App Protection features
This article highlights the App Protection features supported by Citrix Workspace app for Windows, Citrix Workspace app for Linux, and Citrix Workspace app for Mac.
Anti-keylogging
For Citrix Workspace™ app for Windows, Linux, and Mac
With encryption, App Protection’s anti-keylogging capabilities scramble the text the user is typing for both physical and on-screen keyboards. The anti-keylogging feature encrypts the text before any keylogging tool can access it from the kernel or OS level. A keylogger installed on the client endpoint reading the data from the OS or driver captures the hashed text instead of the keystrokes that the user is typing. App Protection policies are active not only for published applications and desktops, but for Citrix Workspace authentication dialogs as well. Your Citrix Workspace is protected from the moment when your users open the first authentication dialog. App Protection scrambles keystrokes, returning indecipherable text to key loggers.
The admins can choose to enable anti-keylogging for the following types resources:
- Virtual Apps and Desktops
- Internal web and SaaS apps
- Authentication screens
- Self-Service plug-in (SSP) screens
For Citrix Workspace app for iOS
This feature protects against keylogging attempts at the application level, ensuring that sensitive information entered into protected applications remains secure. This feature allows you to use only the Apple provided default keyboards ensuring that keystrokes entered into protected applications cannot be captured. App Protection prevents the usage of custom keyboards as part of the anti-keylogging feature. If you have enabled custom keyboards, you can disable them and then continue using the resources that are enabled using App Protection’s anti-keylogging feature.
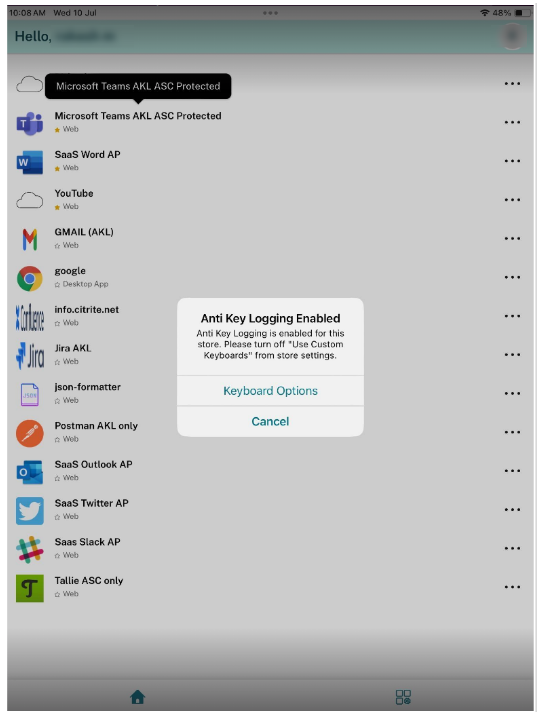
The admins can choose to enable anti-keylogging for the following:
- Virtual Apps and Desktops
- Web and SaaS apps opened through WebView
- Authentication screens
For more information about configuring the App Protection feature, see Configure App Protection.
Citrix Workspace app for Android
Starting from the 25.7.0 version, Citrix Workspace app for Android supports the App Protection Anti-Keylogging feature.
After anti-keylogging is enabled, the following restrictions apply:
-
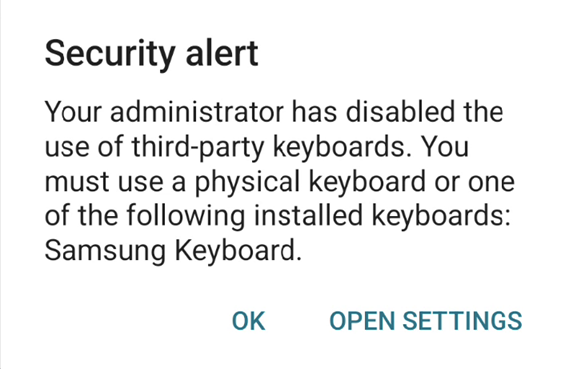
A user can’t use a non-OEM keyboard on anti-keylogging enabled resources. For example, a user has to use the Samsung Keyboard on a Samsung device. If a user is using a non-OEM software keyboard, then during launch of the resource, the keyboard gets blocked. The user can then continue with the launch and use a physical keyboard or must go to the settings and change the keyboard to the OEM keyboard.
