Manage and monitor remote isolated browsers
You can now manage, monitor, and check usage of the published browsers in Remote Browser Isolation.
Manage
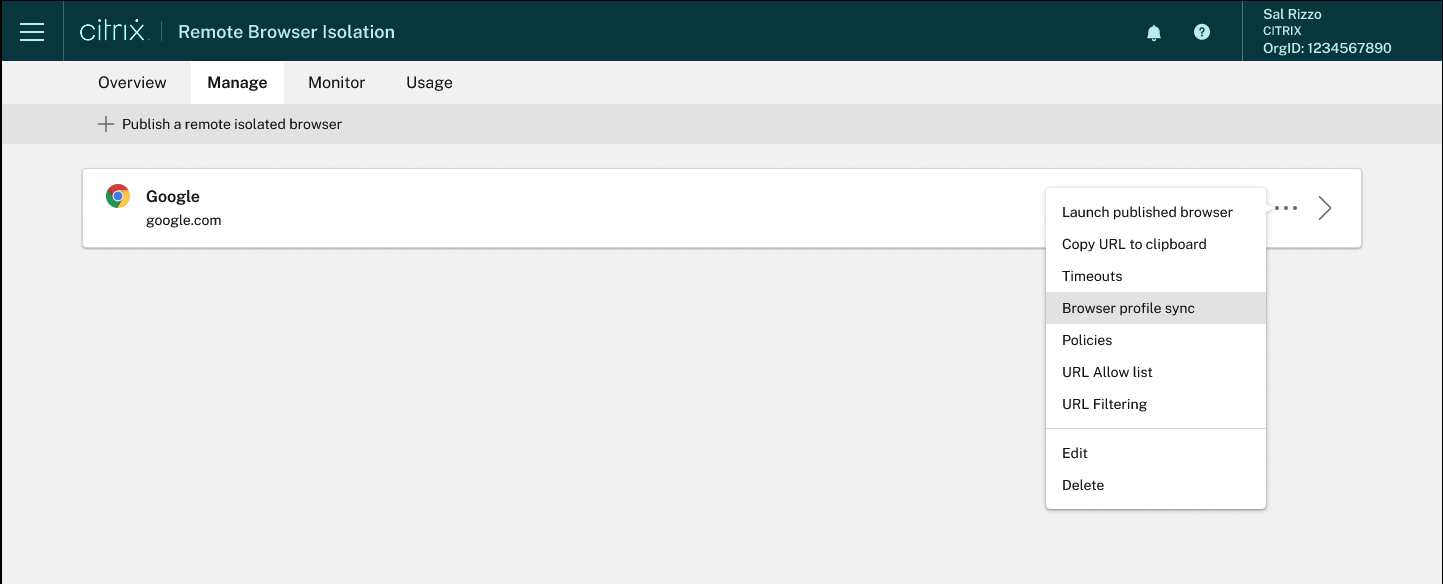
The Manage tab lists the published browsers. To access management tasks, click the ellipsis at the right-end of the published browser, and then select the required task.
If you select a menu entry, and then decide not to change anything, cancel the selection by clicking the X outside the dialog box.
You can manage the published isolated browser using the following tasks:
-
Launch published browser: Opens the published browser session. After publishing the browser, you can select this task to verify the launch of the published browser session.
-
Copy URL to clipboard: Copies the URL of the published browser. You can share this URL with end users to access the published browsers.
-
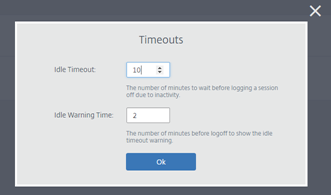
Timeouts: You can set the Idle timeout and Idle Warning time by selecting the Timeouts task.
- Idle Timeout: The number of minutes a session can stay idle before it’s ended due to inactivity.
- Idle Warning Time: The number of minutes before ending a session that a warning message is sent to the user.
For example, if you set Idle Timeout to 20 and Idle Warning Time to 5, the system will display a warning message if there is no activity in the session for 15 minutes. If the user does not respond, the session ends five minutes later.
