Administrator tasks and considerations
This article discusses the tasks and considerations that are relevant for administrators of mobile productivity apps.
Feature flag management
If an issue occurs with a mobile productivity app in production, we can disable an affected feature within the app code. We can disable the feature for Secure Hub, Secure Mail, and Secure Web for iOS and Android. To do so, we use feature flags and a third-party service called LaunchDarkly. You do not need to make any configurations to enable traffic to LaunchDarkly, except when you have a firewall or proxy blocking outbound traffic. In that case, you enable traffic to LaunchDarkly via specific URLs or IP addresses, depending on your policy requirements. For details about support since for the exclusion of domains from tunneling, see the MAM SDK documentation.
You can enable traffic and communication to LaunchDarkly in the following ways:
Enable traffic to the following URLs
events.launchdarkly.comstream.launchdarkly.comclientstream.launchdarkly.comfirehose.launchdarkly.com
Create an allow list by domain
Earlier, we offered a list of IP addresses to use when your internal policies require only IP addresses to be listed. Now, because Citrix® has made infrastructure improvements, we are phasing out the public IP addresses starting on July 16, 2018. We recommend that you create an allow list by domain, if you can.
List IP addresses in an allow list
If you must list IP addresses in an allow list, for a list of all current IP address ranges, see this LaunchDarkly public IP list. You can use this list to ensure that your firewall configurations are updated automatically in keeping with the infrastructure updates. For details about the status of the infrastructure changes, see the LaunchDarkly Statuspage.
Note:
Public app store apps require a fresh installation the first time you deploy them. It is not possible to upgrade from the current enterprise wrapped version of the app to the public store version.
With public app store distribution, you do not sign and wrap Citrix-developed apps with the MDX Toolkit. You can use the MDX Toolkit to wrap third-party or enterprise apps.
LaunchDarkly system requirements
- Endpoint Management 10.7 or later.
- Ensure that the apps can communicate with the following services if you have split tunneling on Citrix ADC set to OFF:
- LaunchDarkly service
- APNs listener service
Supported app stores
Mobile productivity apps are available on the Apple App Store and Google Play.
In China, where Google Play is unavailable, Secure Hub for Android is available on the following app stores:
Enabling public app store distribution
- Download public-store .mdx files for both iOS and Android from the Endpoint Management downloads page.
- Upload the .mdx files to the Endpoint Management console. The public store versions of the mobile productivity apps are still uploaded as MDX applications. Do not upload the apps as public store apps on the server. For steps, see Add apps.
- Change policies from their defaults based on your security policies (optional).
- Push the apps as required apps (optional). This step requires your environment to be enabled for mobile device management.
- Install apps on the device from the App Store, Google Play, or the Endpoint Management app store.
- On Android, the user is directed to the Play Store to install the app. On iOS, in deployments with MDM, the app installs without the user being taken to the app store.
- When the app is installed from the App Store or Play Store, the following action occurs. The app transitions to a managed app as long the corresponding .mdx file has been uploaded to the server. When transitioning to a managed app, the app prompts for a Citrix PIN. When users enter the Citrix PIN, Secure Mail displays the account configuration screen.
- Apps are accessible only if you’re enrolled in Secure Hub and the corresponding .mdx file is on the server. If either condition is not met, users can install the app, but usage of the app is blocked.
If you currently use apps from the Citrix Ready Marketplace™ that are on public app stores, you’re already familiar with the deployment process. Mobile productivity apps adopt the same approach that many ISVs currently use. Embed the MDX SDK within the app to make the app public-store ready.
Note:
The public store versions of the Citrix Files app for both iOS and Android are now universal. The Citrix Files app is the same for phones and tablet.
Apple push notifications
For more information on configuring push notifications, see Configuring Secure Mail for Push Notifications.
Public app store FAQs
-
Can I deploy multiple copies of the public store app to different user groups? For example, I want to deploy different policies to different user groups.