-
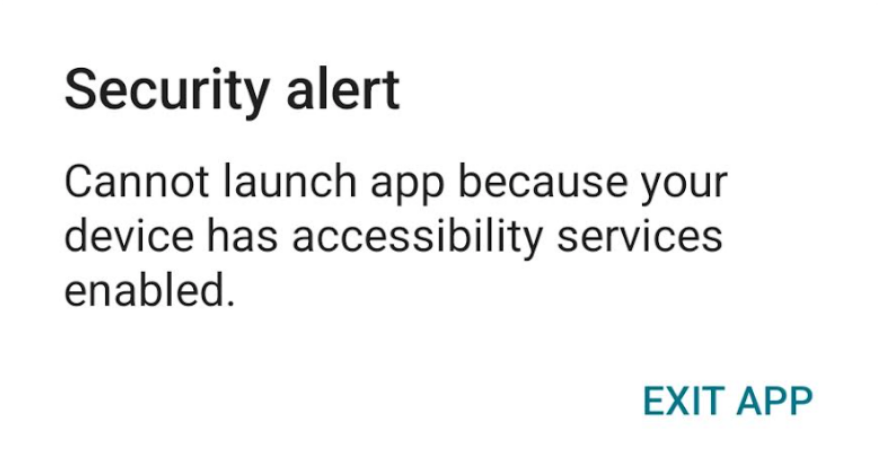
Accessibility service has to be disabled. In case accessibility service enabled, resource launch is blocked with the following error:
-
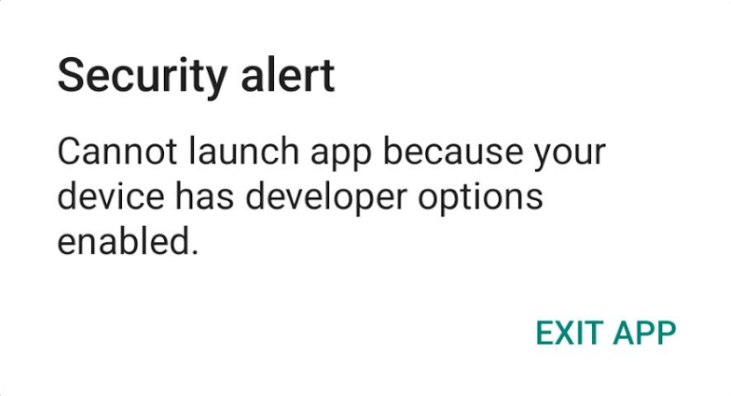
Developer mode has to be disabled. In case developer mode is enabled, launch is blocked with the following error:
Recommendations
Turn on Root detection. A rooted device significantly reduces the security posture of the end user. We recommend you to turn on the Root Detection feature. Click here for instructions.
Feature limitations
We do not support anti-keylogging on Custom Chrome Tab and Custom Portal. If you install the Citrix Workspace app on a managed device, the administrative app primarily governs its security. In this setup, the admin app retains comprehensive control over the device and might capture keystrokes even when Anti-Keylogging is enabled.
Earlier versions (prior to 25.7.0)
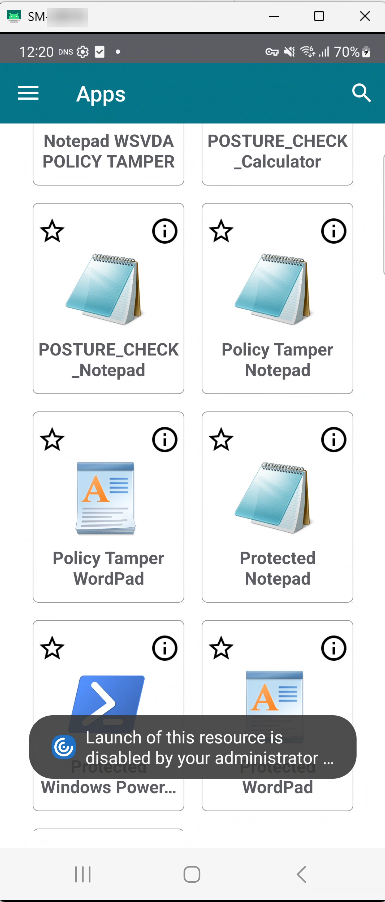
For Citrix Workspace app for Android versions prior to 25.7.0, the anti-keylogging feature is not supported. When you attempt to open an app with anti-keylogging enabled, the app fails to launch and displays the following error message:
“Launch of this resource is disabled by your administrator for security reasons”
Anti-screen capture
For Citrix Workspace app for Windows, Linux, and Mac
Anti-screen capture prevents an app from trying to take a screenshot or recording the screen within a virtual app or desktop session. The screen capture software can’t detect content within the capture region. The area selected by the app grays out, or the app captures nothing instead of the screen section that it expects to copy. The anti-screen capture feature applies to snip and sketch, Snipping Tool, and Shift+Ctrl+Print Screen on Windows.
