Configure NetScaler Gateway
NetScaler Gateway configuration is supported for both Web/SaaS and TCP/UDP applications. You can create a NetScaler Gateway or update an existing NetScaler Gateway configuration for Secure Private Access. It is recommended that you create NetScaler snapshots or save the NetScaler configuration before applying these changes.
Note:
- Support for TCP/UDP apps along with Web/SaaS apps is available starting from NetScaler Gateway version 14.1–25.56. However, Secure Private Access for TCP/UDP apps in hybrid deployments is supported from version 14.1-34.42 and this version significantly streamlines the configuration process.
- Support for Web/SaaS apps is available from NetScaler Gateway versions 13.1, 14.1 and later. For details about the NetScaler Gateway configuration, see Configure NetScaler Gateway.
- Secure Private Access for hybrid deployment can be enabled globally or per VPN virtual server. We recommend that you enable Secure Private Access per VPN virtual server. After Secure Private Access is enabled, TCP/UDP and Web/SaaS applications are enabled by default.
To create NetScaler Gateway for the Web/SaaS or TCP/UDP applications, perform the following steps:
-
Download the latest script
ns_gateway_secure_access.sh.from https://www.citrix.com/downloads/citrix-secure-private-access/Shell-Script/. -
Upload these scripts to the NetScaler machine. You can use the WinSCP app or the SCP command. For example,
scp ns_gateway_secure_access.sh nsroot@nsalfa.fabrikam.local:/var/tmp.For example,
scp ns_gateway_secure_access.sh nsroot@nsalfa.fabrikam.local:/var/tmpNote:
- It’s recommended to use NetScaler /var/tmp folder to store temp data.
- Make sure that the file is saved with LF line endings. FreeBSD does not support CRLF.
- If you see the error
-bash: /var/tmp/ns_gateway_secure_access.sh: /bin/sh^M: bad interpreter: No such file or directory, it means that the line endings are incorrect. You can convert the script by using any rich text editor, such as Notepad++.
- SSH to NetScaler and switch to shell (type ‘shell’ on NetScaler CLI).
-
Make the uploaded script executable. Use the chmod command to do so.
chmod +x /var/tmp/ns_gateway_secure_access.sh -
Run the uploaded script on the NetScaler shell.
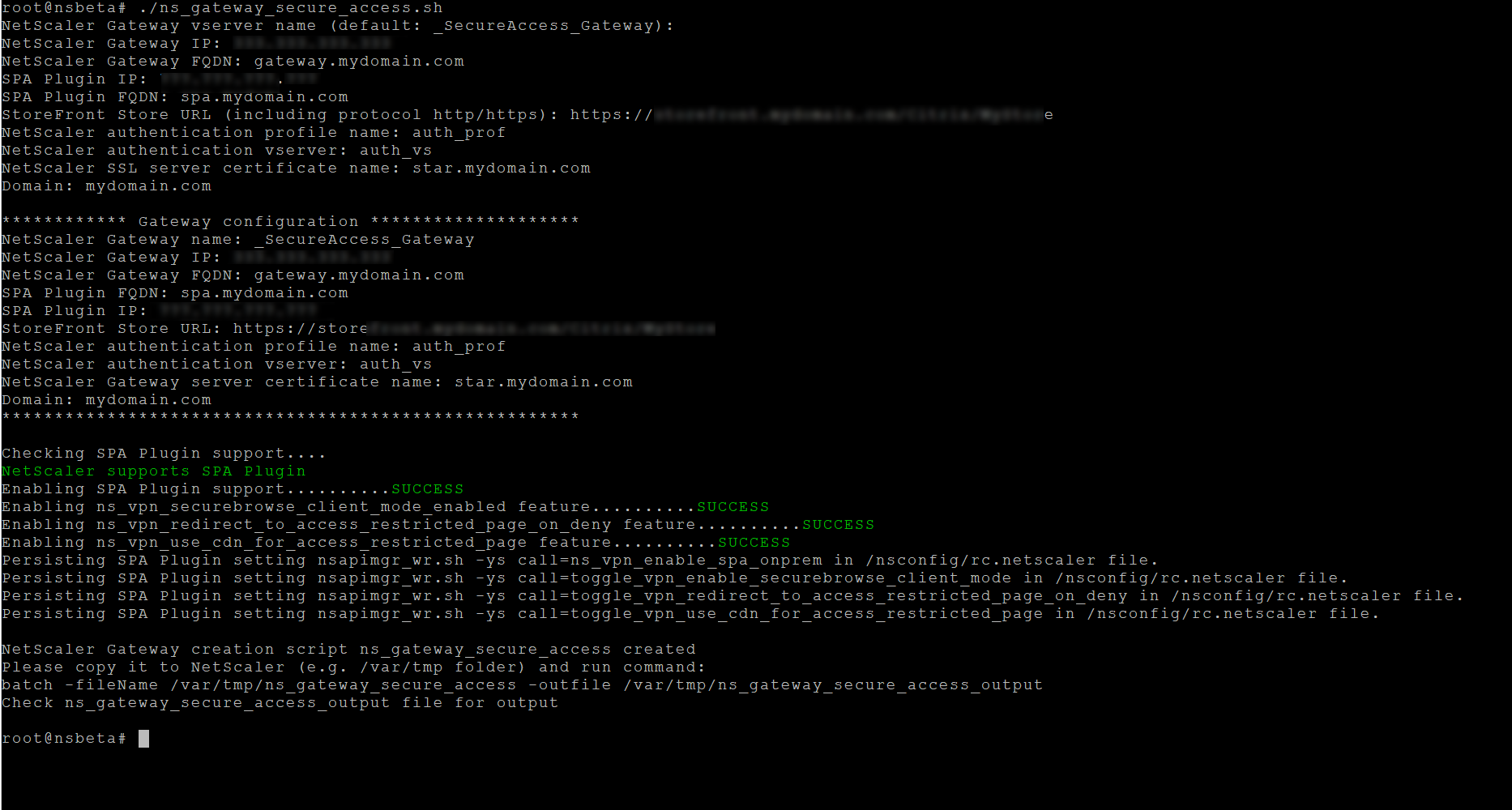
-
Input the required parameters. For the list of parameters, see Prerequisites.