Upload a different .mdx file for each user group. However, in this case, a single user cannot belong to multiple groups. If users did belong to multiple groups, multiple copies of the same app are assigned to that user. Multiple copies of a public store app cannot be deployed to the same device, because the app ID can’t be changed.
-
Can I push public store apps as required apps?
Yes. Pushing apps to devices requires MDM; it’s not supported for MAM-only deployments.
-
Do I update any traffic policies or Exchange Server rules that are based on the user agent?
Strings for any user agent-based policies and rules by platform are as follows.
Important:
Secure Notes and Secure Tasks reached End of Life (EOL) status on December 31, 2018. For details, see EOL and deprecated apps.
Android
| App | Server | User-agent string |
|---|---|---|
| Citrix Secure Mail™ | Exchange | WorxMail |
| Lotus Notes Traveler | Apple - iPhone WorxMail | |
| Citrix Secure Web™ | WorxMail | |
| Citrix Secure Tasks | Exchange | WorxMail |
| Citrix Secure Notes | Exchange | WorxMail |
| Citrix Files | Secure Notes |
iOS
| App | Server | User-agent string |
|---|---|---|
| Citrix Secure Mail | Exchange | WorxMail |
| Lotus Notes Traveler | Apple - iPhone WorxMail | |
| Citrix Secure Web | com.citrix.browser | |
| Citrix Secure Tasks | Exchange | WorxTasks |
| Citrix Secure Notes | Exchange | WorxNotes |
| Citrix Files | Secure Notes |
-
Can I prevent app upgrades?
No. When an update is posted on the public app store, any users who have auto updates enabled receive the update.
-
Can I enforce app upgrades?
Yes, upgrades are enforced via the Upgrade grace period policy. This policy is set when the new .mdx file corresponding to the updated version of the app is uploaded to Endpoint Management.
-
How do I test the apps before the update reaches users if I can’t control the update timelines?
Similar to the process for Secure Hub, the apps are available for testing on TestFlight for iOS during the EAR period. For Android, the apps are available via the Google Play beta program during the EAR period. You can test app updates during this time.
-
What happens if I don’t update the new .mdx file before the automatic update reaches user devices?
The updated app remains compatible with the older .mdx file. Any new features that depend on a new policy are not enabled.
-
Will the app transition to managed if Secure Hub is installed or does the app need to be enrolled?
Users must be enrolled in Secure Hub for the public store app to activate as a managed app (secured by MDX) and to be usable. If Secure Hub is installed, but not enrolled, the user cannot use the public store app.
-
Do I need an Apple Enterprise developer account for the public store apps?
No. Because Citrix is now maintaining the certificates and provisioning profiles for mobile productivity apps, an Apple Enterprise developer account is not required to deploy the apps to users.
-
Does the end of enterprise distribution apply to any wrapped application I have deployed?
No, it applies only to the mobile productivity apps: Secure Mail, Secure Web, and Citrix Content Collaboration™ for Endpoint Management, QuickEdit, and ShareConnect. Any enterprise wrapped apps you deployed that are developed in-house or by third parties can continue to use enterprise wrapping. The MDX Toolkit continues to support enterprise wrapping for app developers.
-
When I install an app from Google Play, I get an Android error with error code 505.
Note:
Support for Android 5.x ended on December 31, 2018.
This is a known issue with Google Play and Android 5.x versions. If this error occurs, you can follow these steps to clear stale data on the device that prevents installation of the app:
-
Restart the device.
-
Clear the cache and data for Google Play through device settings.
-
As a last resort, remove and then add back the Google account on your device.
For more information, search this site using the following keywords “Fix Google Play Store Error 505 in Android: Unknown Error Code”
-
Although the app on Google Play has been released to production and a new beta release is not available, why do I see Beta after the app title on the Google Play?
If you are part of our Early Access Release (EAR) program, you always see Beta next to the app title. This name simply notifies users of their access level for a particular app. The Beta name indicates that users receive the most recent version of the app available. The most recent version may be the latest version is published to a production track or to a beta track.
-
After installing and opening the app, users see the message App Not Authorized, even though the .mdx file is in the Endpoint Management console.
