Device certificate check with Device Posture service
To configure device certificate checks with the Device Posture service, admins must import an issuer certificate from their device. Once a valid issuer certificate is present in the Device Posture service, admins can use device certificate checks as part of device posture policies.
Points to note:
- Device Posture service supports only PEM issuer certificate type.
- For the device certificate check on Windows, the EPA client on the end device must be installed with administrative rights. For other checks, you do not require the local administrative rights. For details on the supported scans, see Scans supported by device posture.
To install the EPA client with administrative rights on Windows, run the following command in the location where the EPA client plug-in is downloaded.
msiexec /i epasetup.msi- The device certificate check with the Device Posture service does not support the certificate revocation check.
If a device certificate is signed by an intermediate certificate, then you must upload the complete chain containing the root and the intermediate certificates in a single PEM file.
Example: chain.pem -----BEGIN CERTIFICATE----- ****************************** -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- ****************************** -----END CERTIFICATE
Upload device certificate
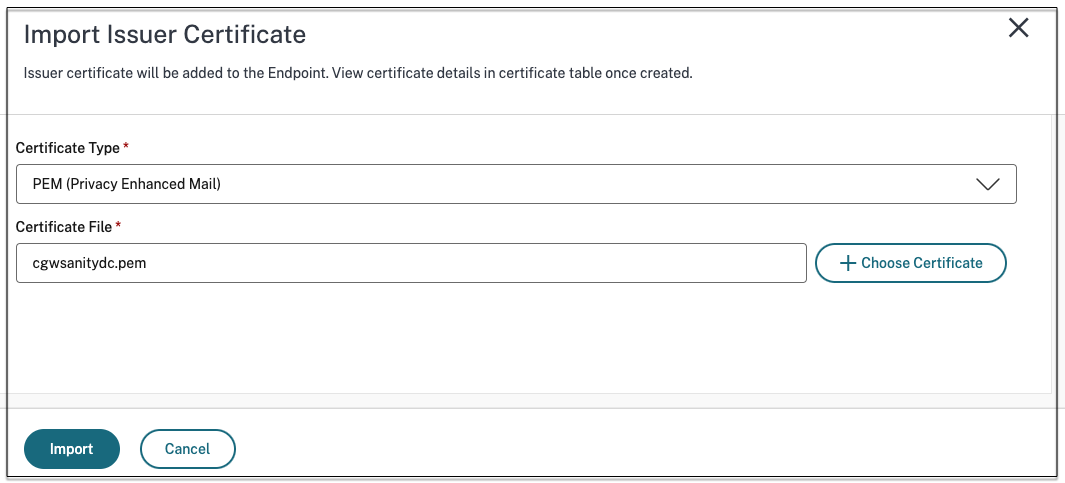
- Click Settings on the Device Posture home page.
- Click Manage, and then click Import Issue Certificate.
- In Certificate Type, select the certificate type. Only the PEM type is supported.
- In Certificate File, click Choose Certificate to select the issuer certificate.
- Click Open, and then click Import.
The selected certificate is listed in Settings > Issuer Certificates. You can import multiple certificates.
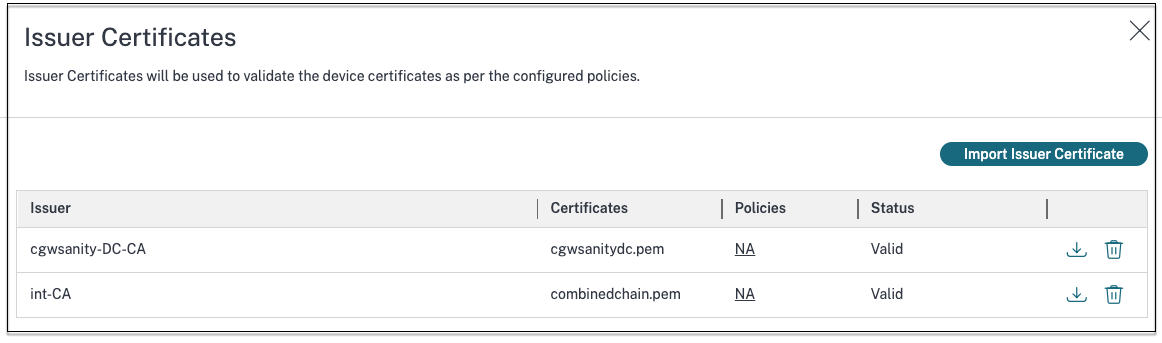
View imported certificates
- Click Settings on the Device Posture home page.
- In Issuer Certificates, click Manage.
- The Issuer Certificates page lists the imported issuer certificates.