For the authentication profile and SSL certificate you have to provide names of existing resources on NetScaler.
A new file with multiple NetScaler commands (the default is var/tmp/ns_gateway_secure_access) is generated.
Note:
During script execution, NetScaler and Secure Private Access provider compatibility is checked. If NetScaler supports the Secure Private Access provider, the script enables NetScaler features to support smart access tags sending improvements and redirection to a new Deny Page when access to a resource is restricted.
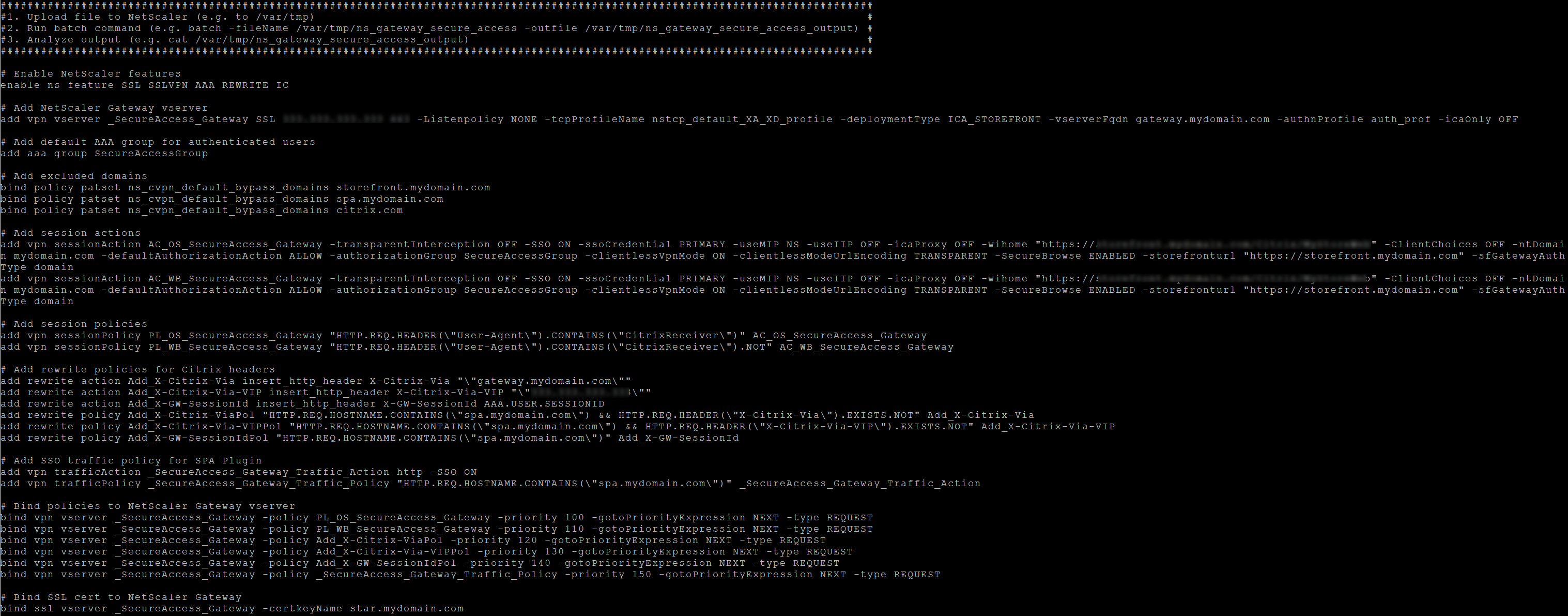
-
Switch to the NetScaler CLI and run the resultant NetScaler commands from the new file with the batch command. For example;
batch -fileName /var/tmp/ns_gateway_secure_access -outfile/var/tmp/ns_gateway_secure_access_outputNetScaler runs the commands from the file one by one. If a command fails, it continues with the next command.
A command can fail if a resource exists or one of the parameters entered in step 6 is incorrect.
- Ensure that all commands are successfully completed.
Note:
- If a load balancer is configured, ensure that you provide the load balancer URL while binding the Secure Private Access provider to the VPN virtual server. Example:
bind vpn vserver spahybrid -securePrivateAccessUrl "https://spa.example.corp"- If there’s an error, NetScaler still runs the remaining commands and partially creates/updates/binds resources. Therefore, if you see an unexpected error because of one of the parameters being incorrect, it’s recommended to redo the configuration from the start.
Points to note
- Existing NetScaler Gateway can be updated with script but there can be a significant number of possible NetScaler configurations that can’t be covered by a single script.
- We recommend that you set ICA Proxy to OFF in the Secure Private Access enabled VPN virtual server.
- If you use NetScaler deployed in the cloud, you must make changes in the network. For example, allow communications between NetScaler and other components on certain ports. For details on the ports, see Communication ports.
- If you enable SSO on NetScaler Gateway, make sure that NetScaler communicates to StoreFront using a private IP address. You might have to add a StoreFront DNS record to NetScaler with a StoreFront private IP address.