Secure communications
To secure the communication between your site and Citrix Workspace app, you can integrate your Citrix Workspace app connections using secure technologies such as Citrix Gateway.
Note:
Citrix recommends using Citrix Gateway between StoreFront servers and user devices.
-
A firewall: Network firewalls can allow or block packets based on the destination address and port. If you’re using Citrix Workspace app through a network firewall that maps the server’s internal network IP address to an external Internet address (that is, network address translation, or NAT), configure the external address.
-
Trusted server.
-
For Citrix Virtual Apps and Desktops or Citrix DaaS (formerly Citrix Virtual Apps and Desktops service) deployments only (not applicable to XenDesktop 7): A SOCKS proxy server or secure proxy server (also known as security proxy server, HTTPS proxy server, or Transport Layer Security (TLS) tunneling proxy server). You can use proxy servers to limit access to and from your network and to handle connections between Citrix Workspace app and servers. Citrix Workspace app supports SOCKS and secure proxy protocols.
-
For Citrix Virtual Apps and Desktops or Citrix DaaS deployments only: Citrix Secure Web Gateway or SSL Relay solutions with TLS protocols. TLS versions 1.0 through 1.2 are supported.
Provision to manage multiple proxy servers
Previously, Citrix Workspace app did not support the usage of multiple proxy servers. Startig with the 2408 version, you can use multiple proxy servers that allow the HDX sessions to select appropriate proxy servers for accessing specific resources. This selection is based on the proxy rules configured in the Proxy Auto-Configuration (PAC) file. Using this file, you can manage the network by mentioning which network traffic must be sent through a proxy server and which must be sent directly.
This feature is disabled by default. To enable this feature, do the following:
- Navigate to the
$HOME/.ICAClient/All_Regions.inifile. -
Go to the
[Network\Proxy]section and do the following:- Update
ProxyTypetoScript. - Update
ProxyAutoConfigURLtofile://file-path,https://serverfilepath, orhttp://server/filepath.
You must replace the preceding path with the real path that you want to use for connection.
- Update
When Script is added as ProxyType, the client retrieves a JavaScript based on the .pac file from the URL specified in the Proxy script URLs policy option. The .pac file is run to identify which proxy server must be used for the connection.
Citrix Gateway
Citrix Gateway (formerly Access Gateway) secures connections to StoreFront stores. Also, lets administrators control, in a detailed way, user access to desktops and applications.
To connect to desktops and applications through Citrix Gateway:
-
Specify the Citrix Gateway URL that your administrator provides using one of the following ways:
- The first time you use the self-service user interface, you’re prompted to enter the URL in the Add Account dialog box.
- When you later use the self-service user interface, enter the URL by clicking Preferences > Accounts > Add.
- If you’re establishing a connection with the
storebrowsecommand, enter the URL at the command line.
The URL specifies the gateway and, optionally, a specific store:
- To connect to the first store that Citrix Workspace app finds, use a URL of the form, for example:
https://gateway.company.com. - To connect to a specific store, use a URL of the form, for example:
https://gateway.company.com>?\<storename\. This dynamic URL is in a non-standard form; do not include = (the equals sign character) in the URL. If you’re establishing a connection to a specific store withstorebrowse, you might need quotation marks around the URL in thestorebrowsecommand.
-
When prompted, connect to the store (through the gateway) using your user name, password, and security token. For more information on this step, see the Citrix Gateway documentation.
When authentication is complete, your desktops and applications are displayed.
Proxy server
Proxy servers are used to limit access to and from your network, and to handle connections between Citrix Workspace app and your Citrix Virtual Apps and Desktops or Citrix DaaS deployment.
Citrix Workspace app supports the SOCKS and HTTPS protocol, along with the following:
- Citrix Secure Web Gateway™ and Citrix SSL Relay, the secure proxy protocol
- Windows NT Challenge/Response (NTLM) authentication.
To configure a proxy to launch a desktop using the SOCKS protocol, do the following:
- Navigate to the
~/.ICAClient/All_Regions.iniconfiguration file. -
Update the following attributes:
- Update
ProxyType. You can useSocksV5asProxyType. -
Update
ProxyHost. You can addProxyHostin the following format:<IP>:<PORT>. For example “10.122.122.122:1080”.
- Update
Note:
- To use proxy, disable EDT. To disable EDT, set the
HDXoverUDPattribute to off in the[Network\UDT]section of the~/.ICAClient/All_Regions.iniconfiguration file.- To ensure a secure connection, enable TLS.
