Rendezvous V1
When using the Citrix Gateway service, the Rendezvous protocol allows traffic to bypass the Citrix Cloud™ Connectors and connect directly and securely with the Citrix Cloud control plane.
There are two types of traffic to consider: 1) control traffic for VDA registration and session brokering; 2) HDX™ session traffic.
Rendezvous V1 allows for HDX session traffic to bypass Cloud Connectors, but it still requires Cloud Connectors to proxy all control traffic for VDA registration and session brokering.
Requirements
- Access to the environment using Citrix Workspace™ and Citrix Gateway service.
- Control Plane: Citrix DaaS (formerly Citrix Virtual Apps and Desktops™ service).
- Linux VDA Version 2112 or later.
- Version 2112 is the minimum required for no-transparent HTTP proxies.
- Version 2204 is the minimum required for transparent and SOCKS5 proxies.
- Enable the Rendezvous protocol in the Citrix policy. For more information, see Rendezvous protocol policy setting.
- The VDAs must have access to
https://*.nssvc.net, including all subdomains. If you can’t add all subdomains to the allow list in that manner, usehttps://*.c.nssvc.netandhttps://*.g.nssvc.netinstead. For more information, see the Internet Connectivity Requirements section of the Citrix Cloud documentation (under Virtual Apps and Desktop service) and the Knowledge Center article CTX270584. - Cloud Connectors must obtain the VDAs’ FQDNs when brokering a session. Accomplish this task in one of these two ways:
-
Enable DNS resolution for the site. Navigate to Full Configuration > Settings and turn on the Enable DNS resolution setting. Alternatively, use the Citrix Virtual Apps and Desktops Remote PowerShell SDK and run the command
Set-BrokerSite -DnsResolutionEnabled $true. For more information about the Citrix Virtual Apps and Desktops Remote PowerShell SDK, see SDKs and APIs. - DNS Reverse Lookup Zone with PTR records for the VDAs. If you choose this option, we recommend that you configure VDAs to always attempt to register PTR records. To do so, use the Group Policy Editor or Group Policy Object, navigate to Computer Configuration > Administrative Templates > Network > DNS Client, and set Register PTR Records to Enabled and Register. If the connection’s DNS suffix does not match the domain’s DNS suffix, you must also configure the Connection-specific DNS suffix setting for the machines to register PTR records successfully.
Note:
If using the DNS resolution option, the Cloud Connectors must be able to resolve the fully qualified domain names (FQDNs) of the VDA machines. In the case that internal users connect directly to the VDA machines, the client devices also must be able to resolve the VDA machines’ FQDNs.
If using a DNS reverse lookup zone, the FQDNs in the PTR records must match the FQDNs of the VDA machines. If the PTR record contains a different FQDN, the Rendezvous connection fails. For example, if the machine’s FQDN is
vda01.domain.net, the PTR record must containvda01.domain.net. A different FQDN such asvda01.sub.domain.netdoes not work. -
Enable DNS resolution for the site. Navigate to Full Configuration > Settings and turn on the Enable DNS resolution setting. Alternatively, use the Citrix Virtual Apps and Desktops Remote PowerShell SDK and run the command
Proxy configuration
The VDA supports establishing Rendezvous connections through HTTP and SOCKS5 proxies.
Proxy considerations
Consider the following when using proxies with Rendezvous:
-
Non-transparent HTTP proxies and SOCKS5 proxies are supported.
-
Packet decryption and inspection are not supported. Configure an exception so that the ICA® traffic between the VDA and the Gateway Service is not intercepted, decrypted, or inspected. Otherwise, the connection breaks.
-
HTTP proxies support machine-based authentication by using the Negotiate and Kerberos authentication protocols. When you connect to the proxy server, the Negotiate authentication scheme automatically selects the Kerberos protocol. Kerberos is the only scheme that the Linux VDA supports.
Note:
To use Kerberos, you must create the service principal name (SPN) for the proxy server and associate it with the proxy’s Active Directory account. The VDA generates the SPN in the format
HTTP/<proxyURL>when establishing a session, where the proxy URL is retrieved from the Rendezvous proxy policy setting. If you don’t create an SPN, authentication fails. - Authentication with a SOCKS5 proxy is not currently supported. If using a SOCKS5 proxy, you must configure an exception so that traffic destined to Gateway Service addresses (specified in the requirements) can bypass authentication.
- Only SOCKS5 proxies support data transport through EDT. For an HTTP proxy, use TCP as the transport protocol for ICA.
