Service continuity
Service continuity allows users to connect to their DaaS apps and desktops when they are unable to connect to Citrix Workspace™ or DaaS, for example, due to an outage or a network connectivity problem.
Service continuity works by securely caching connection leases (long-lived authorization tokens) on the local device. The first time a user signs in to Citrix Workspace, it saves connection lease files to the user profile for each resource published to the user. Workspace connection lease files are signed and encrypted and are associated with the user and the user’s device. By default, the connection lease allows users to access apps and desktops for seven days but you can change this to up to 30 days.
When users exit Citrix Workspace app, Citrix Workspace app closes but the Workspace connection leases are retained. You can configure service continuity to delete or retain Workspace connection leases when users explicitly logs out of Citrix Workspace by clicking the log out button. By default, Workspace connection leases are deleted from user devices when users log out by clicking the log out button.
Service continuity is supported for double hop scenarios when Citrix Workspace app is installed on a virtual desktop.
For an in-depth technical article about Citrix Cloud resiliency features, including service continuity, see Citrix Cloud Resiliency.
Note:
The deprecated Citrix DaaS™ feature called “connection leasing” resembles Workspace connection leases in that it improved connection resiliency during outages. Otherwise, that deprecated feature is unrelated to service continuity.
User device setup
To access resources using Service Continuity during an outage, a user must have previously signed in to Citrix Workspace using Citrix Workspace app or their web browser with Citrix web extension.
To use Citrix Workspace app, users must perform the following steps on their devices:
- Download and install a supported version of Citrix Workspace app.
- Add the Workspace URL for your organization to Citrix Workspace app (for example,
https://example.cloud.com). - Log in to Citrix Workspace.
When using a web browser:
- Download and install a supported version of Citrix Workspace app.
- Add Citrix web extensions to their browser.
- Open the Workspace URL in their browser.
- Log in.
This video shows how to install and use service continuity in browser.
When a user signs into Citrix Workspace for the first time, service continuity downloads Workspace connection leases to the user device. Downloading Workspace connection leases might take up to 15 minutes for first-time sign-in. Users can continue launching published resources during the download period.
User experience during an outage
When service continuity is enabled, the user experience during an outage varies depending on:
- The type of outage
- Whether the Citrix Workspace app is configured with domain pass-through authentication
- Whether session sharing is enabled for the app or desktop the user connects to
For some outages, users continue accessing their DaaS with no change to their user experience. For other outages, user might see a change in how Workspace appears or be prompted to take some action.
This table summarizes how service continuity helps users access apps and desktops during different types of outages.
| Where the outage occurs | How service continuity maintains user access | User experience during outage |
|---|---|---|
| Citrix Workspace | Citrix Workspace app enumerates apps and desktops based on local cache on the user device. | Icons for unavailable apps and desktops appear dimmed. Users can still access apps and desktops that have undimmed icons. After clicking an undimmed icon, users might be prompted to reenter their credentials at the VDA. To regain access to all their apps and desktops, users can try to establish their connection to Workspace by clicking the “Reconnect to Workspace” link. |
| Identity provider | Citrix Workspace app and enumerates apps and desktops based on local cache on the user device. | Users might be unable to log in to Workspace. Users click the “Use Workspace offline” link to access some apps and desktops in an experience identical to a Workspace service outage. |
| Citrix Cloud™ Broker Service | For VDAs registered with connectors, the High Availability Service in the Cloud Connector takes over brokering. All VDAs that were registered with the Cloud Broker Service register with the High Availability Service. For connectorless VDAs, the brokering of the session is done through the Virtual Delivery Agent (VDA). | Some users might be unable to access virtual resources while VDAs register with the High Availability Service. Existing sessions aren’t affected. No user action needed. |
| Secure Ticket Authority | Workspace connection leases provide access to virtual resources when ICA® files can’t. | Sessions launches might take a few seconds longer. No user action needed. |
| Citrix Gateway service | Network traffic fails over to the closest healthy Citrix Gateway service point of presence (POP). | Existing sessions might take a few seconds to reconnect. No user action needed. |
| Internet connection on the LAN | Citrix Workspace app enumerates apps and desktops based on local cache on the user device. If a user has a direct network connection to the resource location, Citrix Workspace app bypasses the Citrix Gateway service when the user clicks undimmed icons. Citrix Workspace app contacts the Cloud Connector over TCP 2598 and contacts VDAs over TCP 2598 or UDP 2598. | Icons for unavailable apps and desktops appear dimmed. Users can still access apps and desktops that have undimmed icons. After clicking an undimmed icon, users might be prompted to reenter their credentials at the VDA. To regain access to all their apps and desktops, users can try to establish their connection to Workspace by clicking the “Reconnect to Workspace” link. |
Citrix Workspace outage
During a Citrix Workspace outage, users see this message at the top of the Citrix Workspace home page: “Unable to connect to some of your resources. Some virtual apps and desktop may still be available.” Users see apps and desktops that they can connect to during the outage. If the app or desktop isn’t available, the icon appears dimmed.