HTTPS protocol support for proxy server
Previously, you could connect to a proxy server only using the SOCKS protocol. From Citrix Workspace app 2308 onwards, you can connect to a proxy server using the HTTPS protocol also.
To open a desktop using an HTTPS protocol, do the following:
- Navigate to the ~/.ICAClient/All_Regions.ini configuration file.
- Go to the [Network\UDT] section.
-
Set the following:
HDXoverUDP=Off <!--NeedCopy--> - Go to the [Network\Proxy] section.
-
Update the following attributes:
- Update ProxyType. You can use Secure as ProxyType.
- Update ProxyHost. You can add ProxyHost in the following format:
<IP>:<PORT>. For example “192.168.101.37:6153”.
Secure proxy server
Configuring connections to use the secure proxy protocol also enables support for Windows NT Challenge/Response (NTLM) authentication. If this protocol is available, it’s detected and used at run time without any additional configuration.
Important:
NTLM support requires the OpenSSL 1.1.1d and libcrypto.so libraries. Install these libraries on the user device. These libraries are often included in Linux distributions. You can also download them from http://www.openssl.org/.
Secure Web Gateway and SSL
You can integrate Citrix Workspace app with the Citrix Secure Web Gateway or Secure Sockets Layer (SSL) Relay service. Citrix Workspace app supports the TLS protocol. TLS (Transport Layer Security) is the latest, standardized version of the SSL protocol. The Internet Engineering Taskforce (IETF) renamed it TLS when it took over responsibility for the development of SSL as an open standard. TLS secures data communications by providing server authentication, encryption of the data stream, and message integrity checks. Some organizations, including U.S. government organizations, require the use of TLS to secure data communications. These organizations might also require the use of validated cryptography, such as FIPS 140 (Federal Information Processing Standard). FIPS 140 is a standard for cryptography.
Secure Web Gateway
You can use the Citrix Secure Web Gateway in Normal mode or Relay mode to provide a secure channel for communication between Citrix Workspace app and the server. If you’re using the Secure Web Gateway in Normal mode, Citrix Workspace app doesn’t require any configuration.
If the Citrix Secure Web Gateway Proxy is installed on a server in the secure network, you can use the Citrix Secure Web Gateway Proxy in Relay mode. If you’re using Relay mode, the Citrix Secure Web Gateway server functions as a proxy and you must configure Citrix Workspace app to use:
- The fully qualified domain name (FQDN) of the Citrix Secure Web™ Gateway server.
- The port number of the Citrix Secure Web Gateway server.
Note:
Citrix Secure Web Gateway Version 2.0 doesn’t support Relay mode.
The FQDN must list, in sequence, the following three components:
- Host name
- Intermediate domain
- Top-level domain
For example: my_computer.my_company.com is an FQDN, because it lists, in sequence, a host name (my_computer), an intermediate domain (my_company), and a top-level domain (.com). The combination of intermediate and top-level domain (my_company.com) is referred to as the domain name.
SSL Relay
By default, Citrix SSL Relay uses TCP port 443 on the Citrix Virtual Apps and Desktops™ or Citrix DaaS server for TLS-secured communication. When the SSL Relay receives a TLS connection, it decrypts the data before redirecting it to the server.
If you configure SSL Relay to listen on a port other than 443, you must specify the non-standard listening port number to Citrix Workspace app.
You can use Citrix SSL Relay to secure communications:
- Between a TLS-enabled user device and a server
For information about configuring and using SSL Relay to secure your installation, see the Citrix Virtual Apps™ documentation.
TLS
Previously, the minimum TLS version supported was 1.0, and the maximum TLS version supported was 1.2. Starting with version 2203, the maximum TLS version supported is 1.3.
You can control the versions of the TLS protocol that can be negotiated by adding the following configuration options in the [WFClient] section:
- MinimumTLS=1.1
- MaximumTLS=1.3
These values are the default values, which are implemented in the code. Adjust them as you require.
Notes:
These values are read whenever programs start. If you change them after starting self-service or
storebrowse, type: killall AuthManagerDaemon ServiceRecord selfservice storebrowse.Citrix Workspace app for Linux does not allow the use of the
SSLv3protocol.TLS 1.0/1.1 works only with the older VDI or Citrix Gateway which support them.
To select the cipher suite set, add the following configuration option in the [WFClient] section:
- SSLCiphers=GOV
This value is the default value. Other recognized values are COM and ALL.
