HDX Adaptive transport with EDT support for Citrix Gateway service
Enlightened Data Transport (EDT) is a Citrix-proprietary transport protocol built on top of UDP. EDT delivers a superior user experience on challenging long-haul connections while maintaining server scalability. Adaptive Transport is a data transport mechanism for Citrix Virtual Apps and Desktops. Adaptive Transport provides the ability to use EDT as the transport protocol for ICA, and switch to TCP when EDT is not available. For more information on Adaptive Transport and EDT, see the Adaptive Transport documentation.
Prerequisites
- Citrix DaaS
- Virtual Delivery Agent (VDA) 2012 or later
- Citrix Workspace app
- Windows: version 1912 or later (2105 or later recommended)
- Linux: version 1912 or later (2104 or later recommended)
- Mac: version 1912 or later
- iOS: latest version available in the Apple App Store
- Android: latest version available in Google Play
- UDP port 443 must be allowed for outbound traffic from VDA to Citrix Gateway service
- The rendezvous protocol must be enabled and working. For details, see the Rendezvous Protocol documentation.
- Ensure that Adaptive Transport is enabled. For details, see the Adaptive Transport setting documentation.
- For more information on Adaptive Transport and EDT, see the Adaptive Transport documentation.
Considerations
The following are some of the considerations for using EDT with the Citrix Gateway service.
-
It is highly recommended to enable EDT MTU Discovery. For details, see the Adaptive Transport documentation.
-
EDT with Citrix Gateway service is only available when using Rendezvous. If HDX sessions are being proxied through the Cloud Connector, only TCP is available for data transport.
-
When an EDT session establishment fails the session falls back to TCP, causing an increase in the session launch time.
-
If you want to continue to proxy HDX™ sessions through the Cloud Connector, consider disabling Adaptive Transport via the Citrix Studio policy to avoid the potential increase in session launch times introduced by the fallback sequence.
-
Citrix recommends using EDT through the Citrix Gateway service only with VDAs running on Windows 10 and Windows Server 2019. There are limitations on Windows Server 2012 R2 and 2016 that do not allow for an MTU greater than 1024 for DTLS-encrypted sessions, which can affect the performance and user experience.
-
With Adaptive Transport, Citrix Gateway service does not Support UDP Audio.
Transport protocol validation
To know if your sessions are using EDT, refer to the following:
- Connection protocol in Citrix Director: https://support.citrix.com/article/CTX220730.
- After you launch an app or a desktop, go to Citrix Workspace app > Connection Center, select the appropriate session, click Properties, and look at the Transport encryption property. If it shows DTLS, the session is using EDT for transport. If it shows TLS, the session is using TCP for transport.
- If you launched a desktop, you can open a PowerShell or command prompt and run
“ctxsession -v”. The Transport Protocols property displays the connection method being used:- EDT Rendezvous: “UDP > DTLS > CGP > ICA®”