To set Idle timeout and Idle Warning time of the published isolated browser, select the Timeouts task and set the time for Idle Timeout and Idle Warning time in the Timeouts dialog box. Then, click OK to save the changes.
-
Policies: You can set policies for the published browsers.
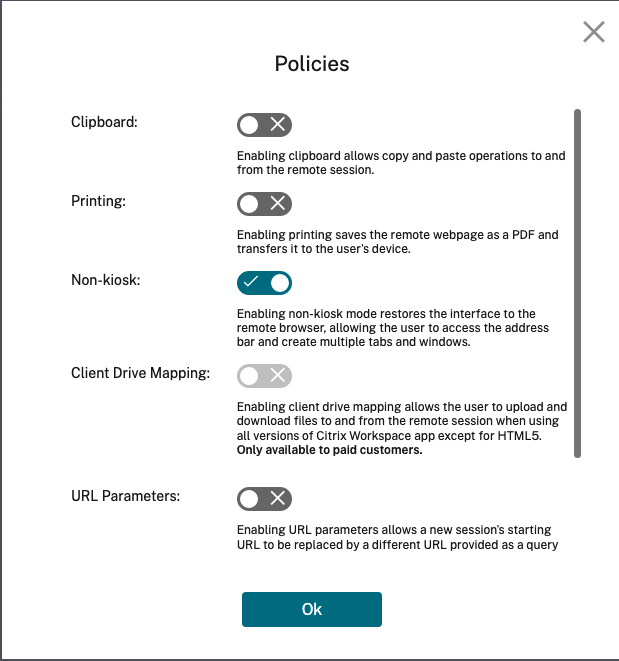
Settings on the policies page control the following:
- Clipboard: Enabling the Clipboard policy allows copy and paste operations to and from the remote session. (Disabling the Clipboard policy removes the Clipboard button from the Citrix Workspace™ app toolbar.) By default, this setting is disabled.
- Printing: Enabling printing saves the remote webpage as a PDF and transfers it to the user’s device. The user can then press Ctrl-P and select the Citrix PDF printer. By default, this setting is disabled.
- Non-kiosk: Enabling non-kiosk mode restores the interface to the remote browser. The user can then access the address bar and create multiple tabs and windows. (Disabling non-kiosk mode removes the remote browser’s navigation controls and address bar.) By default, this setting is enabled (non-kiosk mode is on).
- Region failover: The Region failover policy automatically transfers your published browser to a different region if your current region is reporting an issue. To opt out, disable the Region failover policy. If you published the browser using the Auto region selection, your isolated browser remains enrolled in the policy. By default, this setting is enabled.
-
Client drive mapping: Enabling the Client drive mapping policy allows the user to upload and download files to and from the remote session. This feature is available only for sessions launched with the Citrix Workspace app. By default, this setting is disabled.
- Users must save downloaded files only on the
ctxmntdisk in theAnonxxxdirectory. To do that, users must navigate to the desired location for storing the file. For example, Anonxxx > ctxmnt > C > Users > User Name > Documents.
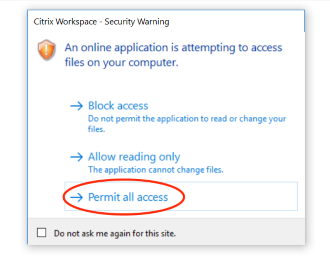
- The dialog box might prompt the user to accept the Permit all access or Read and Write permissions to access the
ctxmntfolder.
- Users must save downloaded files only on the
- URL parameters: Enabling URL parameters allows you to change a new session’s starting URL when users launch an app. For this policy to take effect, configure a local proxy server to identify suspicious websites and redirect them to Remote Browser Isolation. By default, this setting is disabled. For more information, see Proof of Concept Guide: URL Redirection to Remote Browser Isolation with Citrix ADC in Azure.
- Hostname tracking: Use host name tracking to enable Remote Browser Isolation to log host names during a user’s session. This policy is disabled by default. This information is shared with Citrix Analytics. For more information, see Citrix Analytics.
When you’re done, click OK.