Install the device certificate on the end device
Windows:
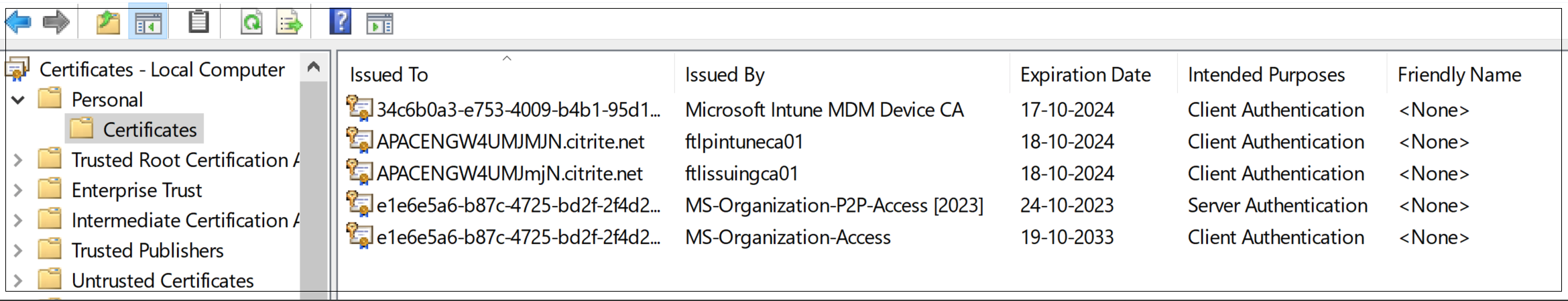
- From the Start menu, open Computer Certificate manager.
-
Ensure that the certificate is installed in
Certificates - Local Computer\Personal\Certificates.- The Intended Purposes must include Client Authentication.
- The Issued By column must match the issuer name configured on the admin GUI.
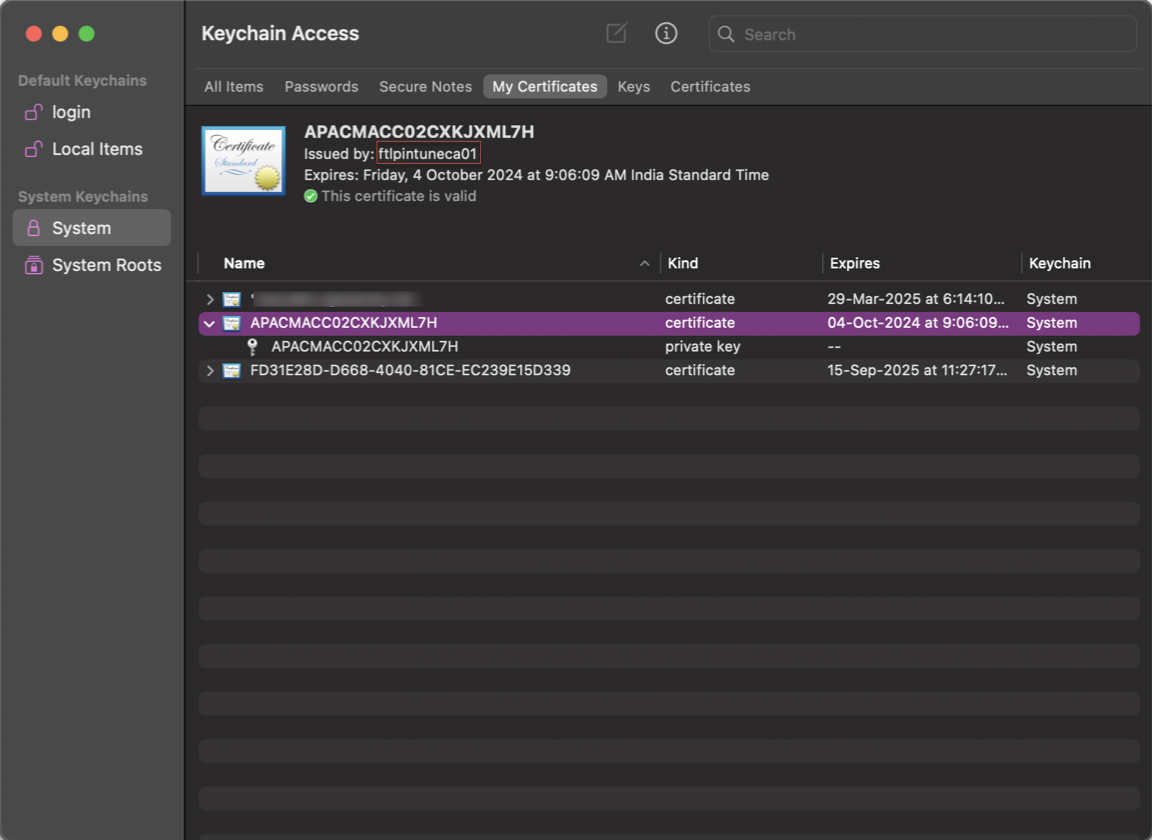
macOS:
- Open Keychain Access and then select System.
-
Click File > Import items to import the certificate.
The Issued by field must display the certificate issuer name.