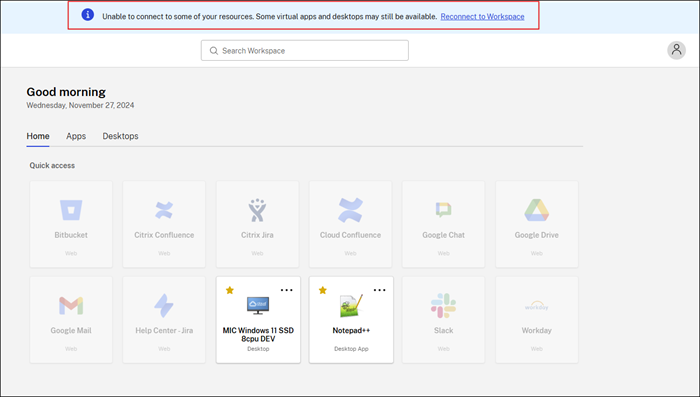
To access available resources during an outage, users select a resource icon that isn’t dimmed.
Launching resources
Depending on how Citrix Workspace app and VDAs are configured, during an outage the VDA might prompt users to enter their credentials into the Windows Logon user interface. If this prompt occurs, users enter their Active Directory (AD) credentials or smart card PIN to access the app or desktop.
Users can access resources without entering their AD credentials if Citrix Workspace app for Windows is configured with domain pass-through authentication. For more information, see Configure single sign-on using the graphical user interface.
If session sharing is enabled, users can access apps or desktops hosted on the same VDA after they provide their credentials for one resource on that VDA. Session sharing is configured for the application group containing the resource on the VDA. For information about configuring application groups, see Create application groups.
In all other configurations, users are prompted to reenter their AD credentials at the VDA before accessing resources.
Identity provider outages
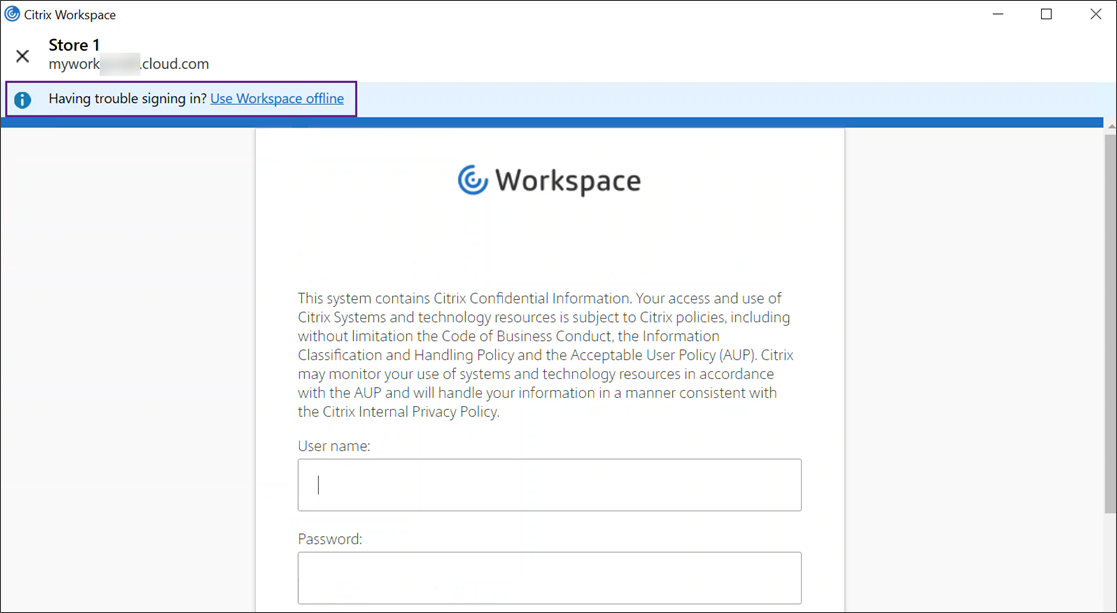
During an outage in the identity provider for workspace authentication, users might be unable to log in to Citrix Workspace through the Workspace log in page.