Transparent proxy
Transparent HTTP proxy is supported for Rendezvous. If using a transparent proxy in your network, no additional configuration is required on the VDA.
Non-transparent proxy
When using a non-transparent proxy in your network, configure the Rendezvous proxy configuration setting. When the setting is enabled, specify the HTTP or SOCKS5 proxy address for the VDA to know which proxy to use. For example:
- Proxy address:
http://<URL or IP>:<port>orsocks5://<URL or IP>:<port>
Rendezvous validation
If you meet all requirements, follow these steps to validate if Rendezvous is in use:
- Launch a terminal on the VDA.
- Run
/opt/Citrix/VDA/bin/ctxquery -f iP. - The TRANSPORT PROTOCOLS indicates the type of connection:
- TCP Rendezvous: TCP - TLS - CGP - ICA
- EDT Rendezvous: UDP - DTLS - CGP - ICA
- Proxy through Cloud Connector: TCP - PROXY - SSL - CGP - ICA or UDP - PROXY - DTLS - CGP - ICA
Tip:
If the VDA cannot reach the Citrix Gateway service directly with Rendezvous enabled, the VDA falls back to proxy the HDX session through the Cloud Connector.
How Rendezvous works
This diagram is an overview of the Rendezvous connection flow.
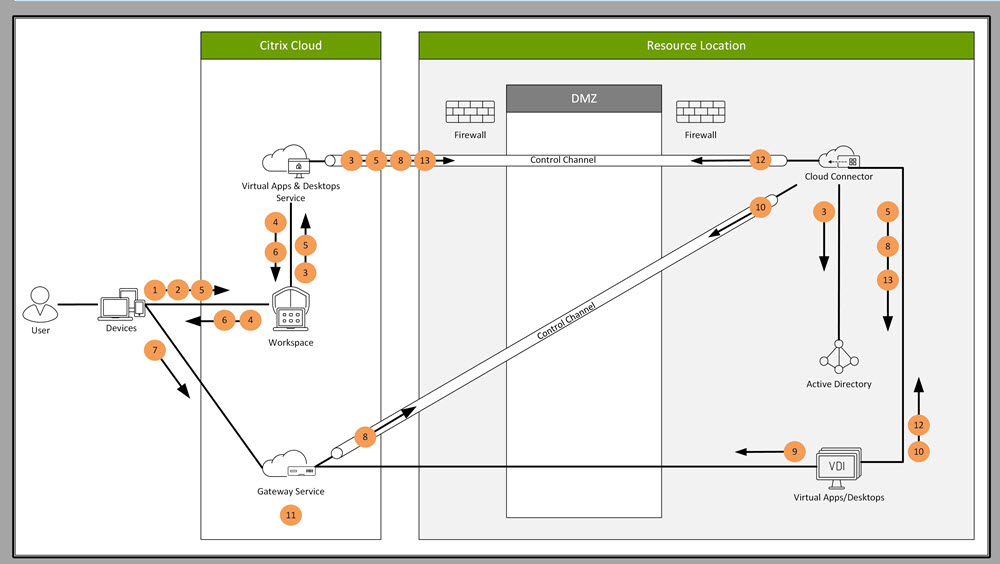
Follow the steps to understand the flow.
- Navigate to Citrix Workspace.
- Enter credentials in Citrix Workspace.
- If using on-premises Active Directory, Citrix DaaS™ authenticates credentials with Active Directory using the Cloud Connector channel.
- Citrix Workspace displays enumerated resources from Citrix DaaS.
- Select resources from Citrix Workspace. Citrix DaaS sends a message to the VDA to prepare for an incoming session.
- Citrix Workspace sends an ICA file to the endpoint that contains an STA ticket generated by Citrix Cloud.
- The endpoint connects to the Citrix Gateway service, provides the ticket to connect to the VDA, and Citrix Cloud validates the ticket.
- The Citrix Gateway service sends connection information to the Cloud Connector. The Cloud Connector determines if the connection is a Rendezvous connection and sends the information to the VDA.
- The VDA establishes a direct connection to the Citrix Gateway service.
- If a direct connection between the VDA and the Citrix Gateway service isn’t possible, the VDA proxies its connection over the Cloud Connector.
- The Citrix Gateway service establishes a connection between the endpoint device and the VDA.
- The VDA verifies its license with Citrix DaaS through the Cloud Connector.
- Citrix DaaS sends session policies to the VDA through the Cloud Connector. Those policies are applied.