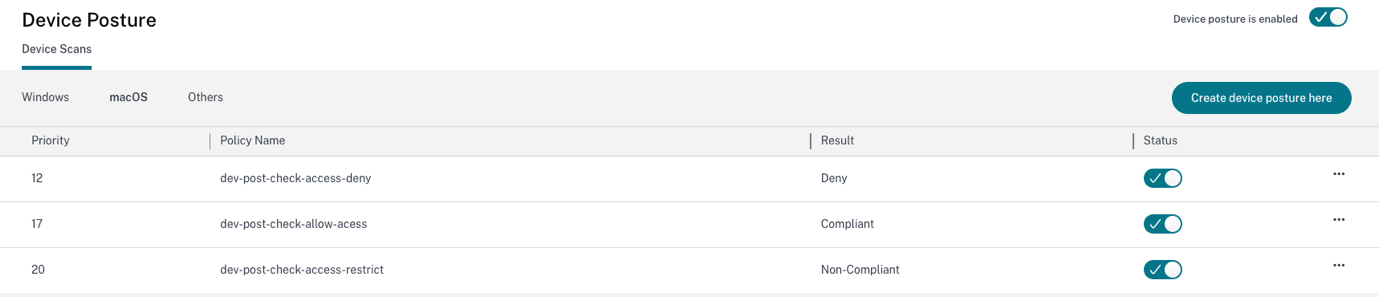
Configure Device Posture policies
Device posture is a combination of policies and rules that a device must meet to gain access to the resources. Each policy is attached with one of the actions namely compliant, non-compliant, and denied login. In addition, each policy is associated with a priority and the policy evaluation stops if a policy evaluates to true and the associated action is taken.
- Sign in to Citrix Cloud™, and then select Identity and Access Management from the hamburger menu.
-
Click the Device Posture, tab and then click Manage.
Note:
- Secure Private Access service customers can directly click Device Posture on the left navigation in the admin user interface.
- For the first-time users, the Device Posture landing page prompts you to create a device posture policy. Device posture policy must individually be configured for each platform. Once you create a device posture policy, it gets listed under the appropriate platforms.
- A policy comes into effect only after device posture is enabled. To enable device posture, slide the Device posture is disabled toggle on the right hand top corner to ON.
- Click Create device policy.
-
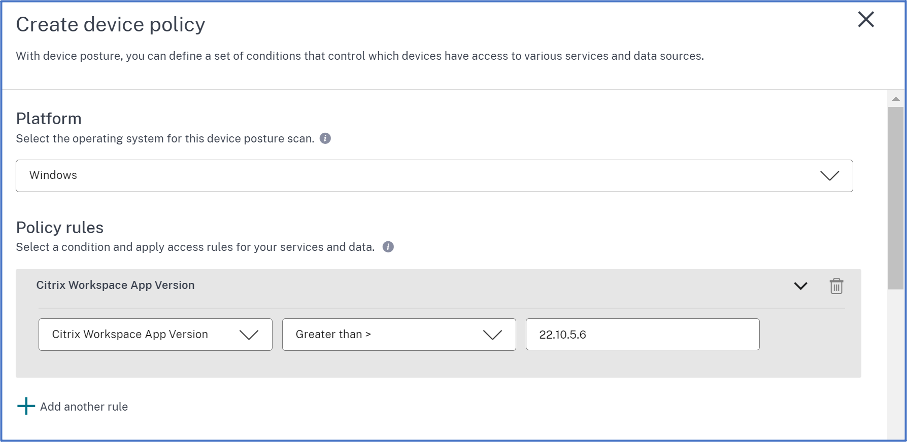
In Platform, select the platform for which you want to apply a policy. You can change the platform from Windows to macOS or conversely irrespective of the tab that you selected on the Device Posture home page.
-
In Policy rules, select the check that you want to perform as part of device posture and select the conditions that must be matched.
Note:
- The Multi-Value Non Numeric Registry scan allows administrators to determine if a device is managed or unmanaged. This is achieved by evaluating several registry key values.
-
Note the following points regarding Device Certificate check:
- Ensure that the issuer certificate exists on the device. Else, you can import a device certificate while creating the device posture policy or upload the certificate from Settings on the Device Posture home page. For details, Device certificate check.
- In environments where multiple device certificates share a common issuer name, the Device Posture service might evaluate the wrong certificate. To ensure the service identifies the exact certificate for a specific policy, you must explicitly enable the Check Thumbprint option. For details, see Configure device certificate check scans.
- The EPA client on the end device must be installed with administrative rights.
- The device certificate check with the Device Posture service does not support the Certificate Revocation check.
- Ensure that the issuer certificate exists on the device. Else, you can import a device certificate while creating the device posture policy or upload the certificate from Settings on the Device Posture home page. For details, Device certificate check.
- When creating a policy rule for network location check, you can add a network location directly from the Device Posture service console. However, to modify the network location, you must use the Network Location configuration on Citrix Cloud.