-
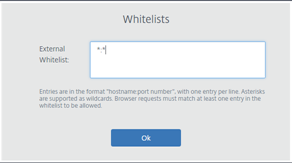
URL Allow lists: Use the Whitelists task to restrict users to visiting only allowed URLs within their published Remote Browser Isolation session. This feature is available for external authenticated web apps.
Enter allow list entries in the form
hostname:port number. Specify each entry on a new line. Asterisks are supported as wildcards. Browser requests must match at least one entry in the allow list.For example, to set
https://example.comas an allowed URL:-
example.com:*allows connection to this URL from any port. -
example.com:80allows connection to this URL only from port 80. -
*:*allows access to this URL from any port and from any links to other URLs and ports. The*.*format allows access to all external web apps from the published app. This format is the default setting for the web apps External Whitelist field.
When you’re done, click OK.
Advanced web filtering capabilities are available through integration with the Access Control service. Learn more at Use case: Selective access to apps.
-
-
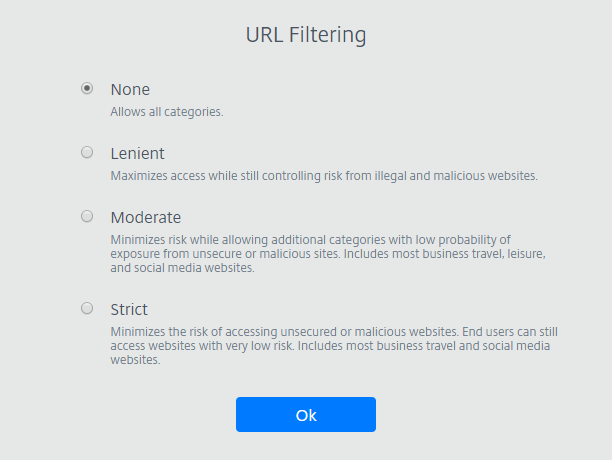
URL filtering: You can configure URL filtering to control access methods based on pre-defined categories associated with risk models. URL filtering options include:
-
None - Allows all categories.
-
Lenient - Maximizes access while still controlling risk from illegal and malicious websites. Includes the following categories:
- Adult: Grotesque, sex education, porn, nudity, sexual services, adult search and links, swimsuits and lingerie, adult magazines and news, sexual expression (text), fetish, and dating.
- Computing and Internet: remote proxies, private IP addresses, peer-to-peer file sharing, and torrents.
- Gambling: Sweepstakes, prizes, lotteries, and gambling in general.
- Illegal and harmful: Terrorism, extremism, hate, slander, weapons, violence, suicide, illegal drugs, medication, illegal activities, marijuana, and advocacy in general.
- Malware and spam: Hacking, malware, spam, spyware, botnets, infected sites, phishing sites, keyloggers, mobile malware, phone bots, malicious and dangerous websites.
-
Moderate - Minimizes risk while allowing more categories with low probability of exposure from unsecure or malicious sites. Includes the following categories:
- Adult: Grotesque, sex education, porn, nudity, sexual services, adult search and links, swimsuits and lingerie, adult magazines and news, sexual expression (text), fetish, and dating.
- Business and industry: Auctions.
- Computing and Internet: Advertisements, banners, remote proxies, private IP addresses, peer-to-peer file sharing, and torrents.
- Downloads: Mobile app stores, storage services, downloads, and program downloads.
- Email: Web-based mail and email subscriptions.
- Finance: Cryptocurrency.
- Gambling: Sweepstakes, prizes, lotteries, and gambling in general.
- Malware and spam: Hacking, malware, spam, spyware, botnets, infected sites, phishing sites, keyloggers, mobile malware, phone bots, malicious and dangerous websites.
- Messaging, chat, and telephony: Instant messages and web-based chat.
- News, entertainment, and society: Wordpress (posts and uploads), unsupported URLs, occult, no content, miscellaneous, horoscope, astrology, fortune telling, drinking, religions, personal webpages, blogs, and online games.
- Social networking: Photo search and sharing sites, IT bulletin boards, and bulletin boards.
-
Strict - Minimizes the risk of accessing unsecured or malicious websites. End users can still access websites with low risk. Includes the following categories:
- Adult: Grotesque, sex education, porn, nudity, sexual services, adult search and links, swimsuits and lingerie, adult magazines and news, sexual expression (text), fetish, and dating.