Another use case for anti-screen capture is preventing sharing of sensitive data in a virtual meeting or web conferencing applications like GoToMeeting, Microsoft Teams, or Zoom. App Protection prevents unintended sharing by returning a blank screen in web conferences when apps are protected. This feature makes sure that the sensitive data isn’t accidentally leaked from the organization. This feature can help with compliance in regulated industries, as the intention is not considered when disclosing a data breach.
The admins can choose to enable anti-screen capture for the following types resources:
- Virtual Apps and Desktops
- Internal web and SaaS apps
- Authentication screens
- Self-Service plug-in (SSP) screens
Note:
If you have launched two virtual desktops where one virtual desktop is enabled with the Anti-screen capture feature and the other virtual desktop isn’t enabled with the Anti-screen capture feature, then the Anti-screen capture feature is applicable for both the virtual desktops. You can’t take the screenshot of either virtual desktops.
In case if you have minimized the virtual desktop that is enabled with Anti-screen capture, the Anti-screen capture feature is still applicable for the virtual desktop without the Anti-screen capture feature.
Screen capture detection and notification
For Citrix Workspace app for Windows, you can view a notification when a possible attempt of screen capture is made on any protected resources. For information on the resources protected by App Protection, see What does App Protection protect?
The notification appears when there is an:
- attempt to take a screenshot or record video through a screen-capturing tool.
-
attempt to take a screenshot through the Print Screen key.
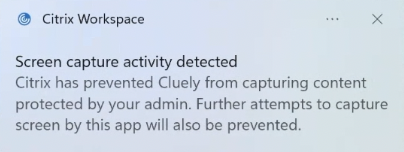
For steps to disable screen capture notifications, refer to the documentation Disable screen capture notifications.
Note:
The notification appears only once per running instance of the screen capture tool. The notification appears again if you relaunch the tool and try to capture the screen.
For Citrix Workspace app for iOS
Starting with the 24.9.0 version, Citrix Workspace app for iOS supports the anti-screen capture feature. App Protection prevents exfiltration of confidential information such as user credentials and sensitive information that is displayed on the screen. The feature prevents users and attackers from taking screenshots and from using keyloggers to glean and exploit sensitive information.
The anti-screen capture is supported on both single and multi-monitor scenarios. To enable the feature, perform the configuration steps mentioned at the Configuration section.
The admins can choose to enable anti-screen capture for the following:
- Virtual Apps and Desktops
- Web and SaaS apps opened through WebView
- Authentication screens
Anti-screen capture support
This feature prevents unauthorized screen captures, recordings, QuickTime screen mirroring, screen sharing, and app switching. Anti-screen capture feature is available for authentication screen, web or SaaS apps, and Citrix Virtual Apps and Desktops. When you capture a screen, a custom message Screen Capture is disabled by your administrator for security reasons is shown in the capture media instead of the actual content displayed on the screen. Anti-screen capture protects against various forms of unauthorized screen access such as:
- Screenshot: Prevents screenshots from being taken.
- Screen recording: Blocks screen recording software.
- Screen mirroring: Disables mirroring of the screen to other devices.
- Screen share: Restricts screen sharing functionality.
-
App switcher: Prevents sensitive information from being visible in app switcher previews.

Behavior of Resources with Anti-Screen Capture Enabled in Multi-Monitor Setups
Multi-monitor mode refers to the configuration in which an iOS or iPadOS device is connected to an external display, allowing the device to use multiple screens simultaneously.