Note:
As with the TLS version configuration, if you change this configuration after starting self-service or storebrowse you must type: killall AuthManagerDaemon ServiceRecord selfservice storebrowse
CryptoKit update
CryptoKit Version 14.2 is integrated with the OpenSSL 1.1.1d version.
Cryptographic update
This feature is an important change to the secure communication protocol. Cipher suites with the prefix TLS_RSA_ do not offer forward secrecy and are considered weak.
The TLS_RSA_ cipher suites have been removed entirely. Instead, it supports the advanced TLS_ECDHE_RSA_ cipher suites.
If your environment isn’t configured with the TLS_ECDHE_RSA_ cipher suite, client launches aren’t supported because of weak ciphers. For client authentication, 1536-bit RSA keys are supported.
The following advanced cipher suites are supported:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030)
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028)
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013)
DTLS v1.0 supports the following cipher suites:
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_EMPTY_RENEGOTIATION_INFO_SCSV
DTLS v1.2 supports the following cipher suites:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_EMPTY_RENEGOTIATION_INFO_SCSV
TLS v1.3 supports the following cipher suites:
- TLS_AES_128_GCM_SHA256 (0x1301)
- TLS_AES_256_GCM_SHA384 (0x1302)
Note:
From version 1903 and later, DTLS is supported from Citrix Gateway 12.1 and later. For information on DTLS supported cipher suites for Citrix Gateway, see Support for DTLS protocol
Cipher suites
To enable different cipher suites, change the parameter SSLCiphers value to ALL, COM, or GOV. By default, the option is set to ALL in the All_Regions.ini file in the $ICAROOT/config directory.
The following sets of cipher suites are provided by ALL, GOV, and COM, respectively:
- ALL
- all 3 ciphers are supported.
- GOV
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030)
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028)
- COM
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013)
For troubleshooting information, see Cipher suites.
Cipher suites with the prefix TLS_RSA_ do not offer forward secrecy. These cipher suites are now deprecated in the industry. However, to support backward compatibility with older versions of Citrix Virtual Apps and Desktops or Citrix DaaS, Citrix Workspace app includes an option to enable these cipher suites.
For better security, set the flag Enable\_TLS\_RSA\_ to False.
The following is the list of deprecated cipher suites:
- TLS_RSA_AES256_GCM_SHA384
- TLS_RSA_AES128_GCM_SHA256
- TLS_RSA_AES256_CBC_SHA256
- TLS_RSA_AES256_CBC_SHA
- TLS_RSA_AES128_CBC_SHA
- TLS_RSA_3DES_CBC_EDE_SHA
- TLS_RSA_WITH_RC4_128_MD5
- TLS_RSA_WITH_RC4_128_SHA
Note:
The last two cipher suites use the RC4 algorithm and are deprecated because they’re insecure. You might also consider the TLS_RSA_3DES_CBC_EDE_SHA cipher suite to be deprecated. You can use flags to enforce all these deprecations.
For information on configuring DTLS v1.2, see the Adaptive transport section in the Citrix Virtual Apps and Desktops documentation.
Prerequisite:
If you’re using version 1901 and earlier, do the following steps:
If .ICAClient is already present in the home directory of the current user:
- Delete
All\_Regions.inifile
Or
- To keep the
AllRegions.inifile, add the following lines at the end of the [Network\SSL] section:- Enable_RC4-MD5=
- Enable_RC4_128_SHA=
- Enable_TLS_RSA_=
If the .ICAClient folder isn’t present in the home folder of the current user, it indicates a fresh install of the Citrix Workspace app. In that case, the default setting for the features is kept.