When using Citrix Workspace app, after 40 seconds, this message appears at the top of the window.
If using a web browser, after 60 seconds the following pop-up appears.
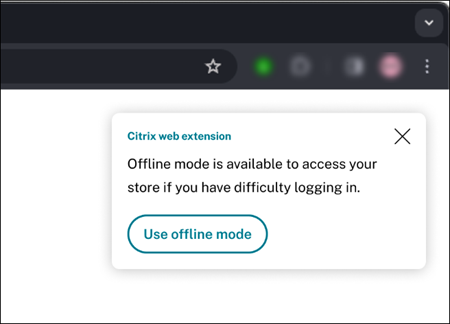
Afterward, the Citrix Workspace home page appears. Users then access resources as they would during a Citrix Workspace outage.
Exit and log out behavior
Regardless of the type of outage, users can continue to access resources if they exit and relaunch Citrix Workspace app or browser including after restarting their devices.
In the default configuration of service continuity, users lose access to their resources if they explicitly log out of Citrix Workspace. If you want users to retain access to their resources after signing out, specify that Workspace connection leases are kept when users log out. See Configure service continuity.
Browser user experience during outages
To access available apps and desktops offline, users can click Use offline mode.
To manage the offline mode prompt, click the Citrix web extension in the browser on the user device. The following screen appears:
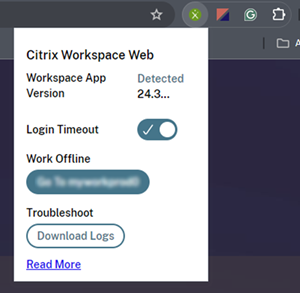
Users can use the Work Offline option to manually switch to offline mode without waiting 60 seconds for the offline mode prompt.
During some outages, the warning window prompting users to work offline appears automatically when the extension detects Workspace-side issues. The user doesn’t need to take any action or wait through the login timeout interval.
Requirements and limitations
Site requirements
-
Supported in all editions of Citrix DaaS with Citrix Workspace.
-
Not supported for Citrix Workspace with site aggregation to on-premises Virtual Apps and Desktops.
-
Not supported when on-premises Citrix Gateway is used as an ICA Proxy. (Using Citrix Gateway Service as a Workspace authentication method is supported.)
User device requirements
Minimum supported Citrix Workspace app versions:
- Citrix Workspace app for Windows 2106
- Citrix Workspace app for Linux 2106
- Citrix Workspace app for Mac 2106
- Citrix Workspace app for Android 22.2.0
- Citrix Workspace app for iOS 22.4.5
- Citrix Workspace app for ChromeOS 2301
For users who access their apps and desktops using browsers:
- Citrix Workspace app 2109 for Windows at a minimum. Supported with Google Chrome and Microsoft Edge.
- Citrix Workspace app for Mac version 2112 at a minimum for use with Google Chrome.
- Citrix Workspace app for Windows (Store) is not supported.
If using connectorless VDAs:
- Citrix Workspace app for Windows 2309 or later
Only one user per device is supported. Kiosk or “hot desk” user devices aren’t supported.
Web browser requirements and limitations
When accessing a store through a web browser, users must use a browser supported by Citrix web extensions.
If users clear cookies and other site data in their browsers during an outage, service continuity doesn’t work until they authenticate to Workspace again.
Service continuity isn’t supported in incognito or InPrivate mode.
Supported workspace authentication methods
- Active Directory
- Active Directory plus token
- Microsoft Entra ID
- Okta
- Citrix Gateway (primary user claim must be from AD)
- SAML 2.0
- Conditional Authentication
Authentication limitations
- Single sign-on with Citrix Federated Authentication Service (FAS) isn’t supported. Users enter their AD credentials into the Windows Logon user interface on the VDA.
- Single sign-on to VDA using cached Active Directory credentials isn’t supported.
- Local mapped accounts aren’t supported.
- VDAs can be Microsoft Entra ID joined or AD joined. Hybrid joined machines aren’t supported
- If using Adaptive Authentication, the Adaptive Authentication or service must remain reachable for service continuity to function.
- If using the Device Posture service, the Device Posture service must remain reachable for service continuity to function. To maintain security, service continuity verifies the results of the latest scan of the device’s posture before launching a session. If the results of the scan are unavailable or outdated, service continuity prevents session launch, ensuring compliance with security policies.
- For connectorless VDAs, signing in with Windows Hello in the virtual desktop is not supported. Only user name and password are currently supported. If users try to log in with any Windows Hello method, they receive an error stating that they are not the brokered user, and the session is disconnected. Associated methods include PIN, FIDO2 key, MFA, and so on.