There are three modes supported:
- Mirror: Duplicates the iPad display on the connected external monitor.
- Presentation: Projects the desktop interface to the external monitor while the iPad screen functions as a trackpad.
- Extend: Enables different content to be shown on each display, allowing for independent views across the iPad and the external monitor.
Virtual Apps and Desktops: The user sees the virtual app or desktop on the external monitor, depending on the selected display mode. When the user attempts to take a screenshot, the content on all screens is protected.
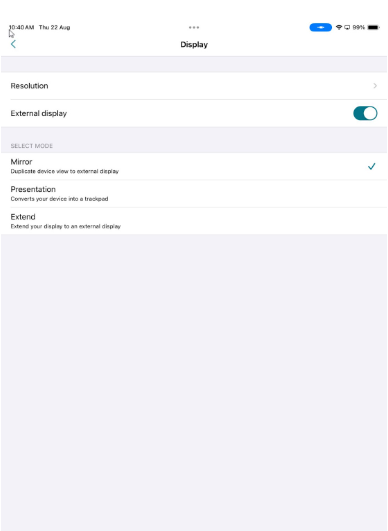
Authentication Screens, web or SaaS apps: On the external monitor, the user sees the following screen instead of the actual authentication screen, web or SaaS apps.

In all scenarios, when the user tries to capture a screenshot of an anti-screen capture enabled resource will be blocked.
For Citrix Workspace app for Android
This feature restricts the ability of clients to be compromised by screen capturing malware. Also, prevents unauthorized screen captures, recordings, mirroring, screen sharing, and app switching.
Anti-screen capture feature is available for authentication processes, web or SaaS apps, and Citrix Virtual Apps and Desktops. Citrix Workspace app for Android doesn’t allow you to take screenshots. When you try to capture a screen, you get a prompt that you are not allowed to take screenshots.
The admins can choose to enable anti-screen capture for the following:
- Virtual Apps and Desktops
- Web and SaaS apps
- Authentication screens
Starting with the Citrix Workspace app for Android 24.7.0 version, the anti-screen capture feature is available by default. However, to enable the feature, perform the configuration steps mentioned at the Configuration section.
Limitations:
-
The App Protection policies are downloaded for each store. If a store has the policies downloaded and you are moving to another store for which the policies aren’t downloaded, the anti-screen capture feature isn’t protected in the new store.
-
The anti-screen capture feature is not supported on the authentication screens when ChromeCustomTab is used. However, this feature is supported when using native authentication or WebView. The ChromeCustomTab is enabled by default on the Cloud stores and you can change it to WebView by changing the AndroidWebViewType to webview using the PowerShell module. For more information, see Set-WorkspaceCustomConfigurations.
Anti-DLL Injection
The Anti-DLL Injection security enhancement helps protect the Citrix Workspace app from certain unauthorized dynamic-link libraries (DLL) or untrusted modules. If such untrusted modules are injected, the Citrix Workspace app detects these interventions and stops the modules from loading. Also, if any untrusted or malicious DLL is detected before the session launch, App Protection blocks the session launch and displays an error message. Closing the error message exits the virtual app and desktop session.
This feature is applicable for all protected virtual apps and desktops and the Citrix Workspace app authentication window (on-premises deployment/StoreFront).
This enhancement exits the session immediately when certain untrusted or malicious DLLs exist on the protected component.
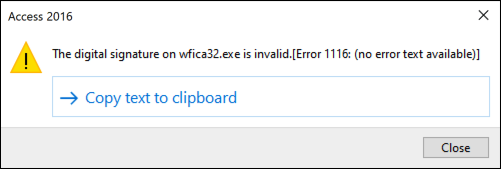
The enhancement displays a notification when an untrusted or malicious DLL is blocked. Closing the message exits the virtual app and desktop session.
