This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Troubleshooting
To confirm that EDT is being used as the transport protocol for the session, you can use Director or the CtxSession.exe command-line utility on the VDA.
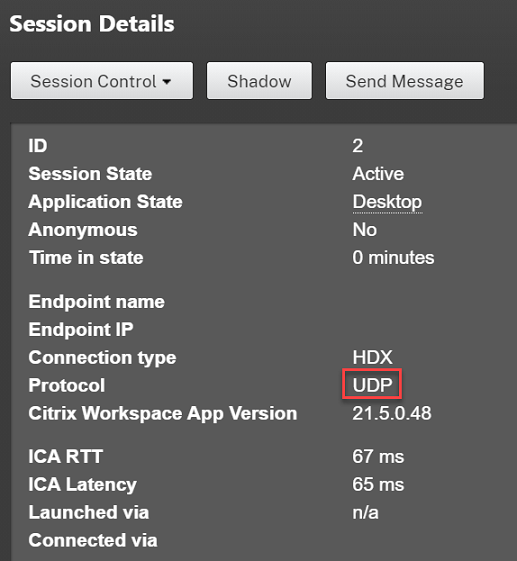
In Director, look up the session and select Details. If the Connection type is HDX and the Protocol is UDP, EDT is being used as the transport protocol for the session.
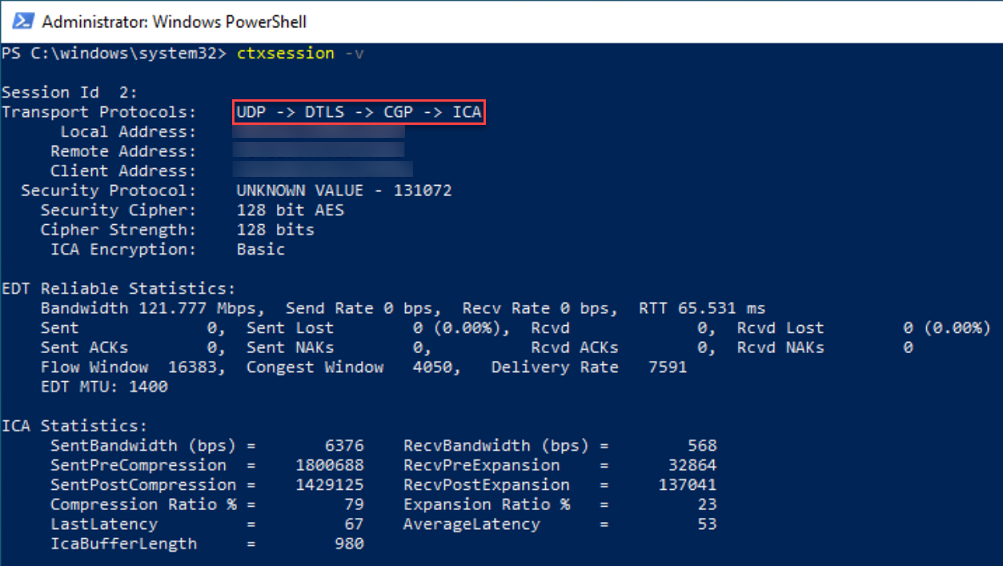
To use the CtxSession.exe utility, launch a Command Prompt or PowerShell within the session and run ctxsession.exe. To see verbose statistics, run ctxsession.exe -v. If EDT is in use, the transport protocol shows one of the following:
- UDP > ICA® (Session Reliability disabled)
- UDP > CGP > ICA (Session Reliability enabled)
- UDP > DTLS > CGP > ICA (ICA is DTLS-encrypted end-to-end)
When sessions fail to connect with EDT
To troubleshoot Adaptive Transport and EDT, we suggest the following:
- Review the System requirements, Network requirements, Known issues, and Things to know, and ensure that all items have been addressed.
- Check if there are Citrix® policies in Studio or GPO overwriting the desired HDX Adaptive Transport setting.
- Check if there are settings on the client overwriting the desired HDX Adaptive Transport setting. This can be a GPO preference, a setting configured using the optional Workspace app administrative template, or a manual configuration of the HDXoverUDP setting in the registry or client’s configuration file.
- On multi-session VDA machines, ensure that the UDP listeners are active. Open a command prompt in the VDA machine and run
netstat -a -p udp. For more information, see How to Confirm HDX Enlightened Data Transport Protocol. - Check if the appropriate firewall rules have been configured in both network firewalls and firewalls running on the VDA machines.
- Launch a direct session internally, bypassing the NetScaler® Gateway or Citrix Gateway Service, and check the protocol in use. If the session uses EDT, the VDA is ready to use EDT for external connections through NetScaler Gateway or Citrix Gateway Service.
-
If EDT works for direct internal connections and not for sessions going through NetScaler Gateway or Citrix Gateway Service:
- Ensure that Session Reliability is enabled.
- If using NetScaler Gateway, ensure that your configuration adheres to the required configuration outlined in Configure NetScaler Gateway to support Enlightened Data Transport and HDX Insight.
- If using Citrix Gateway Service, ensure that Rendezvous is enabled and working.
- Check if your users’ connections require a non-standard MTU. Connections with an effective MTU lower than 1500 bytes cause EDT packet fragmentation, which in turn can affect performance or even cause session launch failures. This issue is common when using VPNs, some Wi-Fi access points, and mobile networks, such as 4G and 5G. Ensure that you either have MTU Discovery enabled or are setting a custom MTU as outlined in How to configure MSS when using EDT on networks with non-standing MTU.
Known issues
-
Asymmetrical network paths can cause MTU Discovery to fail for connections that do not go through NetScaler Gateway or Citrix Gateway Service. To address this issue, upgrade to VDA version 2103 or later. [CVADHELP-16654]
-
When using NetScaler Gateway, asymmetrical network paths can cause MTU Discovery to fail. This is due to an issue on Gateway that causes the Don’t Fragment (DF) bit in the EDT packets’ header not to be propagated. A fix for this issue is available, starting with firmware release 13.1 build 17.42. For details on how to enable the fix, see the NetScaler Gateway documentation. [CGOP-18438]
-
MTU Discovery can fail for users that connect through a DS-Lite network. Some modems fail to honor the DF bit when packet processing is enabled, preventing MTU Discovery from detecting fragmentation. In this situation, the following are the available options:
- Disable packet processing on the user’s modem.
- Disable MTU Discovery and use a hardcoded MTU as described in How to configure MSS when using EDT on networks with non-standing MTU.
- Disable Adaptive Transport to force sessions to use TCP. If only a subset of users are affected, consider disabling it on the client side so that other users can continue to use EDT.
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.