Citrix Cloud Connector™ scale and size
- 4 vCPU or more
- 6 GB memory or more
Citrix Cloud Connector connectivity
Citrix Cloud Connector must be able to reach https://rootoftrust-ap-s.apps.cloud.com, https://rootoftrust-eu.apps.cloud.com, and https://rootoftrust.apps.cloud.com. For more information, see System and Connectivity Requirements in Citrix Cloud documentation. Configure your firewall to allow this connection. For information about the Cloud Connector firewall, see Cloud Connector Proxy and Firewall Configuration.
Connectivity optimization limitations
Advanced Endpoint Analysis (EPA) isn’t supported.
Enlightened Data Transport (EDT) isn’t supported during outages.
VDA requirements and limitations
- VDAs registered with connectors: 7.15 LTSR or higher. For connectorless VDAs: 2402 or higher.
- VDAs must be online for users to access VDA resources during an outage. Service continuity does no protect against outages of platforms hosting the VDAs such as Azure or AWS.
- For VDAs registered with connectors, workloads supported during outages:
- Hosted shared apps and desktops
- Random non-persistent desktops (pooled VDI desktop) with power management
- Static non-persistent desktops
- Static persistent desktops, including Remote PC Access
Note:
Assign on first use isn’t support during outages. Random non-persistent desktops with power management are unavailable by default if Cloud Connectors lose connectivity with Citrix Cloud unless
ReuseMachinesWithoutShutdownInOutageis configured for the delivery group. Review Application and desktop support for more details. - For connectorless VDAs using Rendezvous V2, workloads supported during outages:
- Static persistent desktops
For more information about available VDA functions during outages, see VDA management during outages.
Local keyboard mapping requirements and limitations
The Windows Logon user interface that prompts users to reauthenticate on the VDA does not support local keyboard language mapping. To allow users to reauthenticate during an outage if they have local keyboard language mapping on their devices, preload the keyboard layouts these users require.
Warning:
Editing the registry incorrectly can cause serious problems that might require you to reinstall your operating system. Citrix can’t guarantee that problems resulting from the incorrect use of the Registry Editor can be solved. Use the Registry Editor at your own risk. Be sure to back up the registry before you edit it.
Edit this registry key in the VDA image:
HKEY_USERS\.DEFAULT\Keyboard Layout\Preload
The corresponding language pack in the virtual desktop image must be installed.
For a list of keyboard identifiers associated with keyboard languages, see Keyboard Identifiers and Input Method Editors for Windows.
Configure resource location network connectivity for service continuity
You can configure your resource location to accept connections from inside your LAN, outside your LAN, or both.
Configure for connections inside your LAN
- From the Citrix Cloud menu, go to Workspace Configuration > Access.
- Select Configure Connectivity.
- Select Internal Only as your connectivity type.
- Click Save.
Configure your Citrix Cloud Connector and VDA firewalls to accept connections over Common Gateway Protocol (CGP) TCP port 2598. This configuration is the default setting.
Configure for connections from outside your LAN
- From the Citrix Cloud menu, go to Workspace Configuration > Access.
- Select Configure Connectivity.
- Select Gateway Service as your connectivity type.
- Click Save.
Configure service continuity
To enable service continuity for your site:
- From the Citrix Cloud menu, go to Workspace Configuration > Service Continuity.
-
Set Connection leasing for the Workspace to Enable.