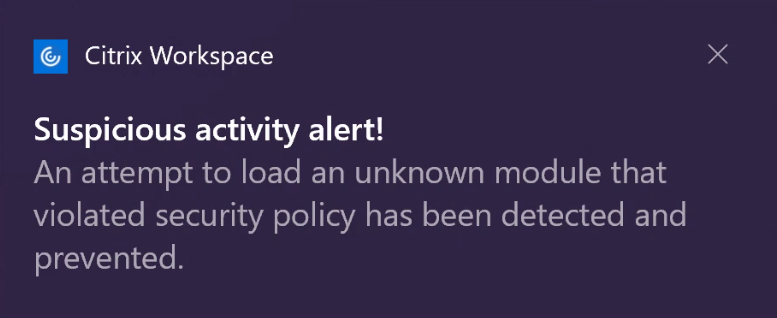
Disclaimer: This capability works by filtering access to required functions of the underlying operating system (specific API calls required to load DLLs). Doing so means that it can provide protection even against certain custom and purpose-built hacker tools. However, as operating systems evolve, new ways of loading DLLs can emerge. While we continue to identify and address them, we cannot guarantee full protection in specific configurations and deployments.
This feature support Citrix Workspace app for Windows version 2206 and later.
Compatibility with HDX™ optimization for Microsoft Teams
Optimized Microsoft Teams supports screen sharing when Citrix Workspace app is enabled with App Protection in the Desktop Viewer mode only. When you click Share content in Microsoft Teams, the screen picker provides the following options:
- Window option to share any open app - This option is displayed only if the VDA version is 2109 or later.
-
Desktop option to share the contents on your VDA desktop - This option is displayed only for the following versions of Citrix Workspace app:
- Citrix Workspace app for Linux version 2311 or later
- Citrix Workspace app for Mac version 2308 or later
- Citrix Workspace app for Windows version 2309 or later
Note:
For Citrix Workspace app for Linux, the Desktop share option is disabled by default. To enable it, add the
UseGbufferScreenSharingparameter in your config.json file as follows:mkdir -p /var/.config/citrix/hdx_rtc_engine vim /var/.config/citrix/hdx_rtc_engine/config.json { "UseGbufferScreenSharing":1 } <!--NeedCopy-->
Optimized Microsoft Teams enabled with App Protection also supports the Citrix virtual monitor layout which allows you to share each virtual monitor individually.
Limitation:
- Optimized Microsoft Teams enabled with App Protection doesn’t support screen sharing on Published Desktops enabled with Local App Access (LAA).
- Client-rendered content such as Browser content using BCR cannot be captured or shared. If you try to screen capture, it is displayed as a black screen.
Note:
For Citrix Workspace app for Linux, this feature is in Technical Preview.
Local App Protection (Preview)
App Protection offers enhanced security to defend customers against keyloggers, and accidental and malicious screen capture at endpoints. Currently App Protection capabilities are only offered for Workspace resources. With this feature, App Protection capabilities are extended to local apps on endpoints. Starting with Citrix Workspace app 2210 for Windows, App Protection can be applied to local apps on Windows devices.
Register for the Preview of this feature using the Podio form.
Policy Tampering Detection
Policy Tampering Detection feature prevents the user from accessing the virtual app or desktop session if the App Protection anti-screen capture and anti-keylogging policies are tampered. If policy tampering is detected, then the virtual app or desktop session is terminated.
Note:
The policy Tampering Detection feature will be enabled by default from Citrix Virtual Apps and Desktops (CVAD) version 2511 onwards.
From CVAD 2511, session launches will fail if you are enabling App Protection using the
Default.icafile. Instead, enable the policies on the delivery group from the Desktop Delivery Controller (DDC) using Web Studio or PowerShell. For more information, see Configure anti-keylogging and anti-screen capture.
To configure Policy Tampering Detection, see Configure Policy tampering detection.
Posture Check
To detect and block launching virtual apps and desktops that are enabled with App Protection policies from Citrix Workspace app versions that do not support the Policy Tampering Detection feature, enable App Protection Posture Check.
Note:
If Posture Check is enabled and you are using the Citrix Workspace app version that does not support Posture Check, then the sessions enabled with App Protection policies are terminated.
To configure Posture Check, see Configure Posture Check.
Limitation:
Posture Check stops working intermittently when you are using Windows Workstation VDAs hosted on Microsoft Azure with VDA 2308. This limitation is resolved in VDA version 2311 and later.
App Protection support for double-hop scenario
Starting with the Citrix Workspace app for Windows 2405 version, App Protection is supported for the double-hop scenario when installed on a workstation VDA (such as Windows 10 or Windows 11) for a single-session VDA.
