Scenario 2
This scenario covers how to disable App Protection for connections started from browser-based access and enable App Protection for connections started from Citrix Workspace app.
The following are the steps to disable App Protection for a delivery group called Win10Desktop when connections are started from a browser and enable App Protection for connections from Citrix Workspace app:
-
Create Smart Access policies:
-
Create a Smart Access policy to filter the connections started from the Citrix Workspace app, as defined in the preceding scenario Disable App Protection for certain device types. Create the following expression, to check for CitrixReceiver in the User Agent string:
HTTP.REQ.HEADER("User-Agent").CONTAINS("CitrixReceiver") <!--NeedCopy-->In this scenario, the Smart Access policy is
cwa.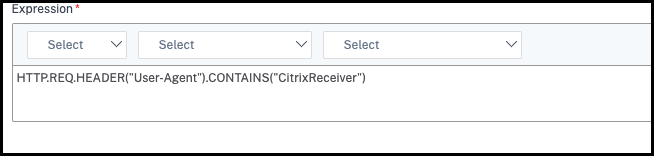
-
Create another Smart Access policy to filter the connections that aren’t started from the Citrix Workspace app,
HTTP.REQ.HEADER("User-Agent").CONTAINS("CitrixReceiver").NOT. In this case, this Smart Access policy is browser.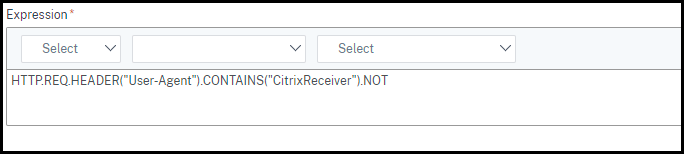
-
-
Create Broker Access policy rules:
-
Run
GetBrokerAccessPolicyRuleto view the two broker access policies forWin10Desktop. For the delivery groupWin10Desktop, the broker access policies areWin10Desktop_AGandWin10Desktop_Direct. Note the Desktop Group UID ofWin10Desktop. -
Create a Broker Access policy for
Win10Desktopto filter connections started from the Citrix Workspace app by using the following command:New-BrokerAccessPolicyRule -Name Win10Desktop_AG_CWA -DesktopGroupUid <Uid_of_desktopGroup> -AllowedConnections ViaAG -AllowedProtocols HDX, RDP -AllowedUsers AnyAuthenticated -AllowRestart $true -Enabled $true -IncludedSmartAccessFilterEnabled $true <!--NeedCopy-->Uid_of_desktopGroup is the DesktopGroupUID of the delivery group got by running the GetBrokerAccessPolicy Rule in step 1.
-
Use the following command to enable App Protection policies only for connections coming through CWA by referencing the Smart Access tag
cwa:Set-BrokerAccessPolicyRule Win10Desktop_AG_CWA -IncludedSmartAccessTags Primary_HDX_Proxy:cwa -AppProtectionScreenCaptureRequired $true -AppProtectionKeyLoggingRequired $true <!--NeedCopy-->Primary_HDX_Proxy is the VPN virtual server name noted down earlier in Step 1, Create Smart Access Policy.
-
Use the following command to disable App Protection policies for the rest of the connections coming through the browser:
Set-BrokerAccessPolicyRule Win10Desktop_AG -IncludedSmartAccessTags Primary_HDX_Proxy:browser -AppProtectionScreenCaptureRequired $false -AppProtectionKeyLoggingRequired $false <!--NeedCopy-->
-
-
Verification
Sign out of Citrix Workspace app, if already open. Sign in to Citrix Workspace app again and launch the required resource from an external connection through an access gateway. You can see that the App Protection policies are enabled for the resource. Launch the same resource from the browser through an external connection and you can see that the App Protection policies are disabled.