- Business and industry: Auctions.
- Computing and Internet: Advertisements, banners, dynamic DNS, mobile apps, publishers, parked domains, remote proxies, private IP addresses, peer-to-peer file sharing, and torrents.
- Downloads: Mobile app stores, storage services, downloads, and program downloads.
- Email: Web-based mail and email subscriptions.
- Finance: Cryptocurrency and financial products.
- Gambling: Sweepstakes, prizes, lotteries, and gambling in general.
- Illegal and harmful: Terrorism, extremism, hate, slander, weapons, violence, suicide, illegal drugs, medication, illegal activities, marijuana, and advocacy in general.
- Jobs and resumes: Employment, career advancement, and LinkedIn (updates, mail, connections, and jobs).
- Malware and spam: Hacking, malware, spam, spyware, botnets, infected sites, phishing sites, keyloggers, mobile malware, phone bots, malicious and dangerous websites.
- Messaging, chat, and telephony: Instant messages and web-based chat.
- News, entertainment, and society: Wordpress (posts and uploads), accommodations, travel and tourism, unsupported URLs, politics, fashion and beauty, arts and cultural events, reference, recreation and hobbies, local communities, miscellaneous, drinking, popular topics, special events, news, society and culture, online magazines, online games, life events, occult, no content, horoscope, astrology, fortune telling, celebrity, streaming media, entertainment, venues, activities, personal webpages and blogs, and religions.