Double-hop indicates a scenario where a Citrix Virtual App or Virtual Desktop session is running within a Citrix Virtual Desktop session. For more information, see Double-hop in Citrix Virtual Apps and Desktops.
The following image describes the double-hop scenario:
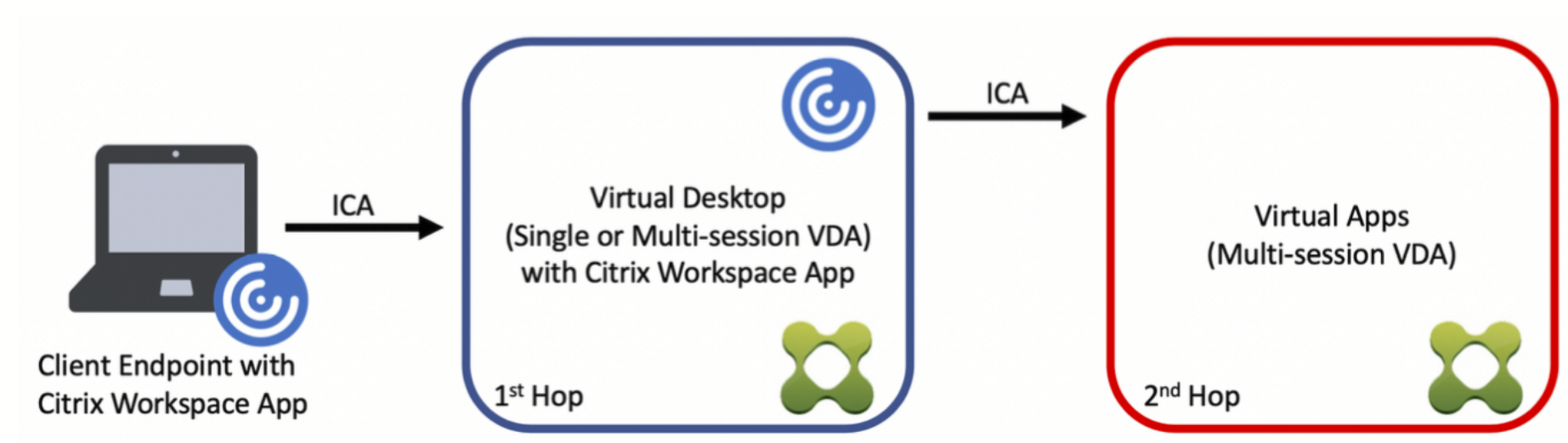
App Protection with double-hop means that the App Protection policies are enabled on the virtual apps and desktops that are opened from the first hop.
The first hop where the App Protection feature is enabled and from where you are opening the protected virtual apps or desktops can only be single-session OS VDA.
The following are the expected behaviors for App Protection with double-hop in multi-session OS VDA and single-session VDA:
App Protection in multi-session OS VDA
App Protection isn’t supported in a multi-session OS VDA (such as Windows Server 2k19 or Windows Server 2k22). Hence, App Protection won’t be installed in such machines.
You can install Citrix Workspace app without App Protection on a multi-session OS. However, resources that are enabled with App Protection policies don’t enumerate and cannot be opened in a multi-session OS VDA.
App Protection in Single Session OS VDA
With the Citrix Workspace app for Windows 2405 version, the App Protection features are supported when installed on a workstation VDA (such as Windows 10 or Windows 11).
The following features are currently supported:
Limitations:
App Protection in Single Session Pooled VDA
Since App Protection has drivers, the Admin must perform operations such as Citrix Workspace app Upgrade and Uninstall that need a reboot on the base image.
If the operations are carried out by the end user with admin privileges within the pooled session, it is not persisted to the base image and the machine might go into an inconsistent state.
Launching AntiScreencapture enabled resources in Double Hop is not supported when Display Capture is configured to use DDAPI (Display Device API).
What scenario is supported?
When the second hop virtual app or desktop enabled with anti-screen capture and anti-keylogging is opened within the first hop virtual desktop session, it is protected from screen capture and keylogging tools that are running within the first hop virtual desktop session.
What scenario is not supported?
