 days. | Event-Type = "Authentication" AND Status-Code = "Successful login" AND Client-IP-Type != "private" AND Access-Insight-Flags = 1 |
On the condition bar, you can also add your own conditions in addition to the preconfigured conditions to identify threats as per your requirements.
For example, if you want to identify the user events from a particular country, you can add the country dimension along with the preconfigured condition:
-
Event-Type = "Session.Logon" AND Client-Type IN ("XA.Receiver.Windows", "XA.Receiver.Mac", "XA.Receiver.Chrome", "XA.Receiver.Android", "XA.Receiver.Linux", "XA.Receiver.iOS") AND Country = “United States” -
Event-Type = "Authentication" AND Status-Code = "Successful login" AND Client-IP-Type != "private" AND Access-Insight-Flags = 1 AND Country = “United States”