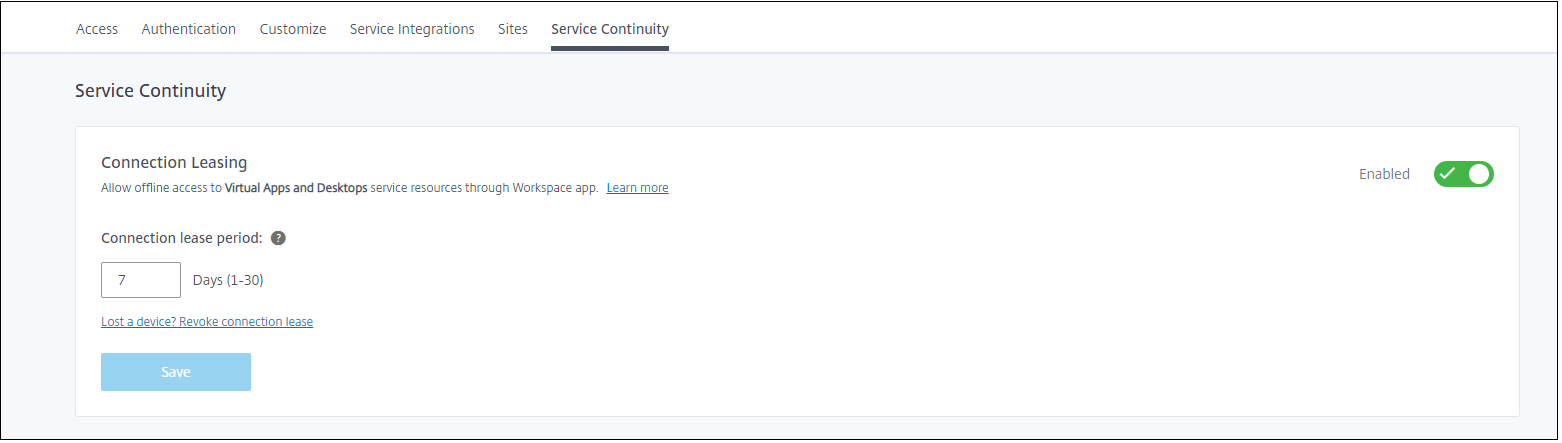
- Set Connection lease period to the number of days a Workspace connection lease can be used to maintain a connection. The Workspace connection lease period applies to all Workspace connection leases through your site. The Workspace connection lease period starts the first time a user signs in to the Citrix Cloud Workspace store. Workspace connection leases are refreshed each time the user signs in, up to once a day. The Workspace connection lease period can be from one day to 30 days. The default is seven days.
- Click Save.
When you enable service continuity, it is enabled for all delivery groups in your site. To disable service continuity for a delivery group, use the following PowerShell command:
Set-BrokerDesktopGroup -name <deliverygroup> -ResourceLeasingEnabled $false
Replace deliverygroup with the name of the delivery group.
By default, Workspace connection leases are deleted from the user device if the user logs out of Citrix Workspace during an outage. If you want Workspace connection leases to remain on user devices after users log out, use the following PowerShell command:
Set-BrokerSite -DeleteResourceLeasesOnLogOff $false
Notes:
- Workspace connection leases can’t be set to remain on user devices after users log out for users connecting with Citrix Workspace app for Mac. Citrix Workspace for Mac is unable to read the value of the
DeleteResourceLeaseOnLogOffproperty.- It might take up to 12 hours for Workspace app clients to update after the setting is configured.
Configure Service Continuity for connectorless workloads
Service Continuity for connectorless workloads must be configured per resource location.
-
Install VDA 2402 for Microsoft Entra ID joined VDAs.
- Enable the CLXMTP service on the VDAs by configuring the following registry key, then reboot the VDA:
[HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\ClxMtpService] "ClxMtpSvcEnabled"=dword:00000001 "ClxMtpTimeoutInMilliSeconds"=dword:00035000 "ClxMtpFsmLogLevel"=dword:00000003 <!--NeedCopy-->Note:
For MCS provisioned VDAs, consider setting these registry keys on the master image
- Create a Microsoft Entra ID joined catalog.
-
Create a Delivery Group.
Note
Only dedicated desktops are supported. Assign the desktop to a user.
- Enable Service Continuity.
- Enable Service Continuity for connectorless workloads on the connectorless resource location by running the following PowerShell.
powershell
Set-ConfigZone -Name <zoneName> -EnableVdaConnectivityForResourceLeases $true
<!--NeedCopy-->
How service continuity works
If there’s no outage, users access virtual apps and desktops using ICA files. Citrix Workspace generates a unique ICA file each time a user selects a virtual app or desktop icon. Each ICA file contains a Secure Ticket Authority (STA) ticket and a logon ticket that can be redeemed only once to gain authorized access to virtual resources. The tickets in each ICA file expire after about 90 seconds. After the ticket in an ICA file is used or expires, the user needs another ICA file from Citrix Workspace to access resources. When service continuity isn’t enabled, outages can prevent users from accessing resources if Citrix Workspace can’t generate an ICA file.
Citrix Workspace generates ICA files when users launch virtual apps and desktops regardless of whether service continuity is enabled. When service continuity is enabled, Citrix Workspace also generates the unique set of files that make up a Workspace connection lease. Unlike ICA files, Workspace connection lease files are generated when the user signs into Citrix Workspace, not when the user launches the resource. When a user signs in to Citrix Workspace, connection lease files are generated for every resource published to that user. Workspace connection leases contain information that gives the user access to virtual resources. If an outage prevents a user from signing in to Citrix Workspace or accessing resources using an ICA file, the connection lease provides authorized access to the resource.