-
If the first hop virtual desktop doesn’t have App Protection policies enabled, it is possible for screen capture and keylogging tools installed on the client endpoint to capture screens or keystrokes even when the second hop has App Protection policies enabled.
-
If the end user is accessing the first hop machine using an RDP session, App Protection for the second hop isn’t supported.
This feature is enabled by default. Therefore needs no separate configuration. The admin needs to configure the App Protection policies for the resources.
Recommendation for end-to-end protection
To have end-to-end protection, it is recommended to enable App Protection policies on each hop (both first and second). This way, keylogging, and screen capture tools running either on the client or the first hop isn’t able to capture the sensitive content of the second hop session.
Block double-hop launch
App Protection features aren’t supported in a double-hop scenario when using the Citrix Workspace app for Windows versions older than 2405. You are allowed to open virtual apps, desktops, web apps, or SaaS apps that are enabled with App Protection policies in a double-hop scenario. However, the App Protection features are not applied.
You can block the opening of virtual apps, desktops, web apps, or SaaS apps enabled with the App Protection feature in a double-hop scenario.
For more information about enabling the Block Double-hop Launch setting, see Enable Block Double-Hop Launch setting.
Citrix Analytics Service for App Protection
When you use Citrix Virtual Apps and Desktops, user events corresponding to their activities and actions are generated. Citrix Analytics for Security has a feature named Self-service search that records those user events and provides you the insights about them. Self-service search enables you to find, filter, and explore those user events so that you can understand what user event is done and act depending on the severity of the event. For more information about Self-service search, see Self-service search.
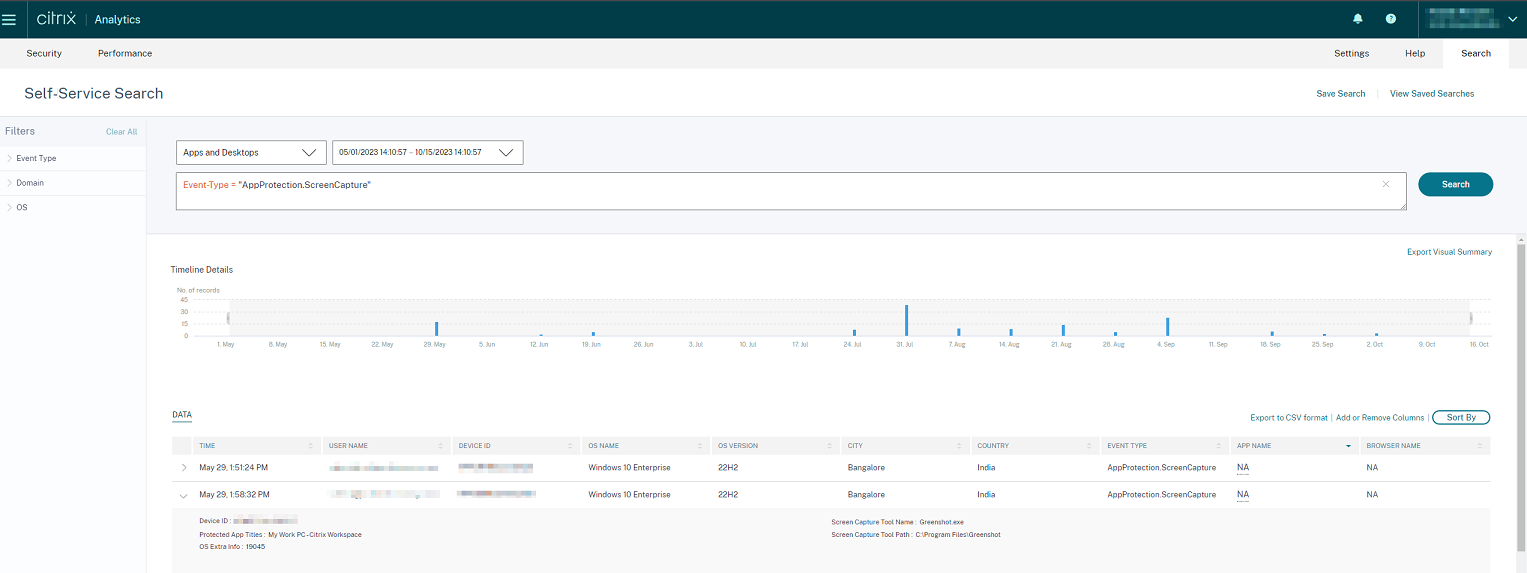
Self-service search for Apps and Desktops has an event type AppProtection.ScreenCapture that allows you to determine if any attempts are made to take screenshots of the virtual apps or desktops that are enabled with App Protection policies. For more information about how to search for a user event, see Specify search query to filter events.