This issue can happen if users install the app directly from the App Store or Google Play and if Secure Hub is not refreshed. Secure Hub must be refreshed when the inactivity timer is expired. Policies refresh when users open Secure Hub and reauthenticate. The app is authorized the next time users open the app.
-
Do I need an access code to use the app? I see a screen prompting me to enter an access code when I install the app from the App Store or Play Store.
If you see a screen requesting an access code, you are not enrolled in Endpoint Management through Secure Hub. Enroll with Secure Hub and ensure that the .mdx file for the app is deployed on the server. Also ensure that the app can be used. The access code is limited to Citrix internal use only. Apps require an Endpoint Management deployment to be activated.
-
Can I deploy iOS public store apps via VPP or DEP?
Endpoint Management is optimized for VPP distribution of public store apps that are not MDX-enabled. Although you can distribute the Endpoint Management public store apps with VPP, the deployment is not optimal, until we make further enhancements to Endpoint Management and the Secure Hub store to address the limitations. For a list of known issues with deploying the Endpoint Management public store apps via VPP, in addition to potential workarounds, see this article in the Citrix knowledge center.
MDX policies for mobile productivity apps
MDX policies enable you to configure settings that Endpoint Management enforces. The policies cover authentication, device security, network requirements and access, encryption, app interaction, app restrictions, and more. Many MDX policies apply to all mobile productivity apps. Some policies are app-specific.
Policy files are provided as .mdx files for the public store versions of the mobile productivity apps. You can also configure policies in the Endpoint Management console when you add an app.
For full descriptions of the MDX policies, see the following articles in this section:
- MDX policies for mobile productivity apps at a glance
- MDX policies for mobile productivity apps for Android
- MDX policies for mobile productivity apps for iOS
The following sections describe the MDX policies related to user connections.
Dual mode in Secure Mail for Android
A mobile application management (MAM) SDK is available to replace areas of MDX functionality that aren’t covered by iOS and Android platforms. The MDX wrapping technology is scheduled to reach end of life (EOL) in September 2021. To continue managing your enterprise applications, you must incorporate the MAM SDK.
From version 20.8.0, Android apps are released with the MDX and MAM SDK to prepare for the MDX EOL strategy mentioned earlier. The MDX dual mode is intended to provide a way to transition to new MAM SDKs from the current MDX Toolkit. Using dual mode allows you to either:
- Continue managing apps using MDX Toolkit (now named Legacy MDX in the Endpoint Management console)
-
Manage apps that incorporate the new MAM SDK.
Note:
When you use the MAM SDK, you do not need to wrap apps.
There are no additional steps required after you switch to the MAM SDK.
For more details about the MAM SDK, see the following articles:
- MAM SDK Overview
- Latest releases of MAM SDK
- Citrix Developer section on Device Management
- Citrix blog post
Prerequisites
For a successful deployment of the dual mode feature, ensure the following:
- Update your Citrix Endpoint Management to versions 10.12 RP2 and later, or 10.11 RP5 and later.
- Update your mobile apps to version 20.8.0 or later.
- Update the policies file to version 20.8.0 or later.
- If your organization uses third-party apps, make sure to incorporate the MAM SDK into your third-party apps before you switch to the MAM SDK option for your Citrix mobile productivity apps. All of your managed apps must be moved to the MAM SDK at one time.
Note:
MAM SDK is supported for all cloud-based customers.
Limitations
- MAM SDK supports only apps published under the Android Enterprise platform on your Citrix Endpoint Management™ deployment. For the newly published apps, the default encryption is platform-based encryption.
- MAM SDK only supports platform-based encryption, and not MDX encryption.
- If you don’t update Citrix Endpoint Management, and the policy files are running on version 20.8.0 and later for the mobile apps, then duplicate entries of the Networking policy are created for Secure Mail.