How sessions launch during outages
When users click an icon for an app or desktop during an outage, the Citrix Workspace app finds the corresponding Workspace connection lease on the user device. Citrix Workspace app then opens a connection. If connectivity to the resource location that hosts the app or desktop is configured to accept connections from outside your LAN, a connection opens to Citrix Gateway Service. If you configure connectivity to the resource location that hosts the app or desktop to accept connections from inside your LAN only, a connection opens to the Cloud Connector.
When opening the workspace in a web browser, the browser uses Citrix web extension to communicate with Citrix Workspace app using the native messaging host protocol for browser extensions.
When the Citrix Cloud broker is online, the Cloud Connector uses the Citrix Cloud broker to resolve which VDA is available. When the Citrix Cloud broker is offline, the secondary broker for the Cloud Connector (also known as the High Availability service) listens for and processes connection requests.
Users who are connected when an outage occurs can continue working uninterrupted. Reconnections and new connections experience minimal connection delays. This functionality is similar to Local Host Cache, but does not require an on-premises StoreFront.
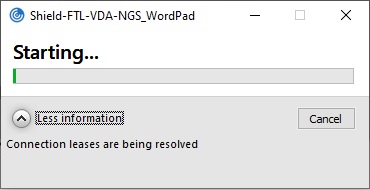
When a user launches a session during an outage, this window appears indicating that Workspace connection leases were used for the session launch:
After the user has finished signing into the session, these properties appear in the Workspace Connection Center:
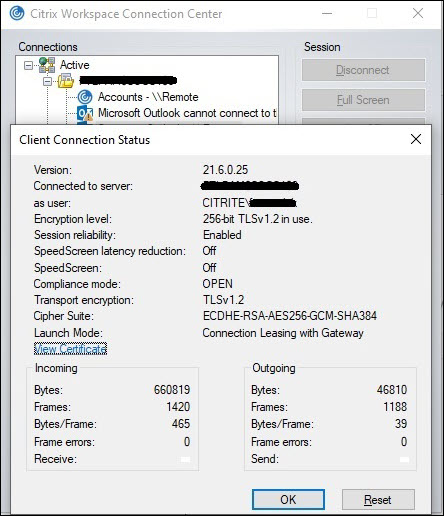
The launch mode property provides information about the Workspace connection leases used to launch the session.
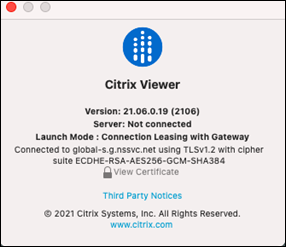
On devices running Citrix Workspace app for Mac, Citrix Viewer displays information showing that Workspace connection leases were used for the session launch:
What makes it secure
All sensitive information in the Workspace connection lease files is encrypted with the AES-256 cipher. Workspace connection leases are bound to a public/private key pair uniquely associated with the specific client device and can’t be used on a different device. A built-in cryptographic mechanism enforces use of the unique key pair on each device.
Workspace connection leases are stored on the user device in AppData\Local\Citrix\SelfService\ConnectionLeases.
The security architecture of service continuity is built on public-key cryptography, similarly to a public key infrastructure (PKI), but without certificate chains and certificate authorities. Instead, all the components establish transitive trust by relying on a new Citrix Cloud service called the root of trust that acts like a certificate authority.
Block connection leases
If a user device is lost or stolen, or a user account is closed or compromised, you can block Workspace connection leases. When you block Workspace connection leases associated with a user, the user can’t connect to resources. Citrix Cloud no longer generates or synchronizes Workspace connection leases for the user.
When you block Workspace connection leases associated with a user account, you block connections to that account on all devices associated with it. You can block Workspace connection leases for a user or for all users in a user group.
To revoke Workspace connection leases for a single user or user group, use this PowerShell command:
Set-BrokerConnectionLeaseRevocationDate -Name username -LeaseRevocationDays Days
Replace username with the user associated with the account you want to block from connecting. Replace username with a user group to block connection from all accounts in the user group. Replace Days with the number of days connections are blocked.
For example, to block connections for xd.local/user1 for the next 7 days, type:
Set-BrokerConnectionLeaseRevocationDate -Name xd.local/user1 -LeaseRevocationDays 7
To view the time period for which Workspace connection leases are revoked, use this PowerShell command:
Get-BrokerConnectionLeaseRevocationDate -Name username
Replace username with the user or user group you want to view the time period for.