- TCP Rendezvous: “TCP > SSL > CGP > ICA”
- Proxy through Cloud Connector: “TCP > CGP > ICA”
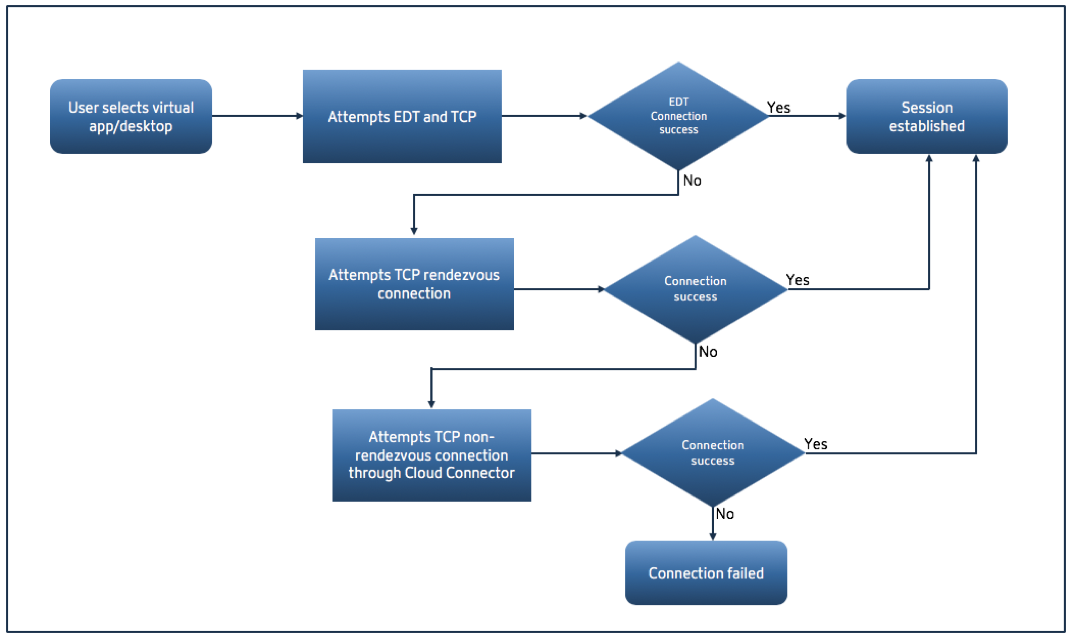
Connection fallback
If EDT negotiation fails for any reason, the session falls back to TCP with Rendezvous. And if that fails, then the session falls back to proxying through the Cloud Connectors.
EDT MTU discovery
It is highly recommended to enable EDT MTU Discovery to ensure that each session uses the optimal MTU for that connection.
In case EDT MTU Discovery is disabled or the user’s client does not support the feature, the EDT MTU is automatically set to 1380 to avoid fragmentation-related issues.
It is possible for users to connect via a network that requires an MTU lower than 1380, which is mostly seen with mobile networks (3G, 4G) or VPN connections. If this is the case in your environment, and the clients in use by the users do not support EDT MTU Discovery, Citrix recommends that you disable Adaptive Transport until the feature is available in your target client platform.
For more details on EDT MTU Discovery, see Adaptive Transport documentation.
Troubleshooting
The following provides some general troubleshooting guidance.
Sessions connect but are not using EDT:
- If the sessions are being proxied through the Cloud Connector, make sure that Rendezvous is enabled and that it works properly, as this is a pre-requisite for using EDT with the Citrix Gateway service. For details, see the Rendezvous documentation.
- If the sessions are using TCP Rendezvous:
- Make sure you are using VDA version 2012 or later.
- Check whether Adaptive Transport is enabled in Citrix policies.
- Make sure that the appropriate firewall rules are in place to open UDP 443 from the VDA machines to the Citrix Gateway service. For more details, see the Rendezvous](/en-us/citrix-virtual-apps-desktops-service/hdx/rendezvous-protocol.html) documentation.
- If there is a local firewall enabled in the VDA machine (for example Windows Defender Firewall), make sure that there are no rules blocking UDP 443.
- If using a proxy, only SOCKS5 proxies can be used to proxy EDT. For details, see the Rendezvous documentation.
Sessions connect with EDT but disconnect randomly after some time:
- Make sure you are using VDA version 2012 or later.
Session fails to connect:
- Make sure you are using VDA version 2012 or later.
- If using a client that supports EDT MTU Discovery, ensure that EDT MTU Discovery is enabled. This helps mitigate fragmentation-related issues. For details, see Adaptive Transport documentation.
-
If using a Linux or Android client:
- Check if Windows or Mac clients are working properly.
- Check if the CWA version is upgraded to Linux 2104, Android 21.5.0 or later.
- If you are using an older version of CWA then disable Adaptive Transport and ensure that TCP Rendezvous works properly.
- Once TCP Rendezvous works, if the session fails to connect after re-enabling Adaptive Transport, see the troubleshooting steps mentioned in step Sessions connect but are not using EDT > If the sessions are using TCP Rendezvous.