When you configure Secure Mail in Citrix Endpoint Management, the dual mode feature allows you to either continue managing apps using the MDX Toolkit (now Legacy MDX) or switch to the new MAM SDK for app management. Citrix recommends that you switch to MAM SDK, as MAM SDKs are more modular and intend to allow you to use only a subset of the MDX functionality that your organization uses.
You get the following options for policy settings in the MDX or MAM SDK policy container:
- MAM SDK
- Legacy MDX
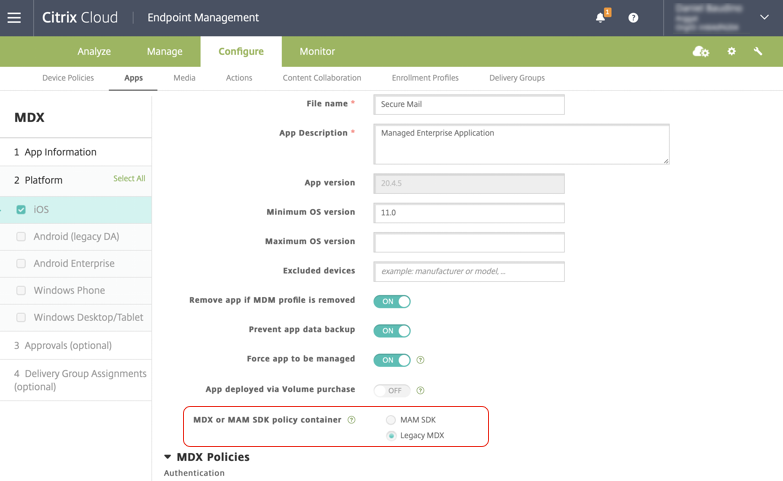
In the MDX or MAM SDK policy container policy, you can only change your option from Legacy MDX to MAM SDK. The option to switch from MAM SDK to Legacy MDX is not allowed, and you need to republish the app. The default value is Legacy MDX. Ensure that you set the same policy mode for both Secure Mail and Secure Web running on the same device. You cannot have two different modes running on the same device.
User connections to the internal network
Connections that tunnel to the internal network can use a full VPN tunnel or a variation of a clientless VPN, referred to as Tunneled – Web SSO. The Preferred VPN mode policy controls that behavior. By default, connections use Tunneled – Web SSO, which is recommended for connections that require SSO. The full VPN tunnel setting is recommended for connections that use client certificates or end-to-end SSL to a resource in the internal network. The setting handles any protocol over TCP and can be used with Windows and Mac computers, and with iOS and Android devices.
The Permit VPN mode switching policy allows automatic switching between the full VPN tunnel and Tunneled – Web SSO modes as needed. By default, this policy is off. When this policy is on, a network request that fails due to an authentication request that cannot be handled in the preferred VPN mode is retried in the alternate mode. For example, server challenges for client certificates can be accommodated by the full VPN tunnel mode, but not Tunneled – Web SSO mode. Similarly, HTTP authentication challenges are more likely to be serviced with SSO when using Tunneled – Web SSO mode.
Network access restrictions
The Network access policy specifies whether restrictions are placed on network access. By default, Secure Mail access is unrestricted, which means no restrictions are placed on network access. Apps have unrestricted access to networks to which the device is connected. By default, Secure Web access is tunneled to the internal network, which means a per-application VPN tunnel back to the internal network is used for all network access and Citrix ADC split tunnel settings are used. You can also specify blocked access so that the app operates as if the device has no network connection.
Do not block the Network access policy if you want to allow features such as AirPrint, iCloud, and Facebook and Twitter APIs.
The Network access policy also interacts with the Background network services policy. For details, see Integrating Exchange Server or IBM Notes Traveler Server.
Endpoint Management client properties
Client properties contain information that is provided directly to Secure Hub on user devices. Client properties are located in the Endpoint Management console in Settings > Client > Client Properties.
Client properties are used to configure settings such as the following:
User password caching
User password caching allows the users’ Active Directory password to be cached locally on the mobile device. If you enable user password caching, users are prompted to set a Citrix PIN or passcode.