-
Click Add another rule to create multiple rules. An AND condition is applied on multiple rules.
-
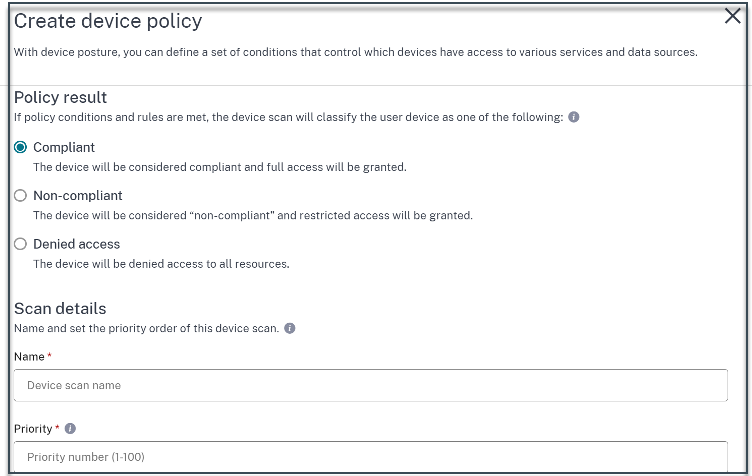
In Policy result based on the conditions that you’ve configured, select the type under which the device scan must classify the user device.
- Compliant
- Non-compliant
- Denied access
- Enter a name for the policy.
-
In Priority, enter the order in which the policies must be evaluated.
- You can enter a value between 1 through 100. It’s recommended that you configure deny policies with higher priority, followed by non-compliant, and finally compliant.
- The priority with the lower value has the highest preference.
- Only the policies that are enabled are evaluated based on the priority.
-
Click Create.
Important:
You must turn the Enable when created toggle switch to ON for the device posture policies to take effect. Before you enable the policies, it’s recommended that you ensure that the policies are correctly configured and you’re performing these tasks in your test setup.
Configure contextual access (smart access) using device posture
After the device posture verification, the device is allowed to log in and classified as compliant or non-compliant. This information is available as tags to the Citrix DaaS service and Citrix Secure Private Access™ service and is used to provide contextual access based on device posture. Therefore, Citrix DaaS and Citrix Secure Private Access must be configured to enforce access control using device posture tags.
Citrix DaaS configuration with Device Posture
To restrict access to the DaaS resources, you can specify the delivery groups on which access restrictions must be enforced and configure the access control restrictions using the Device Posture tags.
Prerequisites:
Ensure that the Adaptive Access feature is enabled (Citrix Workspace > Access > Adaptive Access). For details, see Enable the Adaptive Access feature.
- Sign into Citrix Cloud.
- On the DaaS tile, click Manage.
- Go to the Delivery Group section from the left-hand menu.
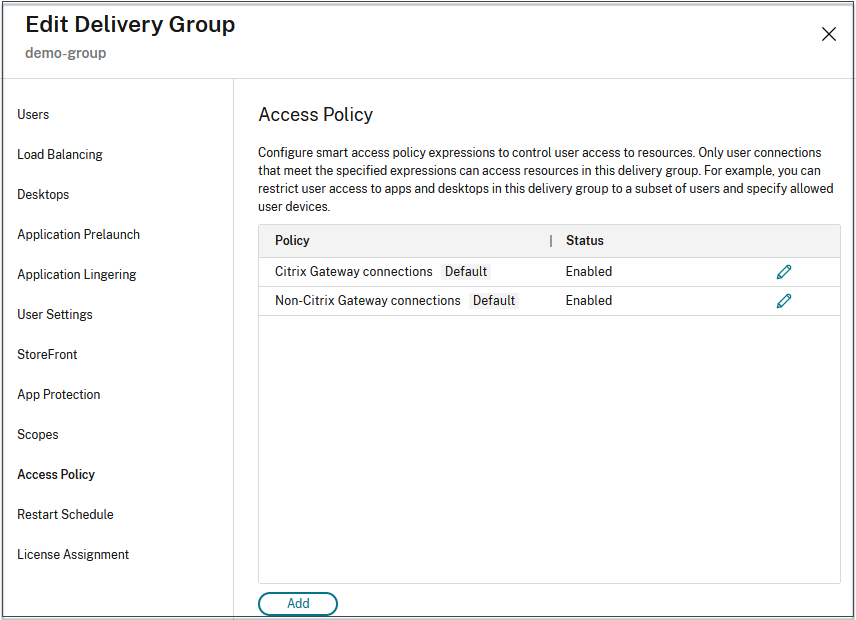
- Select the delivery group for which you want to configure access control based on device posture and click Edit.
- In the Edit Delivery Group page, click Access Policy.
-
Click the edit icon on the Citrix Gateway connections row to edit the gateway connections policy.