For example, to view the time period for which Workspace connection leases are revoked for xd.local/user1, type:
Get-BrokerConnectionLeaseRevocationDate -Name xd.local/user2
This information appears:
FullName :
Name : XD\user2
UPN :
Sid : S-1-5-21-nnnnnn
LeaseRevocationDays : 2
LeaseRevocationDateTimeInUtc : 2020-12-17T17:34:25Z
LastUpdateDateTimeInUtc : 2020-12-19T17:34:25Z
From this output, you can see that user xd.local/user2 has Workspace connection leases revoked for two days, from December 17, 2020, through December 19, 2020, at 17:34:25 UTC on each day.
To allow a user account that has Workspace connection leases revoked to receive connection again, remove the block using this PowerShell command:
Remove-BrokerConnectionLeaseRevocationDate -Name username
Replace username with the blocked user or user group you want to receive connection. To allow all blocked user account to receive connections, leave out the Name option.
Double hop scenarios
Service continuity can allow users to access virtual resources during outages in double hop scenarios if they’re signed in to Citrix Workspace before the outage occurs. In a double hop scenario, a physical user device connects to a virtual desktop that has Citrix Workspace app installed. The virtual desktop then connects to another virtual resource.
In the double hop scenario, service continuity can allow users to access virtual resources during an outage regardless of the type of virtual desktop. If the virtual desktop retains user changes, service continuity can also provide access to virtual resources during outages that occur while the user isn’t signed in.
Service continuity treats the physical user device and the virtual device in a double hop scenario as individual client endpoints. Each device has its own set of Workspace connection leases. When a user signs in to Citrix Workspace on a physical device, Workspace connection lease files are downloaded and saved to the user profile on the physical device. The user then accesses a virtual desktop and signs in to Citrix Workspace on the virtual desktop. At this point, a different set of Workspace connection leases is downloaded and saved the user profile on the virtual desktop. Workspace connection lease files are associated with the device they’re downloaded to. Workspace connection lease files can’t be copied to another device and reused, even by the same user. Thus, service continuity can’t provide access to resources during outages that occur after the session ends if the virtual desktop discards changes made during a user session. For this type of virtual desktop, Workspace connection leases are among the changes discarded.
Here’s how service continuity works in double hop scenarios with each type of supported virtual desktop.
| For double hops that include… | Service continuity can provide access to virtual resources during outages… |
|---|---|
| Hosted shared desktops | If the outage occurs while the user is signed in to the virtual desktop. |
| Random non-persistent desktops (pooled VDI desktop) | If the outage occurs while the user is signed in to the virtual desktop. |
| Static non-persistent desktops | If the virtual desktop hasn’t restarted since the user last logged in. |
| Static persistent desktops | Anytime an outage occurs. |
VDA management during outages
For VDAs registered with connectors, service continuity uses the Local Host Cache function within the Citrix Cloud Connector. Local Host Cache allows connection brokering to continue on a site when the connection between the Cloud Delivery Controller and the Cloud Connector fails. Because service continuity relies on Local Host Cache, it shares some limitations with Local Host Cache.
Note:
Although service continuity uses Local Host Cache within the Cloud Connector, unlike Local Host Cache, service continuity isn’t supported with on-premises StoreFront.
Service Continuity for connectorless workloads differs from Service Continuity in that the brokering of the session is done through the Virtual Delivery Agent (VDA) rather than Cloud Connectors. The VDA communicates with the Citrix Cloud back end services to broker the session for the user through either a direct connection or the Gateway Service, depending on the settings configured for that resource location. More information regarding how resource location network connectivity can be configured for Service Continuity can be found in Configure resource location network connectivity for service continuity.
Power management of VDAs during outages
If Cloud Connectors lose connectivity to Citrix Cloud, Connectors are unable to to receive hypervisor credentials from Citrix Cloud. This means:
- During an outage, all machines are in the unknown power state and no power operations can be issued. However, VMs on the host that are powered-on can be used for connection requests.
By default, power-managed desktop VDAs in pooled delivery groups that have the ShutdownDesktopsAfterUse property enabled are not available for new connections if Cloud Connectors lose connectivity with Citrix Cloud. You can change this setting to allow those desktops to be used if Cloud Connectors lose connectivity with Citrix Cloud by configuring the ReuseMachinesWithoutShutdownInOutage flag on your delivery groups. Changing the ReuseMachinesWithoutShutdownInOutage parameter to $true can result in data from previous user sessions to be present on the VDA until it is restarted.
Power management resumes when normal operations resume after an outage.
Machine assignment and automatic enrollment
An assigned machine can be used only if the assignment occurred during normal operations. New assignments cannot be made during an outage.
Automatic enrollment and configuration of Remote PC Access machines isn’t possible. However, machines that were enrolled and configured during normal operation are usable.