Inactivity timer
The inactivity timer defines the time in minutes that users can leave their device inactive and can access an app without being prompted for a Citrix PIN or passcode. To enable this setting for an MDX app, you must set the App passcode policy to On. If the App passcode policy is Off, users are redirected to Secure Hub to perform a full authentication. When you change this setting, the value takes effect the next time users are prompted to authenticate.
Citrix PIN authentication
Citrix PIN simplifies the user authentication experience. The PIN is used to secure a client certificate or save Active Directory credentials locally on the device. If you configure PIN settings, the user sign-on experience is as follows:
-
When users start Secure Hub for the first time, they receive a prompt to enter a PIN, which caches the Active Directory credentials.
-
When users next start a mobile productivity app such as Secure Mail, they enter the PIN and sign on.
You use client properties to enable PIN authentication, specify the PIN type, and specify PIN strength, length, and change requirements.
Fingerprint or touch ID authentication
Fingerprint authentication, also known as touch ID authentication, for iOS devices is an alternative to Citrix PIN. The feature is useful when wrapped apps, except for Secure Hub, are in need offline authentication, such as when the inactivity timer expires. You can enable this feature in the following authentication scenarios:
- Citrix PIN + Client certificate configuration
- Citrix PIN + Cached AD password configuration
- Citrix PIN + Client certificate configuration and Cached AD password configuration
- Citrix PIN is off
If fingerprint authentication fails or if a user cancels the fingerprint authentication prompt, the wrapped apps fall back to Citrix PIN or AD password authentication.
Fingerprint authentication requirements
-
iOS devices (minimum version 8.1) that support fingerprint authentication and have at least one fingerprint configured.
-
User entropy must be off.
To configure fingerprint authentication
Important:
If user entropy is on, the Enable Touch ID Authentication property is ignored. User entropy is enabled through the Encrypt secrets using the Passcode key.
-
In the Endpoint Management console, go to Settings > Client > Client Properties.
-
Click Add.
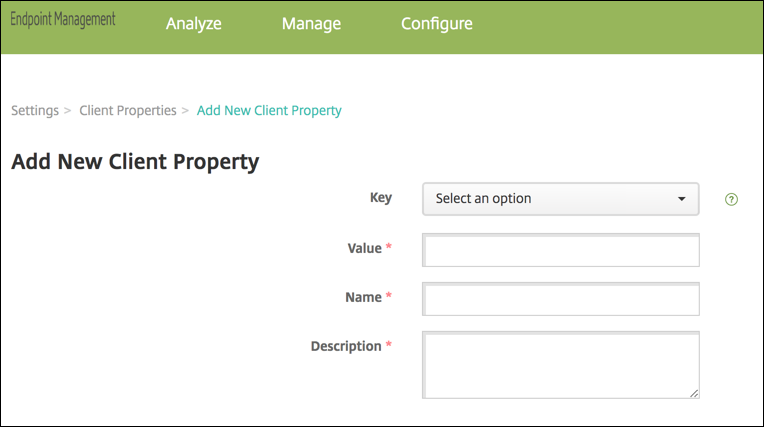
-
Add the key ENABLE_TOUCH_ID_AUTH, set its Value to True and then set the policy name to Enable Fingerprint Authentication.
After you configure fingerprint authentication, users do not need to reenroll their devices.
For more information about the Encrypt Secrets using Passcode key and client properties in general, see the Endpoint Management article about Client properties.
Google Analytics
Citrix Secure Mail uses Google Analytics for collecting app statistics and usage information analytics data to improve product quality. Citrix does not collect or store any other personal user information.
Disable Google Analytics
Admins can disable Google Analytics by configuring the custom client property DISABLE_GA. To disable Google analytics, do the following:
- Sign in to the Citrix Endpoint Management console and navigate to Settings > Client Properties > Add New Client Property.
- Add the value DISABLE_GA to the Key field.
- Set the value of the client property to true.
Note:
If you don’t configure the value DISABLE_GA in the Citrix Endpoint Management console, Google Analytics data is active.