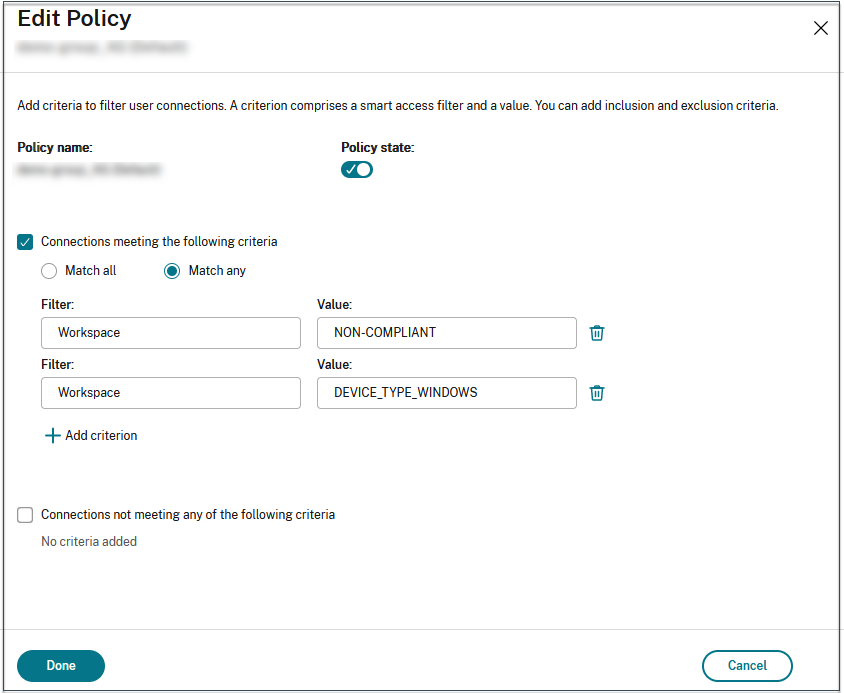
- On the Edit policy page, select Connections meeting the following criteria.
- Select Match any, and then click Add criterion.
- Add criteria for all location tags you configured in Configure network locations: Type Workspace for Filter and COMPLIANT or NON-COMPLIANT for Value.
Note:
The syntax for the device classification tags must be entered exactly as captured earlier, that is all in uppercase (COMPLIANT and NON-COMPLIANT). Else the device posture policies do not work as intended.
In addition to the device classification tags, the Device Posture service also returns the operating system tag and the access policy tag associated with the device. The operating system tags and the access policy tags must be entered in uppercase only.
- DEVICE_TYPE_WINDOWS
- DEVICE_TYPE_MAC
- Exact policy name (uppercase)
Citrix Secure Private Access configuration with Device Posture
To restrict access to the Secure Private Access resources, you can select the applications on which access restrictions must be enforced and configure the access control restrictions using the Device Posture tags.
- Sign into Citrix Cloud.
- On the Secure Private Access tile, click Manage.
- Click Access Policies on the left navigation and then click Create policy.
- Enter the policy name and description of the policy.
- In Applications, select the app or set of apps on which this policy must be enforced.
- Click Create Rule to create rules for the policy.
- Enter the rule name and a brief description of the rule, and then click Next.
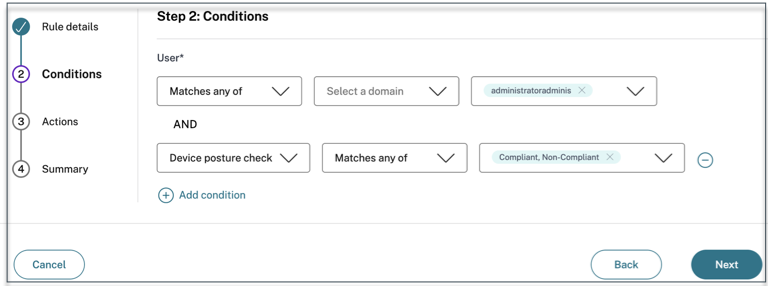
- Select the users’ conditions. The Users condition is a mandatory condition to be met to grant access to the applications for the users.
- Click + to add device posture condition.
- Select Device posture check and the logical expression from the drop-down menu.
-
Enter one of the following values in the custom tags:
- Compliant - For compliant devices
- Non-Compliant - For non-compliant devices
Note:
The tags must be entered exactly as captured earlier, using initial caps (Compliant and Non-Compliant). Otherwise, the device posture policies do not function as intended.
- Click Next.
-
Select the actions that must be applied based on the condition evaluation, and then click Next.
The Summary page displays the policy details.
-
You can verify the details and click Finish.
For more details on creating access policies, see Configure an access policy with multiple rules.
Note:
Any Secure Private Access application, which isn’t tagged as compliant or non-compliant in the access policy is treated as the default application and is accessible on all the endpoints regardless of device posture.
Edit a device posture policy
The configured device posture policies are listed under the specific platform in the Device Scans page. You can search for the policy you want to edit from this page. You can also enable, disable, or delete a policy from this page.