VDA resources in different zones
Server-hosted applications and desktop users might use more sessions than their configured session limits, if the resources are in different zones.
Unlike Local Host Cache, service continuity can launch apps and desktops from registered VDAs in different zones, providing the resource is published in more than one zone. Citrix Workspace app might take longer to find a healthy zone as it cycles sequentially through all the zones in the Workspace connection lease.
Monitoring and troubleshooting
Service continuity performs two main actions:
- Download Workspace connection leases to the user device. Workspace connection leases are generated and synced with the Citrix Workspace app.
- Launch virtual desktops and apps using Workspace connection leases.
Troubleshooting downloading Workspace connection leases
You can view Workspace connection leases at this location on the user device.
On Windows devices:
C:\Users\Username\AppData\Local\Citrix\SelfService\ConnectionLeases\Store GUID\User GUID\leases
Username is the user name.
Store GUID is the global unique identifier of the Workspace store.
User GUID is the global unique identifier of the user.
On Mac devices:
$HOME/Library/Application Support/Citrix Receiver/CLSyncRoot
For example, open /Users/luca/Library/Application Support/Citrix Receiver/CLSyncRoot
On Linux:
$HOME/.ICAClient/cache/ConnectionLease
For example, open /home/user1/.ICAClient/cache/ConnectionLease
Workspace connection leases are generated when the Citrix Workspace app connects to the Workspace store. View registry key values on the user device to determine whether the Citrix Workspace app has successfully contacted the Workspace connection lease service in Citrix Cloud.
Open regedit on the user device and view this key:
HKCU\Software\Citrix\Dazzle\Sites\store-xxxx
If these values appear in the registry key, the Citrix Workspace app contacted or attempted to contact the Workspace connection lease service:
leaseLastCallHomeTimeleaseLastSyncStatus
If the Citrix Workspace app tried unsuccessfully to contact the Workspace connection lease service, leaseLastCallHomeTime shows an error with an invalid time stamp:
leaseLastCallHomeTime REG_SZ 1/1/0001 12:00:00 AM
If leaseLastCallHomeTime is uninitialized, the Citrix Workspace app never attempted to contact the Workspace connection lease service. To resolve this issue, remove the account from the Citrix Workspace app and add it again.
Citrix Workspace app error codes for Workspace connection leases
When a service continuity error occurs on the user device, an error code appears in the error message. Common errors include:
| Error code | Description |
|---|---|
| 3000 | No connection lease files present |
| 3002 | Connection lease cannot be read or found |
| 3003 | No resource location found |
| 3004 | Connection details missing in the leases |
| 3005 | ICA file is empty |
| 3006 | Connection lease expired. Log back into Workspace. |
| 3007 | Connection lease is invalid |
| 3008 | Connection lease validation result: empty |
| 3009 | Connection lease validation result: invalid |
| 3010 | Parameter missing |
| 3020 | Connection lease validation failed |
| 3021 | No resource location found where the app is published |
| 3022 | Connection lease validation result: deny |
| 3023 | Citrix Workspace app timed out |
| 3024 | User canceled the lease-based launch while in progress |
| 3025 | Number of launch-retry count exceeded |
| 3026 | Negotiated resource (app or desktop) can not be launched |
Access selfservice.txt
To access the selfservice.txt file for self-service troubleshooting, perform the following steps:
- Create a blank text file and name it
enableshieldandlogging.reg. -
Copy the following text into the file and save:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Citrix\Dazzle] "Tracing"="True" "AuxTracing"="True" "DefaultTracingConfiguration"="global all -detail" "ConnectionLeasingEnabled"="True" [HKEY_CURRENT_USER\Software\Citrix\Dazzle] "RemoteDebuggingPort"="8088" <!--NeedCopy--> - Place your saved file into your client endpoint.
- The
selfservice.txtfile is now discoverable at the following path:%LocalAppData%\Citrix\SelfService.
Troubleshooting for browser users
In the Advanced menu of the Citrix Workspace browser app account settings, ensure the current method for app and desktop launch preference is set to Use Citrix Workspace App. If this option is set to Use Web Browser, service continuity isn’t supported in the browser.
Ensure that the extension icon in the browser appears green after the browser loads the Workspace URL.
To download logs, click the extension icon in the browser. Then click Download Logs.
In this article
- User device setup
- User experience during an outage
- Requirements and limitations
- Configure resource location network connectivity for service continuity
- Configure service continuity
- How service continuity works
- How sessions launch during outages
- What makes it secure
- Double hop scenarios
- VDA management during outages
- Monitoring and troubleshooting