This service provides the following information:
- Device ID
- Protected App Titles
- OS Extra Info
- Screen Capture Tool Name
- Screen Capture Tool Path
Screen Capture Allow List
If Citrix Workspace app, virtual apps and desktops, or SaaS apps are enabled with the App Protection Anti-screen capture policy, then you can’t capture their screens using any screen-capturing tool.
However, starting from the Citrix Workspace app for Windows 2402 release, the Screen Capture Allow List feature enables you to add an app to the screen capture allow list. This feature enables you to use the allow listed app and capture the screen of the resource enabled with the App Protection Anti-screen capture policy. To add an app to the screen capture allow list, see Configure the Screen Capture Allow List.
Important:
It isn’t recommended to run an allow-listed app on your device for a longer period because it decreases the security posture. You can use the allow-listed apps for sharing your screen temporarily during scenarios such as troubleshooting. It is recommended to adhere to the following conditions:
- Run the allow-listed app for a short period along with the resource enabled with the App Protection Anti-screen capture feature.
- Terminate the allow-listed app immediately after the required task is completed.
- Add a watermark when sharing the screen while using the resource enabled with the App Protection Anti-screen capture feature for more security.
Screen capture allow list needs to be configured in GACS. The feature is compatible with both on-premises and Cloud environments, provided GACS is configured.
Process exclusion list
When you launch any process or application on your device, App Protection DLLs are injected into each process if the App Protection is enabled. Sometimes, this might cause the process or application not to work due to compatibility issues with the DLL.
Starting from the Citrix Workspace app for Windows 2402 release, you can add any process to the Process exclusion list to avoid the injection of the App Protection DLL into that particular process and recover from any compatibility issues caused by the presence of App Protection DLLs. To configure the Process exclusion list, see Configure Process exclusion list.
Important:
It’s not recommended to exclude processes as it decreases the security posture. You can use this to temporarily unblock the usage of the application and raise a support ticket for further investigation.
Process exclusion list needs to be configured in GACS. The feature is compatible with both on-premises and Cloud environments, provided GACS is configured.
USB Filter Driver Exclusion List
Important:
USB filter driver exclusion list needs to be configured in GACS. The feature is compatible with both on-premises and Cloud environments, provided GACS is configured.
Sometimes, when you’re using specialized external keyboards such as gaming keyboards with the Citrix Workspace app, the App Protection USB Filter Driver might cause compatibility issues and block you from using the keyboard.
Starting from the Citrix Workspace app for Windows 2402 release, the USB Filter Driver Exclusion List feature allows you to exclude any USB device that has compatibility issues with the Citrix Workspace app using the device Vendor ID and Product ID. To add any device to the USB Filter Driver Exclusion List, see Configure USB Filter Driver Exclusion List.
Note:
It isn’t recommended to exclude devices permanently. Use this feature to temporarily unblock the user from using the device and raise a support ticket to investigate the compatibility issue further.
Allow list for the apps which use LD_PRELOAD functionalities for Citrix Workspace app for Linux
App protection blocks the launch of a protected session if other apps using LD_PRELOAD are running. To allow legitimate apps, you can configure the allow list feature with admin approval. This feature is only for Citrix Workspace app for Linux.
To enable the feature, perform the configuration steps mentioned at the Configure allowlist LD_PRELOAD section.
In this article
- Anti-keylogging
- Anti-screen capture
- Anti-DLL Injection
- Compatibility with HDX™ optimization for Microsoft Teams
- Local App Protection (Preview)
- Policy Tampering Detection
- Posture Check
- App Protection support for double-hop scenario
- Citrix Analytics Service for App Protection
- Screen Capture Allow List
- Process exclusion list
- USB Filter Driver Exclusion List
- Allow list for the apps which use LD_PRELOAD functionalities for Citrix Workspace app for Linux