The following table lists the cipher suites in each set: Table 1 – Cipher suite support matrix
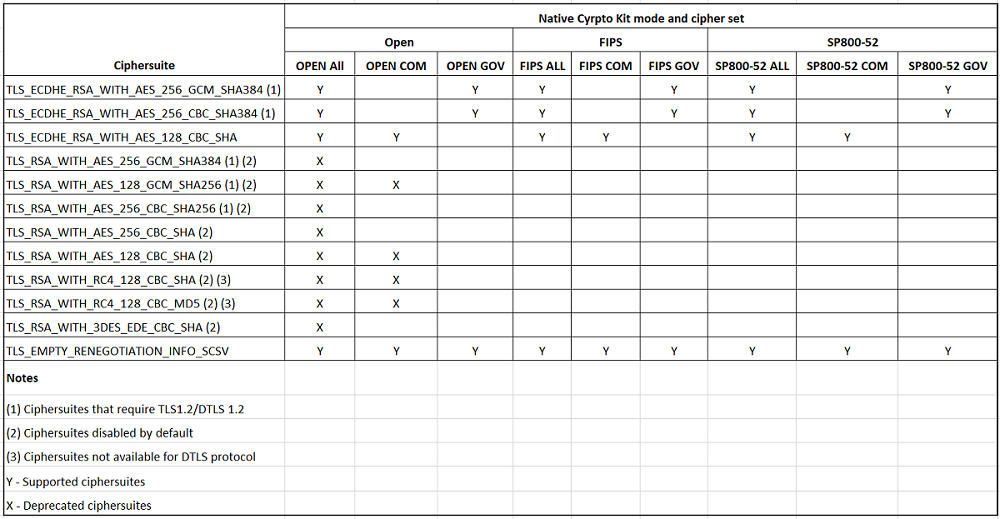
Note:
All the preceding cipher suites are
FIPS-andSP800-52-compliant. The first two are allowed only for (D)TLS1.2 connections. See Table 1 – Cipher suite support matrix for a comprehensive representation of cipher suite supportability.
Certificates
When you use a store with SAML authentication (using the AUTHv3 protocol), the following error message appears: “Unacceptable TLS Certificate.”
The issue occurs when you use Citrix Workspace app 1906 and later. For troubleshooting instructions, see the following Knowledge Center articles:
If your StoreFront server fails to provide the intermediate certificates that match the certificate it’s using, or you install intermediate certificates to support smart card users, follow these steps before adding a StoreFront store:
-
Get one or more intermediate certificates separately in PEM format.
Tip:
If you can’t find a certificate in PEM format, use the
opensslutility to convert a certificate in CRT format to a .pem file. -
As the user installs the package (usually root):
-
Copy one or more files to $ICAROOT/keystore/intcerts.
-
Run the following command as the user who installed the package:
$ICAROOT/util/ctx_rehash
-
If you authenticate a server certificate that a certificate authority issued and not trusted in the user devices, follow these instructions before adding a StoreFront store:
- Get the root certificate in PEM format.
Tip: If you can’t find a certificate in this format, use the
opensslutility to convert a certificate in CRT format to a .pem file. - As the user who installed the package (usually root):
-
Copy the file to $ICAROOT/keystore/cacerts.
-
Run the following command:
$ICAROOT/util/ctx_rehash
-
Enhancement to HDX™ Enlightened Data Transport Protocol (EDT)
In earlier releases, when HDXoverUDP is set to Preferred, data transport over EDT is used as primary with fallback to TCP.
Starting with Citrix Workspace app version 2103, when session reliability is enabled, EDT, and TCP are attempted in parallel during the following:
- Initial connection
- Session reliability reconnection
- Auto client reconnect
This enhancement reduces connection time when EDT is preferred. However, the required underlying UDP transport is unavailable and TCP must be used.
By default, after fallback to TCP, adaptive transport continues to seek EDT every five minutes.
Enlightened Data Transport (EDT) MTU discovery
Citrix Workspace app version 2109 supports Maximum Transmission Unit (MTU) discovery in Enlightened Data Transport (EDT). It increases the reliability and compatibility of the EDT protocol and provides an improved user experience.
For more information, see the EDT MTU Discovery section in the Citrix Virtual Apps and Desktops documentation.
Support for EDT IPv6
Starting with Citrix Workspace app version 2203, EDT IPv6 is supported.
Note:
IPv6is supported in both TCP and EDT. However,IPv6isn’t supported in TCP over TLS and in EDT over DTLS.
Support for IPv6 UDP with DTLS
Previously, DTLS connections between Citrix Workspace app for Linux and Virtual Delivery Agents (VDAs) were supported over the IPv4 network only.
Starting with the 2311 release, Citrix Workspace app supports DTLS connections over both IPv4 and IPv6.
This feature is enabled by default.
No additional configuration is required when you use IPv6 DTLS direct connection with VDA on Citrix Workspace app for Linux.
Support for IPv6 TCP with TLS
Previously, TLS connections between Citrix Workspace app for Linux and Virtual Delivery Agents (VDAs) were supported over the IPv4 network only.
Starting with the 2311 release, Citrix Workspace app supports TLS connections over both IPv4 and IPv6.
This feature is enabled by default.
No additional configuration is required when you use IPv6 TLS direct connection with VDA on Citrix Workspace app for Linux.