- Social networking: Social networks in general, YikYak (posts), Twitter (posts, mail, and follows), Vine (uploads, comments, and messages), Google+ (photo and video uploads, posts, video chat, and comments), Instagram (uploads and comments), YouTube (shares and comments), Facebook (groups, games, questions, video upload, photo uploads, events, chat, apps, posts, comments, and friends), Tumblr (posts, comments, photo, and video uploads), Pinterest (pins and comments), IT bulletin boards, and bulletin boards.
When you’re done, click Ok.
-
-
Edit: You can use the Edit task to change the name, start URL, region of a published browser, or the passcode. When you’re done, click Publish.
-
Delete: You can use the Delete task to remove a published isolated browser. When you select this task, you’re prompted to confirm the deletion.
Monitor
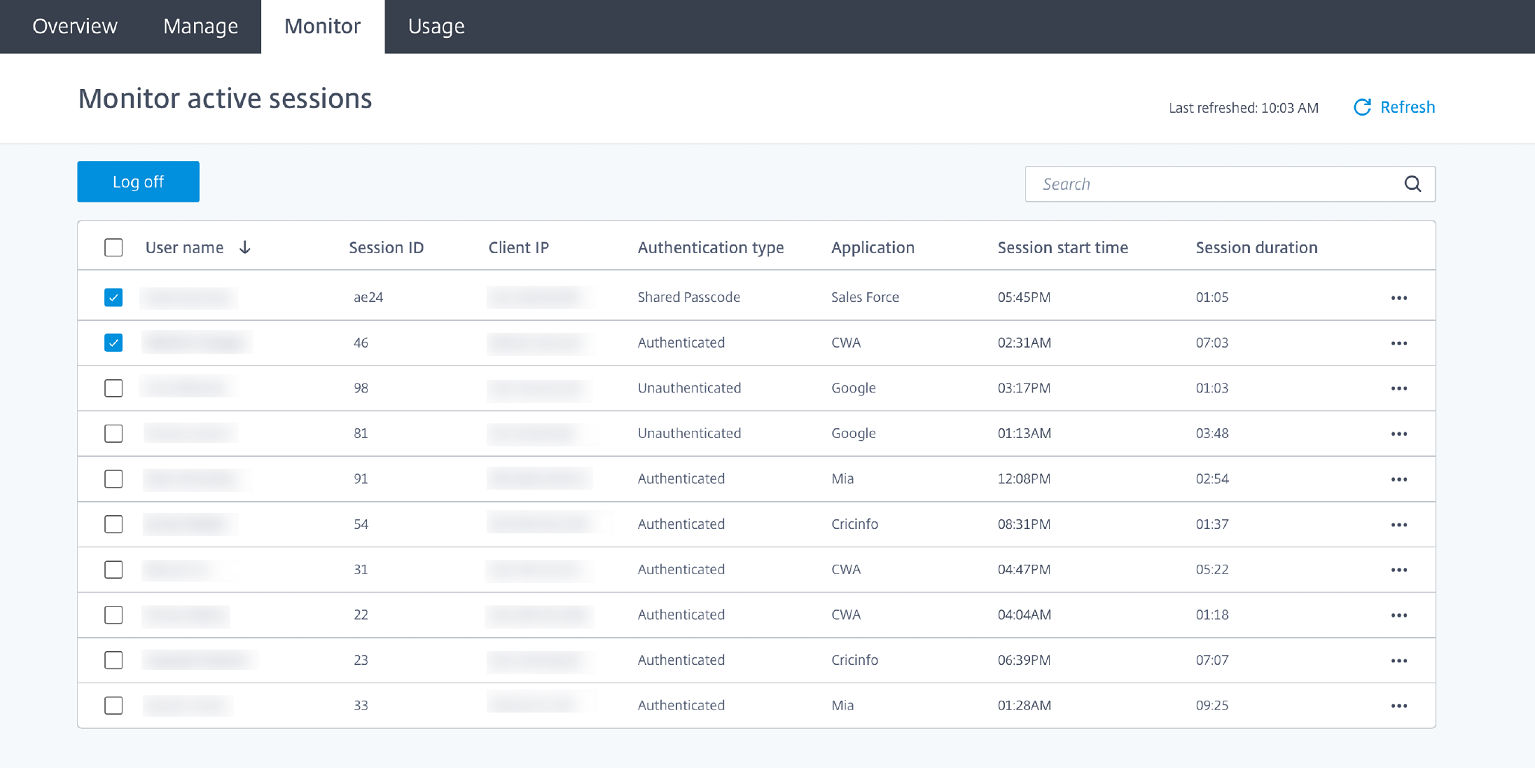
The Monitor tab provides information about users’ real-time sessions. You can monitor and disconnect one or several active sessions.
To stop a single session, select the session and click the ellipsis menu at the end of an entry’s row. Click Log off session and confirm your changes.
To disconnect multiple sessions, select the active sessions in the list and click the Log off button on the top of the page. After you confirm your changes, Remote Browser Isolation immediately disconnects all selected sessions.
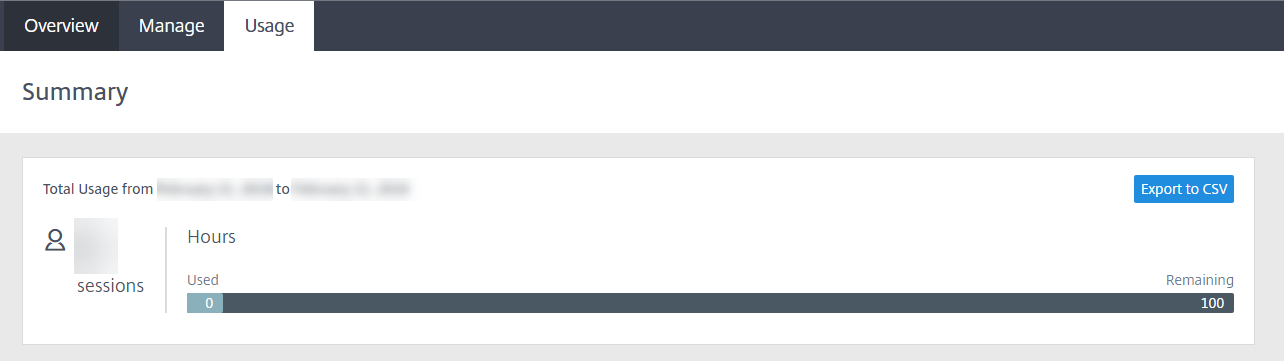
Usage
The Usage tab shows the number of initiated sessions and the number of hours used.
To create a spreadsheet containing usage details, click Export to CSV and select a timeframe.